- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Checking Global Protect Client Status via Command Line
- LIVEcommunity
- Discussions
- General Topics
- Re: Checking Global Protect Client Status via Command Line
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-03-2017 05:48 AM
We have had a heck of a time getting Global Protect 4.0.2 deployed in our environment. One of the things I am coming across is that the install goes fine, at least accoring to the exit code on msiexec and in looking thoguht the log created by msiexec. However, the pangps service does not always get created. Granted, the number of macine affected by this problem is smallish. I would say 3-6%. Now I can check for the existance of the service and manually create it and that fixes most of the machines, but now I am trying to circle back around for all the machines to determine if the global protect client is working ok. On many machines I can check to see if the PanGP interface has an IP address in the range we assigned, but other machines "live" at a location where the site has a connections, either via MPLS or DMVPN to the main office, so Global Protect is considered to be on its home network. I am looking for a way that will allow me to detect if GP is running correctly whether it is on a home network or not. A string in a log, a registry key, a command line that will give me an exit code, etc. something I can deploy that will allow me to see if the client is in "home", active or disabled mode from a command prompt. Powershell is also an option. Ideas?
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-03-2017 12:01 PM
Probably not the simple solution you are looking for, but in the local log files that GP client is writing to the folder where it was installed you should find the information you want
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-03-2017 05:56 AM - edited 08-03-2017 06:44 AM
Hey @BeejCyr
To allow users to connect to GP even when they are at "home" site, make use of 'Internal Gateways'.
Regards,
Anurag
ACE 7.0, 8.0, PCNSE 7
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-03-2017 06:39 AM
Thanks for the resources, but it is not quite what I am going for. I am looking for a way to determine the status of the Global Protect agent from the command line. My script will not be able to "see" the icon, and the script may be running while all users are logged out and the client will be connected in a prelogin state. Another couple of facts that may figure in to the solution:
- We are using SSO.
- I have no access to the gateway. My area of responsibility is client deployment.
@ansharma wrote:Hey @BeejCyr
To allow users to connect to GP even when they are at "hom" site, make use of 'Internal Gateways'.
Here's some information to get you started:
HTH.
Regards,
Anurag
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-03-2017 06:40 AM
FYI, I get a 404 on all three links you supplied.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-03-2017 06:42 AM
I guess I'll remove the links since they wouldn't help in your requirement.
ACE 7.0, 8.0, PCNSE 7
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-03-2017 09:42 AM
Hi Mate,
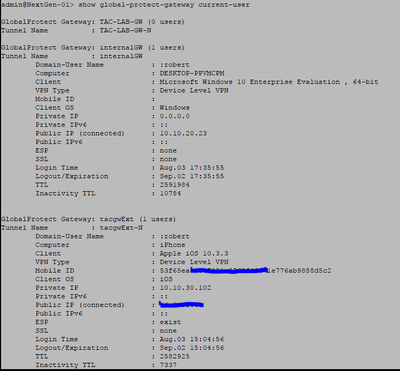
Not sure if this ticks the box. But from the cli ye can see the current users logged in for th eglobal protect and the gateways they are logged on to. Can add to the cli command to just check for internal or external gateways if needed.
admin@NextGen-01> show global-protect-gateway current-user gateway
TAC-LAB-GW TAC-LAB-GW
internalGW internalGW
tacgwExt tacgwExt
<value> Show for given GlobalProtect gateway
admin@NextGen-01> show global-protect-gateway current-user gateway
Doesn't scale well I guess with 100's or 1000s.
From the web ui you can also see the current users logged in,
networks>global protect > gateways -> far right , current users..
screenshot below from lab set up showing external user on the ext gateway and a local guy on the internal gateway.
best regards,
Rob
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-03-2017 11:43 AM
Rob,
Yeah, if I could get access to the gateway it would be easier, but alas I cannot.
With the Cisco AnyConnect VPN client we are replacing, I can do something like vpncli /status and it would product some test I could search through. I was really hoping GlobalProtect did something similar.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-03-2017 12:01 PM
Probably not the simple solution you are looking for, but in the local log files that GP client is writing to the folder where it was installed you should find the information you want
- 1 accepted solution
- 24800 Views
- 7 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Command to Disconnect Global Protect VPN in GlobalProtect Discussions
- How to specify multiple conditions for the "test custom-signature-perf" command in Custom Signatures
- Customize Authentication Complete URL in General Topics
- Cortex XSOAR - Best Practice Optimize Threat Intelligence Management (TIM) in Cortex XSOAR Discussions
- User´s problem connection in GlobalProtect Discussions