- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Threat signature for ICMP type
- LIVEcommunity
- Discussions
- Custom Signatures
- Re: Threat signature for ICMP type
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-01-2021 12:05 PM
Has anyone had success in creation of threat signatures for ICMP type? I've seen (and tested) the Palo Alto guide on creation of an app to block/allow specific ICMP types and was trying to log a threat event for potential use and visibility versus creation of a new application (and needing to create a new app-id group to accommodate all ICMP types)
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClFZCA0
Working app-id CLI:
set application icmp-type8 default ident-by-icmp-type type 8
set application icmp-type8 subcategory ip-protocol
set application icmp-type8 category networking
set application icmp-type8 technology network-protocol
set application icmp-type8 risk 1
Non working threat CLI:
set threats vulnerability 44008 signature standard icmp-req-data and-condition "And Condition 1" or-condition "Or Condition 1" operator pattern-match pattern 8
set threats vulnerability 44008 signature standard icmp-req-data and-condition "And Condition 1" or-condition "Or Condition 1" operator pattern-match context icmp-req-data
set threats vulnerability 44008 signature standard icmp-req-data and-condition "And Condition 1" or-condition "Or Condition 1" operator pattern-match negate no
set threats vulnerability 44008 signature standard icmp-req-data order-free no
set threats vulnerability 44008 signature standard icmp-req-data scope protocol-data-unit
set threats vulnerability 44008 default-action alert
set threats vulnerability 44008 threatname chrisvuln-icmp-type8
set threats vulnerability 44008 severity informational
set threats vulnerability 44008 direction both
set threats vulnerability 44008 comment "ICMP type 8"
set threats vulnerability 44008 affected-host client yes
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-09-2021 04:27 PM
Hello @TomYoung and @Chris_Johnston
With app and threat release 8484-7039, we have added a new context matching for customer signature. With these 2 new customer contexts, the type detection in ICMP will be a lot easier.
icmp-req-type
icmp-req-code
I tested with icmp-req-type=8 to check the echo request and it was detected.
Please see the attached screen capture. 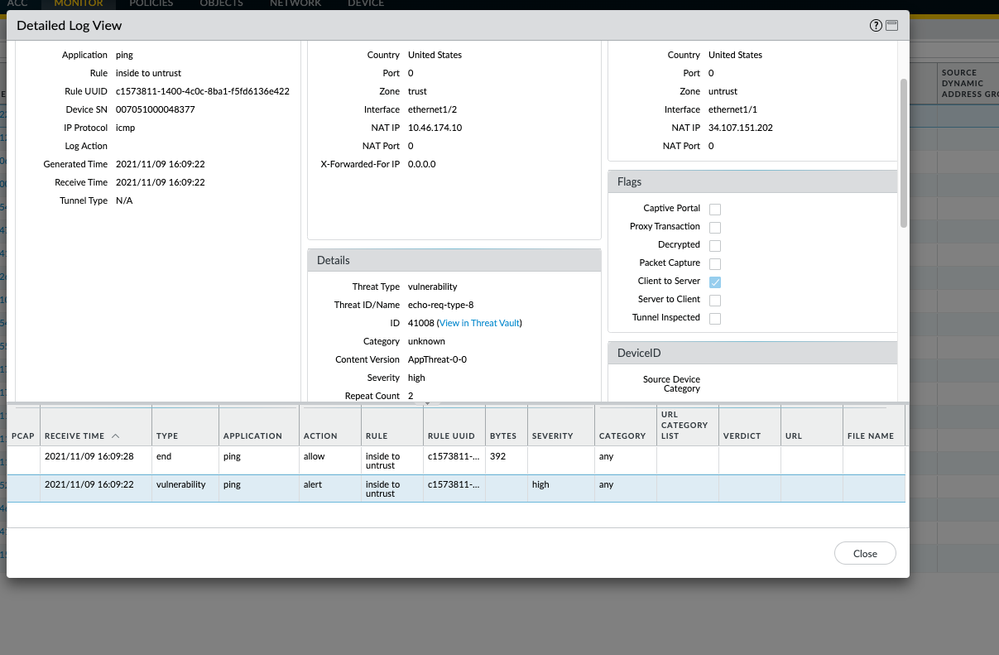
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-01-2021 06:40 PM - edited 09-01-2021 06:42 PM
Cool idea! Just like the GitHub code on HTTP response codes for visibility.
This configuration works for Type 8 and Type 0:
tyoung@fdslcofw01# show | match 4400
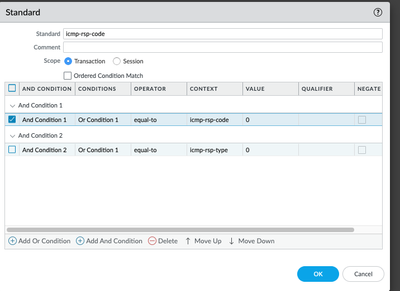
set threats vulnerability 44000 signature standard icmp-rsp-code and-condition "And Condition 1" or-condition "Or Condition 1" operator equal-to value 0
set threats vulnerability 44000 signature standard icmp-rsp-code and-condition "And Condition 1" or-condition "Or Condition 1" operator equal-to context icmp-rsp-code
set threats vulnerability 44000 signature standard icmp-rsp-code and-condition "And Condition 1" or-condition "Or Condition 1" operator equal-to negate no
set threats vulnerability 44000 signature standard icmp-rsp-code order-free yes
set threats vulnerability 44000 signature standard icmp-rsp-code scope protocol-data-unit
set threats vulnerability 44000 default-action alert
set threats vulnerability 44000 threatname "ICMP Type 0"
set threats vulnerability 44000 severity informational
set threats vulnerability 44000 direction both
set threats vulnerability 44000 affected-host client yes
set threats vulnerability 44000 affected-host server yes
set threats vulnerability 44008 signature standard icmp-req-data and-condition "And Condition 1" or-condition "Or Condition 1" operator pattern-match pattern 8
set threats vulnerability 44008 signature standard icmp-req-data and-condition "And Condition 1" or-condition "Or Condition 1" operator pattern-match context icmp-req-data
set threats vulnerability 44008 signature standard icmp-req-data and-condition "And Condition 1" or-condition "Or Condition 1" operator pattern-match negate no
set threats vulnerability 44008 signature standard icmp-req-data order-free yes
set threats vulnerability 44008 signature standard icmp-req-data scope protocol-data-unit
set threats vulnerability 44008 default-action alert
set threats vulnerability 44008 threatname "ICMP Type 8"
set threats vulnerability 44008 severity informational
set threats vulnerability 44008 direction both
set threats vulnerability 44008 affected-host client yes
set threats vulnerability 44008 affected-host server yes
set profiles vulnerability Internal-VP threat-exception 44008 action default
set profiles vulnerability Internal-VP threat-exception 44008 packet-capture disable
set profiles vulnerability Internal-VP threat-exception 44000 action default
set profiles vulnerability Internal-VP threat-exception 44000 packet-capture disable
[edit]
tyoung@fdslcofw01# exit
Exiting configuration mode
tyoung@fdslcofw01> show bad-custom-signature
bad performance custom signature list:
TID: 44008, Vsys 1, Context: icmp-req-data, Pattern: 8
However, I did get the following commit warning:
Warning: one or more custom signatures have big performance impact.
Please see details in CLI "show bad-custom-signature"
You can see the command output above.
There is one strange behavior. I enabled the signatures in 1 VP, but it logs for all. See step 4 in https://docs.paloaltonetworks.com/pan-os/u-v/custom-app-id-and-threat-signatures/custom-application-....
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-02-2021 06:22 AM - edited 09-02-2021 06:37 AM
Makes sense it would log in all, unless you went into each VP and marked it as 'ignore'. That was the challenge with creation of app - it overrides all other icmp apps and unless you create a new application group 'icmp-all' that included icmp and the customs....potential for things to be missed
Edit: Actually, no...doesn't make sense on the VP now looking in depth. Probably one of those PA gotchas
Thanks for crafting the signature! I'm looking forward to seeing it in my lab (and potentially prod!)
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-10-2021 11:01 PM
Hello @TomYoung and @Chris_Johnston
Thank you for the post.
What are we solving;
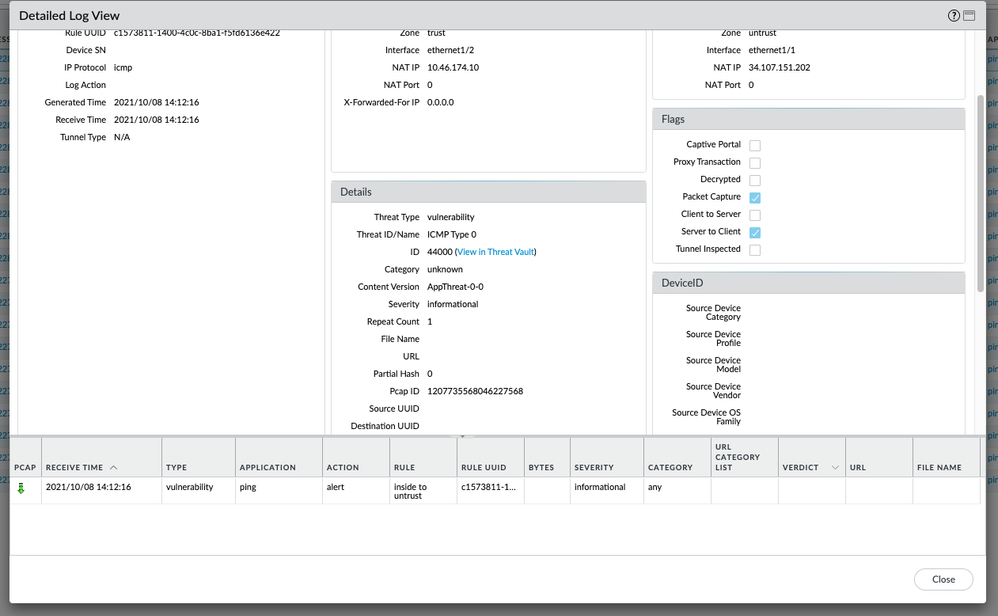
Identify the ICMP request and reply using a custom threat signature.
For ICMP response ( echo-response):
In the custom vulnerability signature, the identity echo-response is easy as the context is available.
The signature 44000, will work perfectly as we have selected icmp-rsp-code [ as 0] and you can also add icmp-rsp-type [ also as 0].
The threat logs is shown as below.
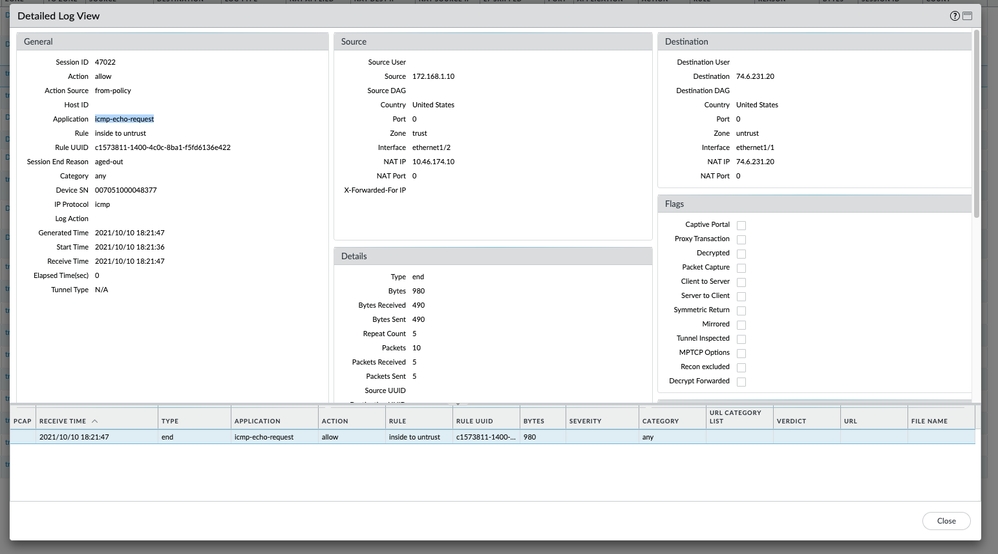
For ICMP request, that is echo request:
This is hard to identify as in the custom vulnerability signature, there is no context to select "icmp-req-code" or "icmp-req-type".
The below line will match the payload in the icmp protocol.
>>set threats vulnerability 44008 signature standard icmp-req-data and-condition "And Condition 1" or-condition "Or Condition 1" operator pattern-match context icmp-req-data
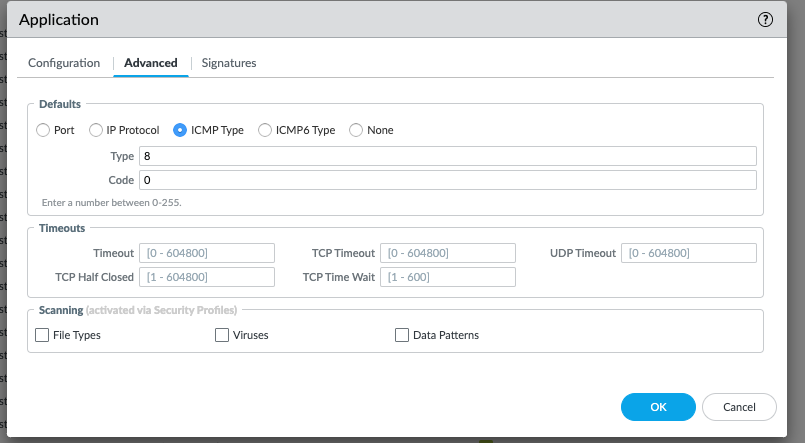
The best way to identify the response code is, please use the custom application identification with ICMP base and select the Type and code as follows.
CLI: show application icmp-echo-request
set application icmp-echo-request default ident-by-icmp-type type 8
set application icmp-echo-request default ident-by-icmp-type code 0
set application icmp-echo-request subcategory internet-utility
set application icmp-echo-request category general-internet
set application icmp-echo-request technology network-protocol
set application icmp-echo-request risk 1
set application icmp-echo-request parent-app icmp
[edit]
show threats
set threats vulnerability 44000 signature standard icmp-rsp-code and-condition "And Condition 1" or-condition "Or Condition 1" operator equal-to value 0
set threats vulnerability 44000 signature standard icmp-rsp-code and-condition "And Condition 1" or-condition "Or Condition 1" operator equal-to context icmp-rsp-code
set threats vulnerability 44000 signature standard icmp-rsp-code and-condition "And Condition 1" or-condition "Or Condition 1" operator equal-to negate no
set threats vulnerability 44000 signature standard icmp-rsp-code and-condition "And Condition 2" or-condition "Or Condition 1" operator equal-to value 0
set threats vulnerability 44000 signature standard icmp-rsp-code and-condition "And Condition 2" or-condition "Or Condition 1" operator equal-to context icmp-rsp-type
set threats vulnerability 44000 signature standard icmp-rsp-code and-condition "And Condition 2" or-condition "Or Condition 1" operator equal-to negate no
set threats vulnerability 44000 signature standard icmp-rsp-code order-free yes
set threats vulnerability 44000 signature standard icmp-rsp-code scope protocol-data-unit
set threats vulnerability 44000 default-action alert
set threats vulnerability 44000 threatname "ICMP echo response"
set threats vulnerability 44000 severity informational
set threats vulnerability 44000 direction both
set threats vulnerability 44000 affected-host client yes
set threats vulnerability 44000 affected-host server yes
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-09-2021 04:27 PM
Hello @TomYoung and @Chris_Johnston
With app and threat release 8484-7039, we have added a new context matching for customer signature. With these 2 new customer contexts, the type detection in ICMP will be a lot easier.
icmp-req-type
icmp-req-code
I tested with icmp-req-type=8 to check the echo request and it was detected.
Please see the attached screen capture. 
- 1 accepted solution
- 6750 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- TID 95187 is not on my signature list in Threat & Vulnerability Discussions
- Palo Alto Threat Vault AntiVirus Signatures in Custom Signatures
- PaloAlto Predefined IP Lists not appearing in General Topics
- Possible threat detected in chrome browser (network.mojom.NetworkService) in Cortex XDR Discussions
- Dynamic User Group Auto Remediation configuration in Next-Generation Firewall Discussions