
- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
The content you are looking for has been archived. View related content below.

Special shoutout to Cyber Elite @reaper for his contribution to this blog!
You wouldn't leave your front door open. So why would you leave your firewall wide open?
With just a few simple actions you can make your environment more secure. That being said, you'll be amazed at how many administrators skip the 'hardening the operating system' part of a firewall deployment.
In my years working for support, I was shocked at how many times I was able to log into a customer's firewall without asking for credentials: simply because they never bothered to change the default password!
The worst scenario I ever encountered (well maybe not worst, but still pretty bad) was an administrator that was still using the good old admin/admin. An enterprising user had discovered the management interface, had been able to log in and create security policies for himself so he could access all the things he wanted from his work computer.
Suffice to say many of the newly acquired privileges were not work related.
First, set up every administrator with a personalized account. This will come in handy when a change in the configuration needs to be back-traced in case something is unclear or was not documented properly. You can verify which configuration changes were configured by which administrator in the configuration log located at Monitor > Logs > Configuration. Having 20 administrators using the same admin account isn't going to help you track who configured what.
Next, change the default administrator account. Never keep the default password; create a new strong password for the default admin account is best practice regardless of the platform you're working on.
Alternatively you can simply delete the default admin account.
NOTE: An administrator can NOT delete his own account. You'll need to create a different account first and delete the default admin account using the newly created account.
As displayed below you'll see different types of administrators using different types of authentication and different roles depending on their permission set. Note that the default 'admin' account has been deleted.
Some admins require less access, the operations team may only need to have monitoring up on a big screen or may only need to review certain settings. Some admins may not be allowed access to private data like usernames or IP addresses. All this can be controlled through an admin role that's attached to the admin's account: Web interface for Admin Roles Device Tab with Admin Role Profile window open.

If possible, make sure the management interface is in an isolated network segment not accessible to unauthorized people. If a traditional 'out-of-band' network is not possible, consider adding an access list to the management configuration to limit access to administrator's subnet or individual IP addresses.
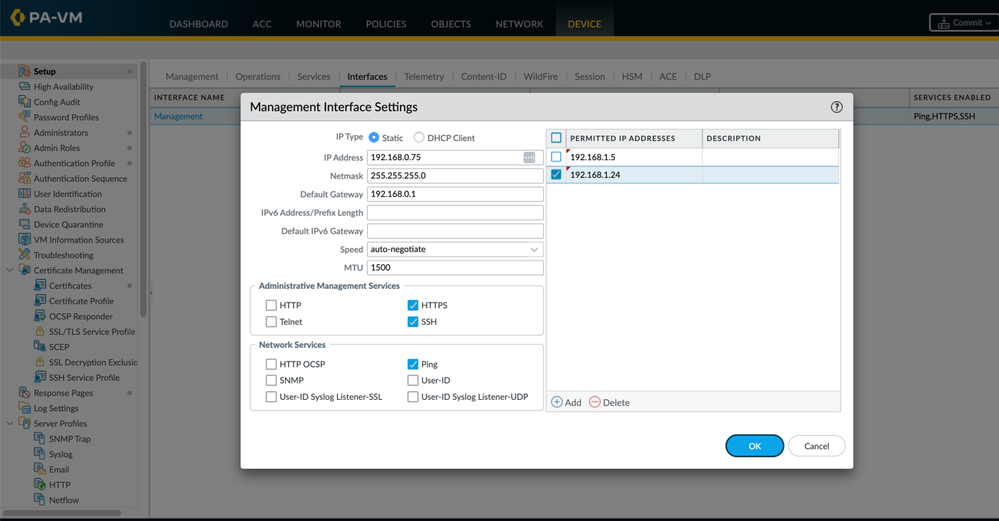
Please share if you know an admin that could use a quick refresher! 🙂
Let us know how you limited access to the admin interface of your device !
Thank you for taking time to read this blog!
Don't forget to hit the Like (thumbs up) button and to Subscribe to the LIVEcommunity Blog area.
As always, we welcome all questions, comments and feedback in the comments section below.
Kiwi out!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
| Subject | Likes |
|---|---|
| 3 Likes | |
| 2 Likes | |
| 2 Likes | |
| 2 Likes | |
| 2 Likes |




