- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Commit Error After Upgrading to 10.0.9
- LIVEcommunity
- Discussions
- General Topics
- Commit Error After Upgrading to 10.0.9
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Commit Error After Upgrading to 10.0.9
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-07-2022 07:27 AM
Hi Team,
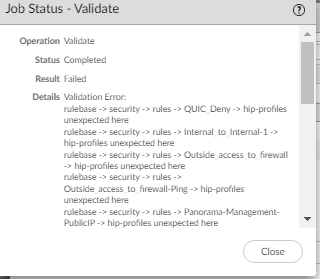
Getting below commit validation error after upgrading to PAN-OS 10.0.9.
- Validation Error:
- rulebase -> security -> rules -> QUIC_Deny -> hip-profiles unexpected here.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-19-2022 02:38 AM
Yes, in my case most of the rules were also generated using the BPA+ tool, but one of them don't. So maybe it's not just the tool causing this.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-21-2022 02:09 PM
1) Save named configuration snapshot
2) Export named configuration snapshot
3) Open saved file in editor and remove
<hip-profiles>
<member>any</member>
</hip-profiles>
from authentication rules
4) rename saved file to new name
5) Import named configuration snapshot
6) load config partial mode replace from-xpath devices/entry[@name='localhost.localdomain']/vsys/entry[@name='vsys1']/rulebase/authentication/rules to-xpath /config/devices/entry[@name='localhost.localdomain']/vsys/entry[@name='vsys1']/rulebase/authentication/rules from your_imported_configuration_snapshot.xml
7) validate and commit
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-22-2022 02:04 PM
We just entered the same issue after upgrading our panorama to 10.1.5h5, it's code issue where hip-profiles are changed to be source-hip, we have more than 2k rules impacted manual rule clone doesn't fit for us, so the quickest solution is to load your saved sanpshot:
Step 9 from below link:
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-24-2022 06:59 PM
This solution worked for us. Reloading saved snapshot.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-25-2022 09:58 PM
Heya
We've gotten the following workaround to fix our issue with 10.1.5h1 on Panorama.
> Panorama will need to perform a commit fix and apply some transforms using the transform script.
Resolution:
> Run the following CLI commands to resolve the validation error, 'hip-profiles expected here'.
>configure
#load config from running-config.xml
#commit force
<<
This workaround is by far better then the copy replace in notepad workaround for all the wrong rules.
Anyhow, even though the fix is quick and simple. One would wish Palo documentation would be update and well documented for this. Also a hotfix for the hotfix would be appreciated.
Best regards
Alex
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-26-2022 07:30 AM
Could not change the settings via CLI, I get syntex Error.
So I exportet the XML and removed all
" <hip-profiles>
<member>any</member>
</hip-profiles> "
and loadet it and commit worked.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-28-2022 01:34 AM
Hi Ederg
that work's for me too,
thx
Yordan
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-28-2022 02:38 AM
I have same issue in Authentication rule too. I solved with export config and edit the notepad++ and remove the the following lines
in rules :
<hip-profiles>
<member>any</member>
</hip-profiles>
...
<source-hip>
<member>any</member>
</source-hip>
<destination-hip>
<member>any</member>
</destination-hip>
and then saved edited xml files and import + load operation and works for me .
Thank You.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-12-2022 03:13 PM
This solution to: " #load config from running-config.xml and then to do a #commit force" , was the only thing that worked for me.
@AlexNC Thank you very much for saving my bacon !!
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-30-2022 03:45 AM - edited 05-30-2022 04:07 AM
So export/import/load/find/replace aside, if you want to fix the issue right then and there in-place:
1. It is a leftover of pre-upgrade configuration which makes commit fail, as the new PAN-OS does not recognise it
2. It is not visible in the GUI, so cannot be removed
3. It cannot be removed with a "delete" command on CLI, because the CLI validation engine does not recognize it and you will get 'invalid syntax'
4. This is a funny debacle on PANW end, sure
5. So what you can do is this. Remove the whole auth policy and re-enter it without the hip-profile element. This can be done manually using GUI or in a more proper way by using the cli and the set format.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-08-2022 12:17 PM
Our Panorama ran into this issue on a device group with 5,000 security policies. I am running 10.1.5 h2 and I resolved this with Expedition by importing and using the API to push just the security rules back to the device group.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-08-2022 11:53 AM
We've upgraded to 10.1.6 h3 and issue is still there. Common Palo. What the hell?
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-08-2022 01:46 PM
Spent some time on a call with TAC. It is known issue. The way we got around it is to load the last known "good" configuration (pre upgrade). We have this issues with Panorama and loading "panorama configuration version" and then committing did the trick. TAC uses this as a work around.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-09-2022 11:32 AM
We faced similar issues again after upgrading Panorama to 10.2.2. If the issue is for Panorama, then before working on editing the configuration file, please try restarting the management service on Panorama. It solved issues for us when Panorama could not push config to the firewalls (Panorama version 10.2.2, Firewalls version 10.1.5)
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-22-2023 04:33 AM
I had this problem last night going from 9.1.x to 10.1.x. My problem was that all except one of the errors was happening locally and one was happening from Panorama.
This fixed the local ones:
>configure
#load config from running-config.xml
#commit force
Going to the rule that was having an issue from Pano and giggling the handle (changing something small - like a tag - on the rule) fixed that one.
- 22025 Views
- 44 replies
- 2 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Upgrading 10.1.11-h5 to 11.1.2 directly ? in Panorama Discussions
- XSAOR with HA using Open search Upgrade in Cortex XSOAR Discussions
- 10.2.8 DP DP Hardware Packet Buffer exhaustion bug in Next-Generation Firewall Discussions
- Need to upgrade PA 440 Firewall in Next-Generation Firewall Discussions
- Firewall has the IPSec tunnel but Panorama don't. How to fix? in Panorama Discussions