- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Captive portal browser challenge issue
- LIVEcommunity
- Discussions
- General Topics
- Re: Captive portal browser challenge issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Captive portal browser challenge issue
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-16-2020 11:35 AM
Hi team,
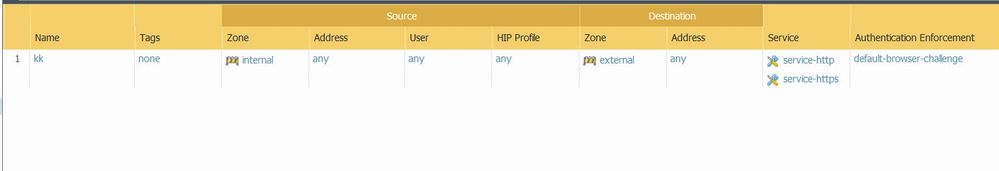
While trying to deploy Kerberos SSO for enduser authentication I came up to the following issue with the captive portal (browser challenge).
When an end user logged in a windows (part of the domain) tries to connect to "http://neverssl.com" for example here is what's happens on the wire :
1/ The browser send a request to neverssl.com
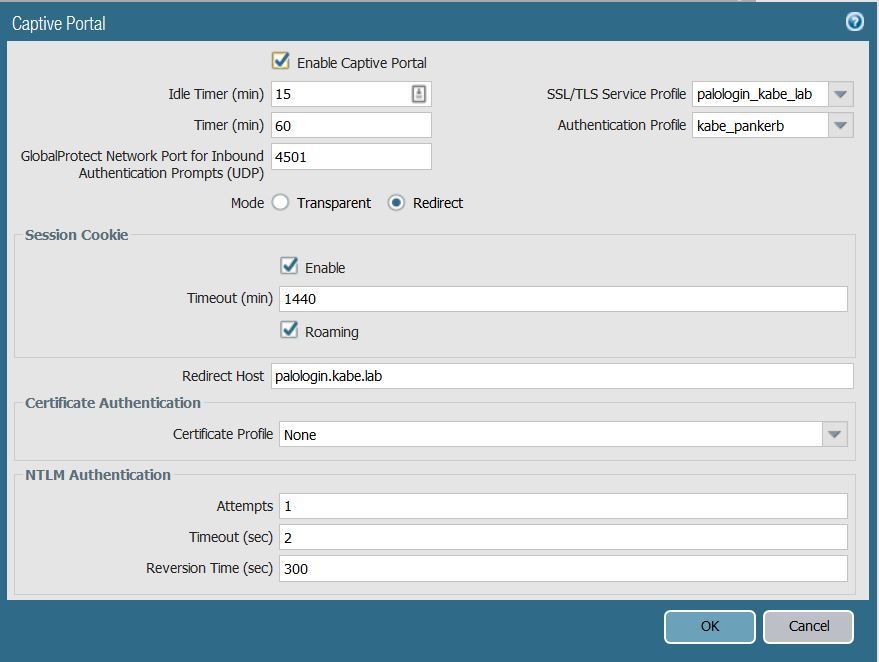
2/ Pan redirect the browser to the captive portal with 302 to the location : http://palologin.kabe.lab:6080/php/browser_challenge.php?vsys=1&rule=0&url=http://neverssl.com%2f
3/ The browser follows the redirect and gets this response from the palo :
HTTP/1.1 200 OK
Date: Thu, 16 Apr 2020 15:29:51 GMT
Content-Type: text/html
Content-Length: 909
Connection: keep-alive
Cache-Control: no-cache
Set-Cookie: SESSID=f4MBAV6Yee96xCU+AwMFAg==; path=/
<HTML>
<HEAD>
<TITLE>Kerberos V5 Authentication Redirection</TITLE>
<meta http-equiv="refresh" content="5; url=http://palologin.kabe.lab/php/browser_challenge.php?vsys=1&rule=0&url=http://neverssl.com%2f&preauthid=&returnreq=yes&challengetimeout=yes">
</HEAD>
<BODY>
<script language="Javascript" type="text/javascript">
if(typeof(Storage) != "undefined") {
var orig_url = "";
sessionStorage.setItem ("isoffline", 0);
if(orig_url != "")
sessionStorage.setItem("origurl", orig_url);
}
window.location = "http://palologin.kabe.lab/php/browser_challenge.php?vsys=1&rule=0&url=http://neverssl.com%2f&preauthid=&returnreq=yes";
</script>
<p><b>Kerberos V5 Authentication Redirection</b></p>
<p>In case you see this page,
<ol>
<li>Your browser does not support both Kerberos and NTLM authentication. Waiting for refresh.</li>
</ol>
</p>
</BODY>
</HTML>
4/ The browser executes the javascript and sends a GET request to "http://palologin.kabe.lab/php/browser_challenge.php?vsys=1&rule=0&url=http://neverssl.com%2f&preauth..."
5/ The browser get no responses, and the authentication fails !
The problem is at step 4/ in which the paloalto should make the browser send the GET request to "http://palologin.kabe.lab:6080/php/browser_challenge.php?vsys=1&rule=0&url=http://neverssl.com%2f&preauthid=&returnreq=yes" instead.
I used fiddler to change the browser request number 4 (and add the :6080) and the authentication worked just fine !
I tried to search for similar bug in the KB without success , am I the only one who is facing this issue ? or am I missing something in my config ?
I'm on version 91.2 and here is my config :
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-19-2020 12:24 PM
Hi everyone, does anyone ever come across this issue ? Just want to make sure if I'm missing something in my config or no
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-05-2020 01:16 PM
I am facing a kind of similar issue. i want to know what did you allow to fix this issue.
i am not able to open the browser but i can telnet my CP url.
Thanks in advance.
- 6629 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- CIE for user/group mapping for firewall on-premise in General Topics
- Mist AP and user-id in Next-Generation Firewall Discussions
- Captive Portal SSO browser-challenge issue in General Topics
- GP - Connect with SSL Only in General Topics
- Issues with Captive Portal / Continue URL Filtering Response page on 10.1.12 in Next-Generation Firewall Discussions