- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Client VPN traffic and routing over IPsec Tunnel
- LIVEcommunity
- Discussions
- General Topics
- Re: Re: Client VPN traffic and routing over IPsec Tunnel
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Client VPN traffic and routing over IPsec Tunnel
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-19-2013 01:50 PM
Hi there,
Here is our scenario that I am trying to figure out.
We have two sites (main office and a rack in a data center) that are connected via PAN-2020's on both sides through a IPsec Tunnel. I am trying to route Client VPN traffic that connects at our main office to go over the site-to-site tunnel to access some web servers there. It seems the traffic goes over the tunnel, but all is marked as incomplete. Below is my config..is it a route metric issue or a routing issue in the Client VPN traffic config? Our VPN clients are obtaining DNS from internal domain controllers. Our web server are defined with internal zones on those domain controllers, that is why I am having this issue. Any help would be appreciated. Can provide additional details as needed.
Main Office:
Zones:
Trust Zone - (192.168.x.x/16)
SSL-VPN Zone - (172.x.x.x/24) - no split brained routing (0.0.0.0/0)
Site-to-Site Tunnel
Routes:
Default Route: 0.0.0.0/0 - metric 10
Trust Zone - metric 5
SSL-VPN Zone - next hop 0.0.0.0 - metric 8
All traffic over tunnel to remote zones - metric 5
Security Policies:
Trust Zone & SSL-VPN zone to Tunnel - allow all traffic
Data Center Rack:
Zones:
Trust Zone - (10.20.x.x/16)
Untrust Zone - (10.30.x.x/16) - were web servers are
Site-to-Site Tunnel
Routes:
Default Route: 0.0.0.0/0 - metric 10
Trust Zone - metric 1
Untrust Zone - metric 1
All traffic over tunnel to remote zones - metric 1
Security Policies:
Trust Zone & Untrust Zone to Tunnel - allow all traffic
- Labels:
-
Configuration
-
Networking
-
Set Up
-
Troubleshooting
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-19-2013 02:48 PM
Hello cmateam,
Incomplete means that either the three way tcp handshake did NOT complete or the three way tcp handshake did complete but there was no data after the handshake to identify the application. In other words that traffic you are seeing is not really an application.
So to explain a little clearer, if a client sends a server a syn and the Palo alto device creates a session for that syn, but the server never sends a syn-ack in response back to the client, then that session would be seen as incomplete.
Could you please share the session detail info here and do packet captures on the firewall at the transmit, receive and drop stage.
Example:
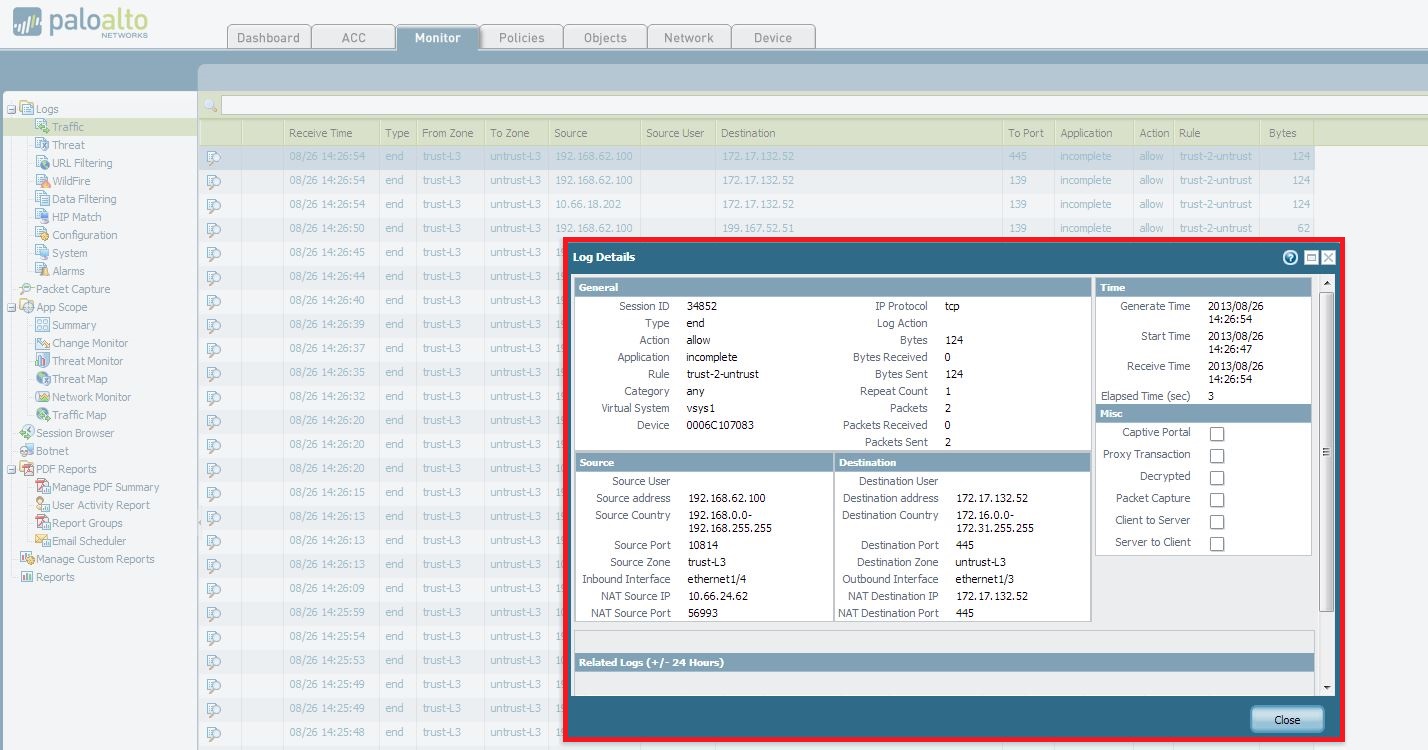
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-20-2013 08:38 AM
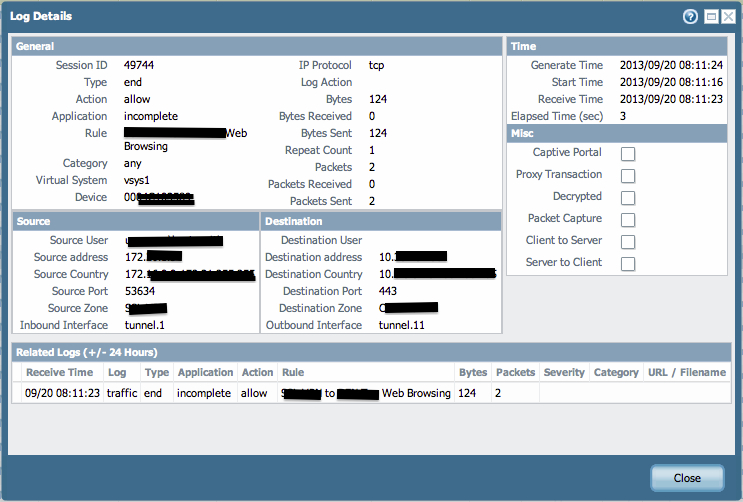
Here is the screen shots and packet captures. Hope this helps.
Packet Captures: Dropbox - PAN (doesn't look like I can upload the packet captures here) this is on the firewall handling the Client VPN traffic)
Traffic on FW handling Client VPN traffic
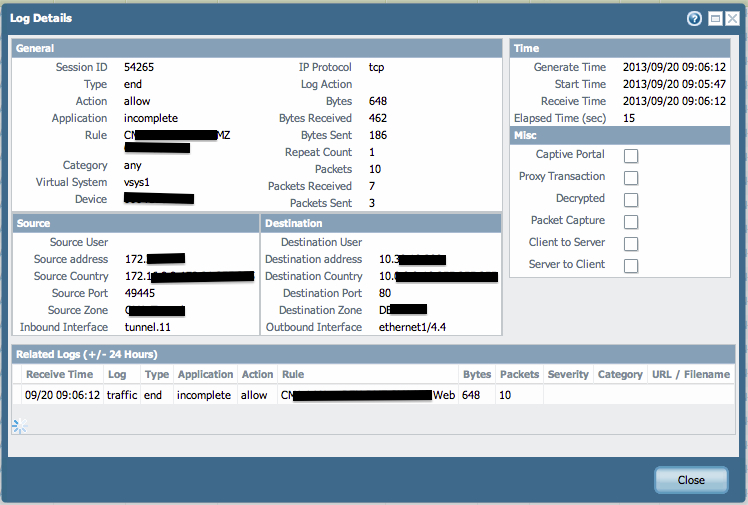
Receiving FW
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-21-2013 09:04 AM
Hi,
wwe have the same network configuration, but I don't know what I need to configure for give the VPN client access to the remote site resources.
Can an any one help me withe the configuration?
thank you.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-21-2013 11:23 AM
You may try to traceroute from servers to vpn clients and see what is wrong.seems to be routing issue.Try to add a route for a web server and forward its traffic for vpn subnet through tunnel.see if it works
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-23-2013 02:19 PM
Traceroute helped identify the problem and reading this post: Accessing all company networks with GlobalProtect client - turns out it was a route that needed to be added on the other side to return the traffic back to the client. Looks like everything is working as expected.
cc: @leonidspect
- 9019 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Azure to OnPrem Connectivity issue in Next-Generation Firewall Discussions
- Issue after onboard Azure VM into SCM in Strata Cloud Manager
- GlobalProtect Always-On (6.3.3-c711) – Users Stuck in “Connecting” State but Still Have Internet Access in General Topics
- Unable to establish tunnel during Service Connection configuration (Details Added with Screenshot) in Prisma Access Discussions
- Prisma Access with ECMP in Prisma Access Discussions



