- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Cannot block theoxymoron.xyz
- LIVEcommunity
- Discussions
- General Topics
- Re: Cannot block theoxymoron.xyz
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
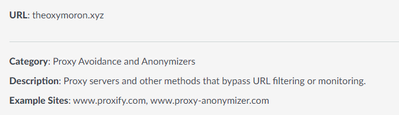
Cannot block theoxymoron.xyz
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-02-2022 12:04 PM
Hello, I have been trying to block the site theoxymoron.xyz but can not get it to block. I have tried URL filtering with many different versions of the URL as well as blocking the IP addresses for the site, neither of which worked for me. We do not use decryption. Any help would be appreciated. Thank you.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-02-2022 12:31 PM
How exactly are you attempting to block? Does the Security Policy the traffic is going thru have a URL Filter policy attached? Have you created a custom URL Category? What format did you put the entries into the URL Category? When blocking by IP, did you put the IP in a URL category or create a separate Security Policy?
Sorry for so many questions, but there are at least a half dozen different ways to filter/block sites depending on how your firewall is configured...
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-02-2022 01:02 PM
No worries about all the questions. I have a url filter policy attached to one security policy and then a different security policy to deny the IPs. Here are some of the different ways I tried to input the URL to block it:
theoxymoron.xyz
*.theoxymoron.xyz
there were more, but I cant remember everything I tried.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-02-2022 02:33 PM
Hello,
Why not block the category?
Just a thought.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-02-2022 02:46 PM
Yeah, we already had that category blocked, but that site was listed as arts and entertainment until about an hour ago. I submitted the request to change it and it went through, now its coming up blocked. Thanks for your help guys!
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-02-2022 03:07 PM
So... as I said, there are many ways to do this. But if you are using a Security Policy with a URL Filter policy attached, do something like this. First you should have an existing Security Policy for your general internet bound traffic. You may want to use the "Test Policy Match" tool at the bottom of the Security Policy page to verify the traffic is actually using the intended policy. The URL Filter must also be something other than "default" as you can not change the default filter categories.
Policies->Security
name=Internet Access
SrcZone=Trust
SrcAddr=CorpInternalIPs
DstZone=Untrust
DstAddr=any
Application=any
Service=any
Action=Allow
Profile Settings->URL Filtering=CorpURLFilter
Then create a custom URL Category for all domains you want to block (regardless of their other automatic categorization). The entries should only be the FQDN and possibly a URL path (path will only work if you are doing SSL decryption). Without encryption it can be a bit trickier as you only have the SNI to work off of. The entries should be terminated with a slash or other delimitator to ensure variable expansion doesn't match to unintended paths (see https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA14u000000oM79CAE&lang=en_US%E2%80%A...). Be sure to add both the root and wildcarded server names as the wildcard will not capture the root by itself. Don't put http/https specific resource indicators:
Objects->Custom Objects->URL Category
name=Corp-Block
sites=
theoxymoron.xyz/
*.theoxymoron.xyz/
Now in your URL Filtering policy you should see your custom URL Category. Set the Site Access to "block":
Objects->Security Profiles->URL Filtering
name=CorpURLFilter
Category=
ᐁ Custom URL Categories:
Corp-Block=block,block
...
ᐁ Predefined Categories
... whatever your corporate URL categories filtering policies are...
Your Custom URL Category will override the Predefined Categories settings for anything matching your CorpBlock.
Alternatively, you can block based solely on IP address. This can be a bit more troublesome as, depending on the hosting, the website may be hosted on more IPs than the PA can track, using fast-flux DNS, may use many FQDN names, or using multiple redirects. This only works when you know the specific FQDN, unfortunately there isn't a way to wildcard address objects. Start by creating some address objects to block:
Objects->Addresses
name=theoxymoron-xyz
type->FQDN=theoxymoron.xyz
name=www-theoxymoron-xyz
type->FQDN=www.theoxmoron.xyz
Now create a new internet-bound rule for the specific destination IPs you want to block. You don't need a URL filtering policy or other attributes on this as you will just be blocking:
Policies->Security
name=Internet-BlockDestinations
SrcZone=Trust
SrcAddr=CorpInternalIPs
DstZone=Untrust
DstAddr=theoxymoron-xzy,www-theoxymoron-xyz
Application=any
Service=any
Action=Block
Depending on how you have your firewall setup, and your security posture, you may want to use one or another path. I use both of the above methods (and other methods) for various categories of blocking, FQDN/domain based URL Filter based on URL-root names for general websites, Security Policy general blacklists for various other IPs and networks that should never have any traffic http/https or otherwise.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-02-2022 03:09 PM - edited 11-02-2022 03:10 PM
Yep... I tested the PA category a little bit ago, as I first started typing my above reply, and saw it as Arts&Entertainment as well. Showing up as Proxy Avoidance now here too.
- 6957 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Cortex XDR Device Control Violation Alerts in Cortex XDR Discussions
- Notepad++ block specific hash version in Cortex XDR Discussions
- looking to block google ai mode in Advanced URL Filtering Discussions
- Request for Query to Retrieve Endpoint Security Details. in Cortex XDR Discussions
- Cortex Pop-ups Triggered for StoreDesktopExtension.exe Despite Being Blocklisted in Cortex XSIAM Discussions