- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Automating the Palo Alto NGFW's Process/Deamon Restarts
- LIVEcommunity
- Articles
- General Articles
- Automating the Palo Alto NGFW's Process/Deamon Restarts
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
The article you are trying to access is permanently deleted.
- Mark as New
- Subscribe to RSS Feed
- Permalink
on 02-14-2023 08:06 AM - edited on 04-18-2024 12:43 PM by emgarcia
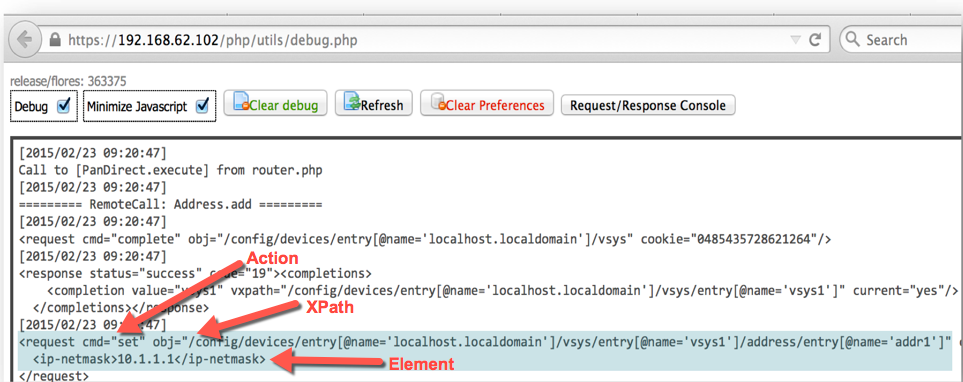
The Palo Alto NGFW has a great API interface and there is even an integrated tool to view the API commands, called api browser that is located at the <firewall ip>/api and it is described at Use the API Browser (there is even a debug window for API traffic. You can also read Use the Web Interface to Find XML API Syntax or Use the CLI to Find XML API Syntax ) but it does not provide access to the operational commands that are starting with "debug xxxx" but why do we need access to those commands?
The answer to the previous question is to restart some palo alto processes without rebooting the full firewall.
For example "debug software restart process web-server" is to restart the backend web-server that is responsible for the PAN-OS GUI. I also suggest checking the articles below:
- Knowledge sharing: restarting palo alto processes, reboot, shutdown, factory default reset (authored by me)
- Commonly Used Processes/Daemons
- How to Restart the Management server "mgmtsrvr" Process
- How to Restart the Web-related Processes
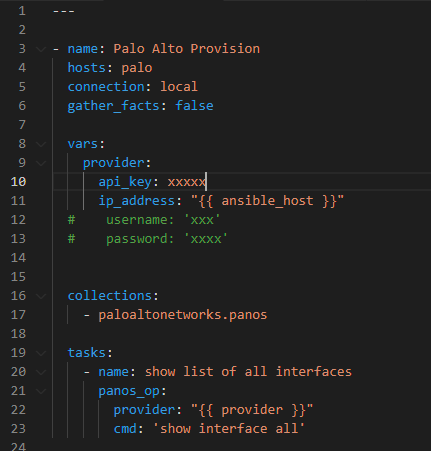
The issue that the API does not have access to the debug commands is that we can't use something like Ansible "paloaltonetworks.panos.panos_op module" which allows to execute random operational commands with Ansible. Ansible has a separate module to run random config commands called panos_config_element and another one called panos_type_cmd (panos_type_cmd seems older one and does not do good checks when pushing commands). We also can't use the Palo Alto XSOAR PAN-OS integration that is shown here, but the XSOAR RemoteAccessV2 is another option to push a debug commands, using SSH, to reboot a process.
As a note, Terraform is more limited to triggering custom commands with its Resources (similar to Ansible modules with tasks) on the Palo Alto Firewalls compared to Ansible (panos_type_cmd/ panos_config_element and panos_op) or Cortex XSOAR (the PAN-OS or RemoteAccessV2 integrations) as Terraform's idea is to have predefined Resources and there is Terraform resource like in Ansible to send custom Operational or Type (configuration) commands if they are available through the Palo Alto API, so only the predefined resources can be used and you can check out this page from Terraform.
Example Playbook for operational commands (except debug commands). For everything else Ansible and XSOAR are still good options (you may need to do things like"pip install pan-os-python " as for some reason when the Ansible collection is installed this is missing.
- name: Palo Alto Provision
hosts: palo
connection: local
gather_facts: false
vars:
provider:
api_key: xxxxxx
ip_address: "{{ ansible_host }}"
collections:
- paloaltonetworks.panos
tasks:
- name: show list of all interfaces
panos_op:
provider: '{{ provider }}'
cmd: 'show interface all'
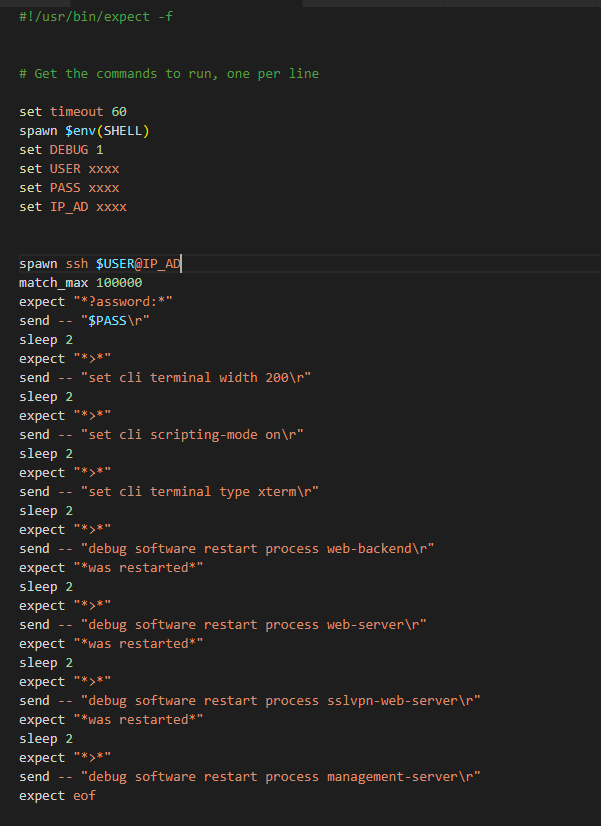
The solution to this issue are the good old TCL Expect scripts! Some may not know but this is one of the first ways to do automation by using SSH even before API was an option. As noted leave the "management-server" process for last if you need to restart it together with other processes as it can kill the script's ssh connection!
Example of a TCL expect script (when the management server is restarted nothing is seen in the CLI, so we can't use "expect" and the ssh connection is terminated, so this process should be restarted at the end):
#!/usr/bin/expect -f
# Get the commands to run, one per line
set timeout 60
spawn $env(SHELL)
set DEBUG 1
set USER xxxx
set PASS xxxx
set IP_AD xxxx
spawn ssh $USER@$IP_AD
match_max 100000
expect "*?assword:*"
send -- "$PASS\r"
sleep 2
expect "*>*"
send -- "set cli terminal width 200\r"
sleep 2
expect "*>*"
send -- "set cli scripting-mode on\r"
sleep 2
expect "*>*"
send -- "set cli terminal type xterm\r"
sleep 2
expect "*>*"
send -- "debug software restart process web-backend\r"
expect "*was restarted*"
sleep 2
expect "*>*"
send -- "debug software restart process web-server\r"
expect "*was restarted*"
sleep 2
expect "*>*"
send -- "debug software restart process sslvpn-web-server\r"
expect "*was restarted*"
sleep 2
expect "*>*"
send -- "debug software restart process management-server\r"
expect eof
"expect eof" is only needed for the management-server restart at the end of the scrip as it not always returns "was restarted" and this will keep the connection open until the management server restart kills it or the script times out.
The TCL Expect script can be on a linux server and Ansible and Cortex XSOAR when there is an Incident and logs in the Cortex Data Lake with its RemoteAccessv2 integration can trigger it as this seems a great integration!
Love to see our members contribute content for the greater good of the community! Thanks @nikoolayy1 !
- 12250 Views
- 4 comments
- 7 Likes
-
"Address Objects"
1 -
10.0
1 -
10.1
1 -
10.2
2 -
ACC
1 -
Active-Passive
1 -
AD
1 -
address objects
1 -
admin roles
1 -
Administration
6 -
Administrator Profile
1 -
Advanced URL Filtering
2 -
Advanced WildFire
1 -
AI
1 -
AI Security
1 -
AIOPS
1 -
Ansible
1 -
antivirus
1 -
API
1 -
App-ID
1 -
applications
2 -
APS
1 -
Asset Management
1 -
Authentication
6 -
Authentication Profile
1 -
Authentication Sequence
1 -
automatically acquire commit lock
1 -
Automation
3 -
AWS
3 -
Basic Configuration
4 -
Beacon
1 -
best practices
6 -
Block List
1 -
categories
1 -
certificates
1 -
Certification
1 -
Certifications
1 -
Certifications & Exams
1 -
CLI
5 -
CLI command
3 -
Cloud Automation
1 -
Cloud Identity Engine
1 -
Cloud NGFW
1 -
Cloud Security
1 -
Collector Group
1 -
Commit and Push
1 -
Commit Process
1 -
Configuration
8 -
Configuration and Management
3 -
Configure Next Generation Firewall
1 -
console
1 -
Cortex
1 -
Cortex Data Lake
2 -
Cortex XDR
3 -
CPSP
1 -
Custom Signatures
3 -
cyber elite
1 -
cyberelite
11 -
dag
1 -
DDoS
1 -
Debug
1 -
debugging
2 -
Default Policy
1 -
discussions
1 -
EDL
2 -
education
1 -
Education and Training
1 -
Education Services
1 -
Educational Services
1 -
Effective Routing
1 -
Endpoint
1 -
export
1 -
failover
1 -
FAQ
1 -
file upload
1 -
Filtering
2 -
Firewall
2 -
Firewall VM-Series
2 -
Focused Services
3 -
Focused Services Proactive Insights
2 -
gateway
1 -
Gateway Load Balancer
2 -
GCP
2 -
GCP Firewall
1 -
geolocation
1 -
Getting Started
1 -
GitHub
1 -
Global Protect
1 -
Global Protect Cookies
1 -
GlobalProtect
7 -
GlobalProtect App
1 -
globalprotect gateway
1 -
GlobalProtect Portal
2 -
google
2 -
Google Cloud
3 -
google cloud platform
2 -
Hardware
2 -
Header Insertion
1 -
High Availability
1 -
How to
1 -
HTTP
1 -
https
1 -
Hybrid Cloud
1 -
ike
3 -
import
1 -
Installation & Upgrade
1 -
IoT
1 -
IPSec
4 -
IPSec VPN Administration
1 -
kerberos
1 -
Layer 2
1 -
Layer 3
1 -
Learning
1 -
licenses
1 -
local user
3 -
Log Cluster Design
1 -
Log Collection
3 -
Log Collector Design
2 -
Logging
1 -
login
1 -
Logs
3 -
Management
8 -
Management & Administration
5 -
MFA
1 -
Microsoft
1 -
Microsoft 365
1 -
Migration
1 -
minemeld
4 -
multi factor authentication
1 -
multi-factor authentication
1 -
multi-vsys
1 -
NAT
1 -
NetSec
1 -
NetSec Newsletter
1 -
Network Security
34 -
Network Security Management
1 -
network-security
1 -
Networking
1 -
newsletter
2 -
Next Generation Firewall
4 -
Next-Generation Firewall
42 -
next-generation firewall. network security
1 -
Next-Generation Firewall. NGFW
6 -
NGFW
30 -
NGFW Configuration
11 -
NGFW Newsletter
1 -
Nominated Discussion
1 -
Objects
2 -
OTP
1 -
PA-3200 Series
1 -
PA-400
1 -
pa-440
2 -
PA-5400 series
1 -
PA-800 Series
1 -
pa-820 firewall
1 -
Packet Buffer
1 -
packet debug
1 -
packet diag
1 -
PAN-OS
16 -
PAN-OS 10.2
1 -
PAN-OS 11.0
1 -
PAN-OS Prisma Access
1 -
Panorama
11 -
Panorama Configuration
2 -
PBF
1 -
PCNSA
1 -
PCNSE
1 -
performance
2 -
policies
2 -
policy
3 -
Policy Based Forwarding
1 -
Prisma Access
5 -
Prisma AIRS
1 -
Prisma SD-WAN
1 -
proactive insights
2 -
Radius
1 -
Ransomware
1 -
region
1 -
Registration
1 -
reporting and logging
1 -
RestAPI
1 -
Risk Management
1 -
Routing
1 -
SAML
1 -
SASE
1 -
script
2 -
SD WAN
1 -
SDWAN
1 -
Search
1 -
Security Advisory
1 -
Security automation
1 -
security policy
4 -
security profile
1 -
Security Profiles
2 -
Selective Push
1 -
Session Packet
1 -
Setup & Administration
8 -
Site-to-Site VPN
1 -
Split Tunneling
2 -
SSL
1 -
SSL Decryption
2 -
SSL Forward Proxy
1 -
SSO
1 -
Strata Cloud Manager
1 -
Strata Logging Service
2 -
Support Guidance
1 -
syslog
1 -
system modes
1 -
Tag
2 -
tags
2 -
Terraform
2 -
Threat
1 -
threat log
1 -
Threat Prevention
1 -
Threat Prevention License
1 -
Tips & Tricks
1 -
TLS
1 -
traffic_log
1 -
Traps
1 -
Troubleshoot
2 -
Troubleshoot. logs
1 -
Troubleshooting
6 -
tunnel
2 -
Tutorial
2 -
Unified Monitoring
1 -
upgrade
1 -
upgrade-downgrade
2 -
url categories
1 -
URL Filtering
2 -
URL-Filtering
1 -
User ID Probing
1 -
User-ID
1 -
User-ID & Authentication
1 -
User-ID mapping
1 -
userid
1 -
VM Series
1 -
VM-Series
7 -
VM-Series on AWS
3 -
VM-Series on GCP
2 -
VPC Flow logs
1 -
VPN
3 -
VPNs
4 -
Vulnerability
2 -
Vulnerability Protection
1 -
WildFire
2 -
Wildfire License
1 -
wmi
1 -
XDR
1 -
xml
2 -
XML API
2
- Previous
- Next