- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
DNS service route doesn't work ?
- LIVEcommunity
- Discussions
- General Topics
- DNS service route doesn't work ?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
DNS service route doesn't work ?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-23-2013 06:41 PM
Hi,
I am having troubles configuring dns service route for DNS.
DNS servers are behind tagged internal interface of PA-2050 device.
I was able to configure that for syslog and it sends all the traffic PA outbound to the server.
I was trying to do the same with DNS, but when I do, PA stops sending queries either through management interface or through the interface the routing to dns servers is.
I'm not using dnsproxy.
Is this enough information for any help ?
Any options, what should I try ?
Best regards,
Pawel
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-24-2013 06:40 AM
Hello Pawel,
Are you able to ping the DNS servers from the Palo Alto firewall?
So, if you are using an interface other than the management interface (example Ethernet1/2), are you able to ping from Ethernet1/2's ip address to the DNS server? OR, if you are using default configuration (i.e management interface), can you ping from the management interface to the DNS servers?
Also, the DNS servers configured under Device> Setup > Services - are those internal or external?
Regards,
Kunal Adak
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-24-2013 06:42 AM
Hi,
Do you see any thing in the traffic logs or threat logs regarding DNS traffic on the PAN being dropped ?
Thanks,
Syed R Hasnain
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-24-2013 08:12 AM
Hello Pawel,
If you are configuring service routes for reaching to DNS server through any other interface other than management interface yes we do it as shown in below image.
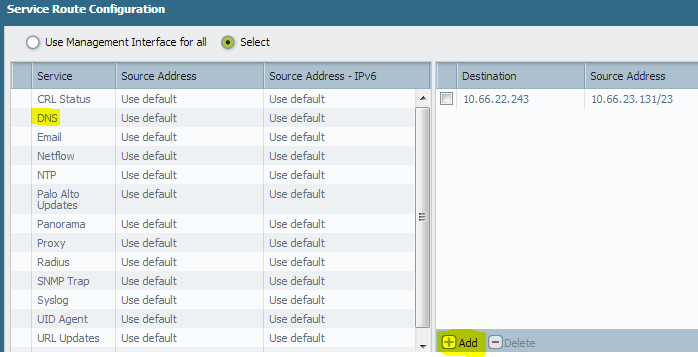
I have highlighted on left for DNS, we generally select another interface on PAN to pass traffic. In your case seems like this is not working neither the management interface.
Steps to ensure:
1> Do source ping:
ping source <New interface IP configured on service route> host <Dns server IP>
If configured right it has to send out pings and we can see outcome.
2> We can take packet captures on PAN for new interface configured for DNS traffic to pass through and instantly we can see data on the captures, if we do not see then PAN is not passing.
Based on the captures we may know that if the Dns server if received dns packets from PAN did it respond back or not.
3> Also in the above image on the right you can select custom values as shown.
Indicate the DNS server IP in destination field and source address as the new interface IP address.
Hope these steps should narrow down the issue.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-27-2013 05:08 PM
Thank All for help,
Sorry for the late reply.
It turned out firewall itself blocked access to dns-es as there was no security rule for that.
In fact, this was not obvious as I put a rule for that but somehow it didn't work. I've just opened wide access from "all" zones to dnses and it started to work. Maybe that should be narrowed, but as I'm fighting with other pcularities it was no time to debug.
Thanks again,
Pawel
- 3385 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Should I override the intrazone-default to deny? in Next-Generation Firewall Discussions
- No DNS, cannot ping anything above gateway in General Topics
- Inquire how to stop EDL updates from going through Proxy Server in General Topics
- error: azure marketplace vm-series do not bootstrap in VM-Series in the Public Cloud
- Blocking traffic initiated from Trusted Zone - AWS in Prisma Access Discussions



