- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
DynDNS client on PANOS 9.0
- LIVEcommunity
- Discussions
- General Topics
- Re: DynDNS client on PANOS 9.0
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-03-2019 01:37 AM
Hi,
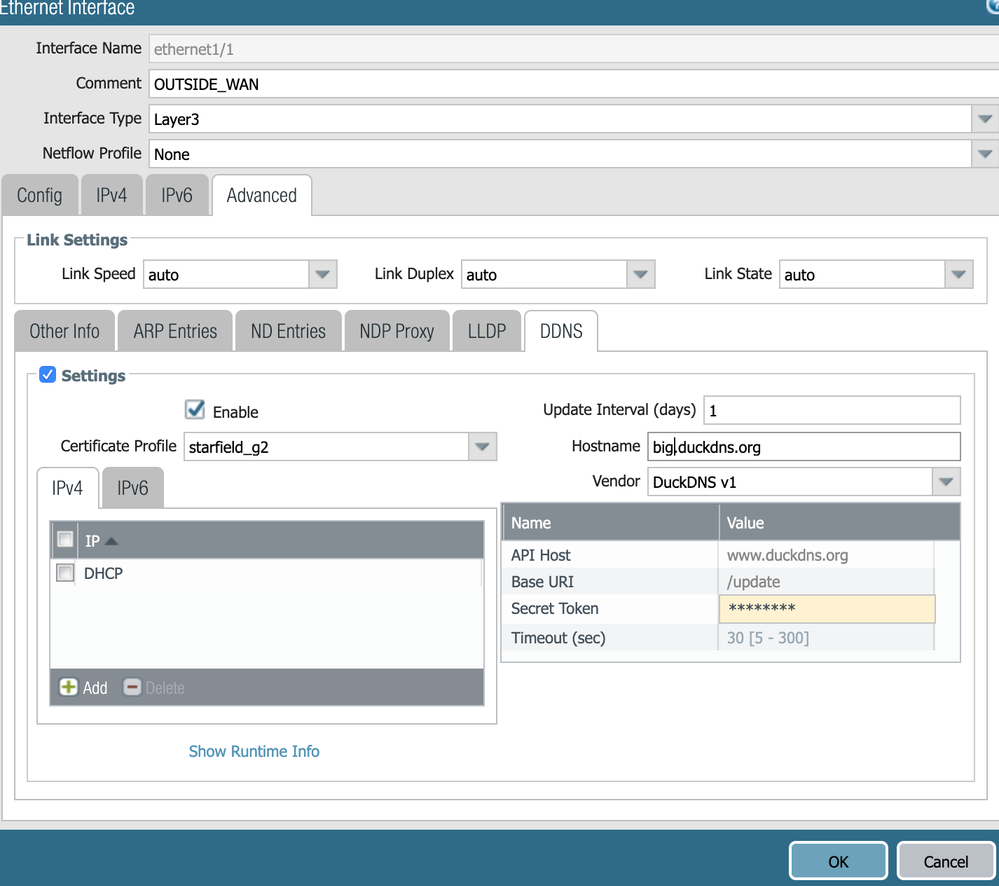
I'm trying to setup DynDNS based on the instructions found at https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-admin/networking/configure-dynamic-dns-for-firew...
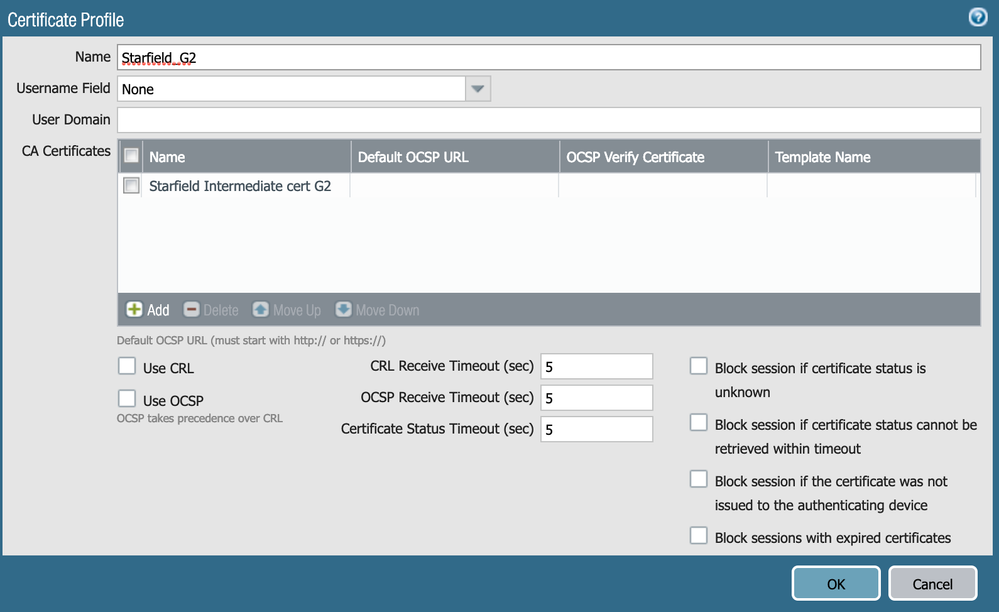
I'm using DuckDNS, but I'm stuck at the 'certificate profile' portion. As I understand it correctly I have to import the (public) SSL certificate of DuckDNS, but this is not provided by them.
I don't understand why this is needed since their certificate is signed by Starfield CA, which is already in the list of 'Default Trusted Certificate Authorities' on the Paloalto firewall.
Also other DynDNS provides such as DYN don't seem to provide their public certificates for download.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-03-2019 01:02 PM
The public cert is always public available. It is send in every tls connection that you establish to duckDNS. In your browser you can see the cert also when you check the tls certificate of the website.
The duckDNS cert is this one here:
-----BEGIN CERTIFICATE-----
MIIGYDCCBUigAwIBAgIJAOL5nH5b/py2MA0GCSqGSIb3DQEBCwUAMIHGMQswCQYDVQQGEwJVUzEQ
MA4GA1UECBMHQXJpem9uYTETMBEGA1UEBxMKU2NvdHRzZGFsZTElMCMGA1UEChMcU3RhcmZpZWxk
IFRlY2hub2xvZ2llcywgSW5jLjEzMDEGA1UECxMqaHR0cDovL2NlcnRzLnN0YXJmaWVsZHRlY2gu
Y29tL3JlcG9zaXRvcnkvMTQwMgYDVQQDEytTdGFyZmllbGQgU2VjdXJlIENlcnRpZmljYXRlIEF1
dGhvcml0eSAtIEcyMB4XDTE4MDUwOTEzNTIxMloXDTE5MDcwODEyNDYwMFowOTEhMB8GA1UECxMY
RG9tYWluIENvbnRyb2wgVmFsaWRhdGVkMRQwEgYDVQQDEwtkdWNrZG5zLm9yZzCCASIwDQYJKoZI
hvcNAQEBBQADggEPADCCAQoCggEBAK0nsIS1nfeEHQUaax+kNhAA0bZSQ/xCidcm5Xfbj099EUca
NbdhdcRHIh9oLa4Sna68Rsfzeyl/sQ5MECjg3dmJ7TvcEXyfEbx2/EAhrMMcisiNIWraGGoA2b24
3y4MMEMy7MAQaMK2FLfele9+Qq4BMIhmo9xfYd7I7QITtBoHufFfuTwq12uUO687kNWHh8dHa7eL
REeAgiZaaKfRP5PccfSwZT/LNgHNsk0SjwTVjIChIeWLH4q4wVmSR1NWL5nGsEyLDx0EiB4yDQyI
FfBCyCW2tm6cVdIsNlr1WCGcQPbg4CGJSRqkEIqtR2WTrJiZm2/HH2YzzoiPYBHqMtkCAwEAAaOC
AtswggLXMAwGA1UdEwEB/wQCMAAwHQYDVR0lBBYwFAYIKwYBBQUHAwEGCCsGAQUFBwMCMA4GA1Ud
DwEB/wQEAwIFoDA9BgNVHR8ENjA0MDKgMKAuhixodHRwOi8vY3JsLnN0YXJmaWVsZHRlY2guY29t
L3NmaWcyczEtMTAxLmNybDBjBgNVHSAEXDBaME4GC2CGSAGG/W4BBxcBMD8wPQYIKwYBBQUHAgEW
MWh0dHA6Ly9jZXJ0aWZpY2F0ZXMuc3RhcmZpZWxkdGVjaC5jb20vcmVwb3NpdG9yeS8wCAYGZ4EM
AQIBMIGCBggrBgEFBQcBAQR2MHQwKgYIKwYBBQUHMAGGHmh0dHA6Ly9vY3NwLnN0YXJmaWVsZHRl
Y2guY29tLzBGBggrBgEFBQcwAoY6aHR0cDovL2NlcnRpZmljYXRlcy5zdGFyZmllbGR0ZWNoLmNv
bS9yZXBvc2l0b3J5L3NmaWcyLmNydDAfBgNVHSMEGDAWgBQlRYFoUCY4PTstLL7Natm2PbNmYzAn
BgNVHREEIDAeggtkdWNrZG5zLm9yZ4IPd3d3LmR1Y2tkbnMub3JnMB0GA1UdDgQWBBSfTZVAxuqj
POjYBMnfDcDzAlhJ2DCCAQQGCisGAQQB1nkCBAIEgfUEgfIA8AB1AKS5CZC0GFgUh7sTosxncAo8
NZgE+RvfuON3zQ7IDdwQAAABY0UtY2cAAAQDAEYwRAIgbZbBehTwoYb3LSH0lQNU7kSXM3UON+WT
oJYfI7V4c18CIC2NhgKEtd2n+e+DbFmT7Z0VlUAo4MxuJatcpbAa1nX2AHcAdH7agzGtMxCRIZzO
JU9CcMK//V5CIAjGNzV55hB7zFYAAAFjRS1kVAAABAMASDBGAiEA6MmBRVoeb1P4r5rxvteyZ6fn
fWMyZmjiwJCpBVT6tEcCIQDgdzI63ntwUh6YNoQsEXAih9v4702plBTk5RymCDM4pjANBgkqhkiG
9w0BAQsFAAOCAQEA2engR6oxMC5KxSYoivchGCsvO956hG6VMe70uaavddgvNYtg6hdkf1JUrSmg
t4EURspzaMuNwq9diN9PQHsQyuS1NGqKlJKWqy/CkYfk4BuwL2P0GP/fhwHbFslk9Ebdb3O7+Zrt
tbjSVWoxsI+UgD0UfGUEy+5wOnA443QUl9G8lUNZdXdKdBd7s831205nc82KLy8tNuLh3PvXQJff
IBqHBbJWnHcxz0MJIWoLx7iDhBYEkQ/qRH5m2uvDDybwICDgd/eY3RuCxt/yZE2Fbj6MZbY+hjOd
57k/kPcAEmUHD8y0i7z3W447+H0gp8IAvkE7u5jB9lNv2PTW5UO5KQ==
-----END CERTIFICATE-----
But for the cert profile you should use the intermediate cert which signed the duckdns cert.
Hope this helps.
Regards,
Remo
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-03-2019 01:59 PM - edited 03-03-2019 02:05 PM
Hi Remo,
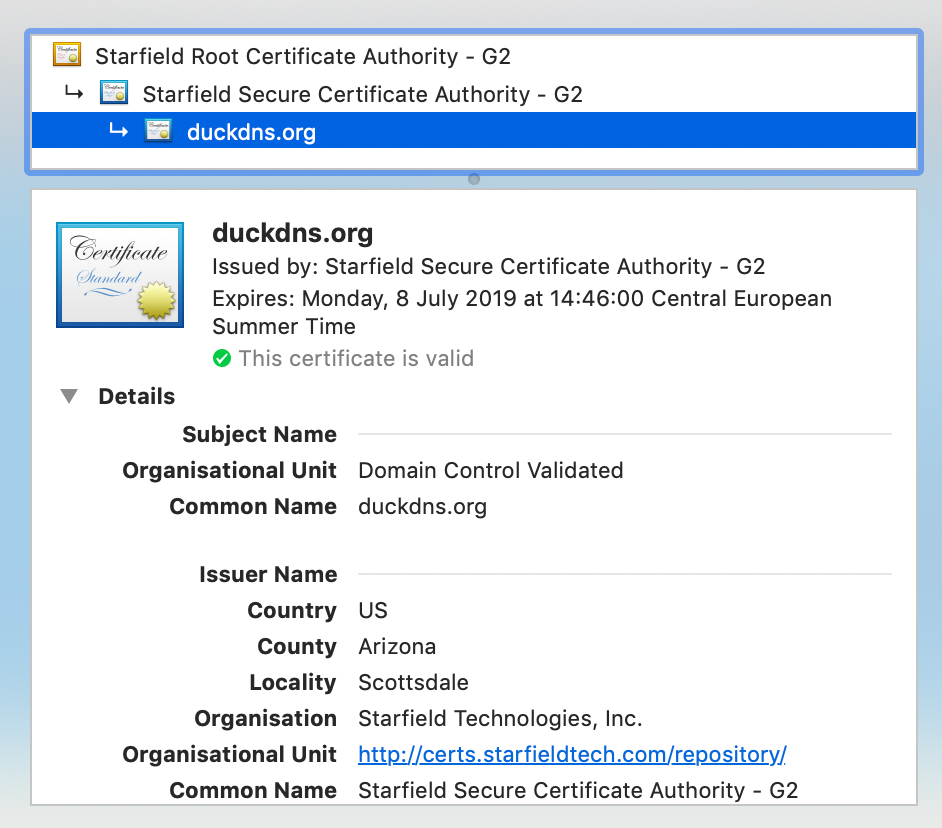
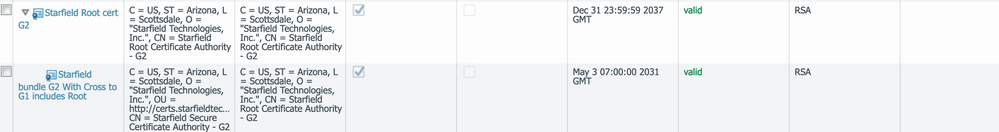
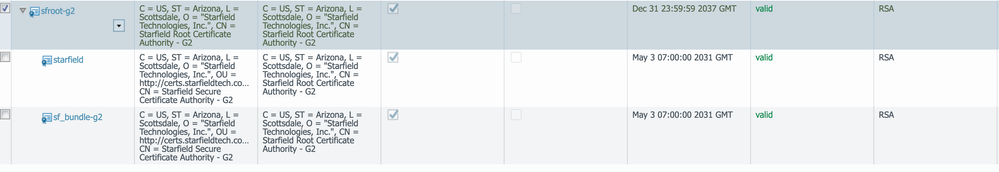
The Duckdns.org cert is signed by Starfield Secure CA GW, so I tried to import the Root G2 and intermediate G2 certificate found on http://certs.starfieldtech.com/repository/
But I still see the following error in the system log when filtering ddns type entries: Server response: 'Peer certificate cannot be authenticated with given CA certificates'
Any clue?
Thanks!
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-04-2019 09:28 AM
Hello,
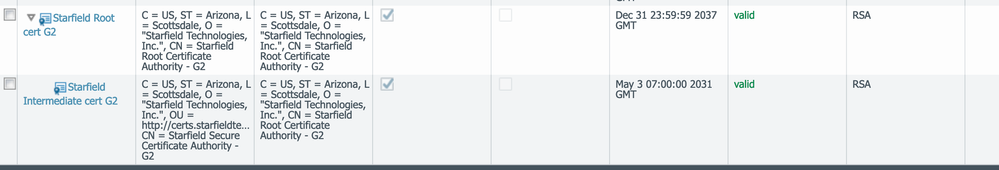
Install the highest certificate in the chain.
The Starfield Root Certificate.
See if that helps.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-05-2019 05:38 AM - edited 03-05-2019 05:40 AM
I've got it running now.
The root certificate was already installed, but I had to import a different intermediate bundle: https://ssl-ccp.secureserver.net/repository/sf_bundle-g2-g1.crt
Thanks
Steven
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-23-2019 09:41 PM - edited 08-23-2019 09:43 PM
I've been having the same issue with DuckDNS DDNS via the Palo Alto and finally got it to work after what seems like hours of downloading certificates from Starfield and trying different combinations... as this was the only post I've been able to find with anything relevant I thought I would add what finally worked for me.
I tried multiple different combinations of intermediate certificates and adjusting other settings.
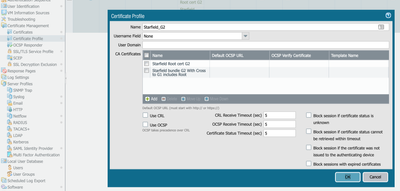
What finally worked was using Firefox, going to www.duckdns.org, opening the SSL certificate properties and exporting the root certificate and each of the intermediate certificates down the chain in order (I numbered the three of them for simplicity.) I then cleared out other test certificates, imported them in order one by one setting the very top one as a Trusted root CA - but not setting any of the intermediates as trusted root CAs and I did not import the DuckDNS certificate itself. I then created a new Certificate Profile and added each of the certificates to the profile in order, set the Certificate Profile that I created in the dynamic DNS profile and saved it.
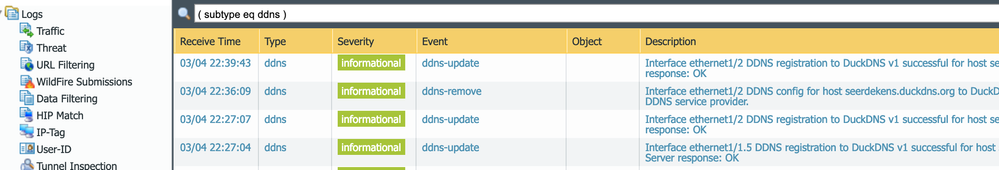
Low and behold a test "dns-proxy ddns update interface name vlan" in the CLI finally worked, when I checked the logs under Monitor -> Logs -> System -> ( subtype eq ddns )
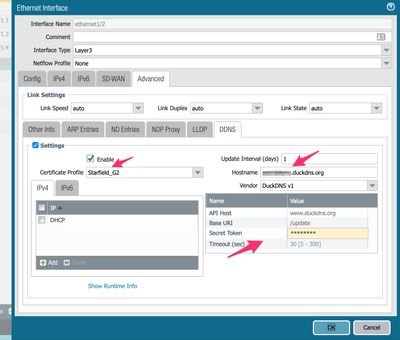
For reference, the Advanced -> DDNS -> Hostname entry was set as the DDNS hostname *without* the .duckdns.org appended. API Host at www.duckdns.org, Base URI at /update, Secret Token pasted in with no spaces or other characters (generally the default DuckDNS v1 settings with my own private key.
Hopefully that saves someone some of the same headaches - seems strange that these aren't trusted by default with OEM provided Certificate Profiles for each service in the OEM provided DDNS profiles.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-30-2019 07:55 AM
Thanks a lot @MichaelJay you saved me a huge headaches on my no-ip dyndns situation... I was about to throw my Palo by the windows. Now need to understand why my GP portal wont pop up ... if you have any insight would be nice
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-03-2019 09:17 AM
Vincent, very glad to hear that it worked, I wasted way too many hours trying assorted settings!
As far as the GP portal popup, I would probably suggest opening a new conversation on topic and giving a lot more detail on what you're having trouble with. I'm not sure what you mean exactly... As far as the GP VPN client which connects to the portal and then the gateway to establish the VPN, we had to make sure a single certificate was issued to each machine from our CA and trusted by the Palo, and remove all duplicate certificates from the clients. There is a setting to enable prompting for authentication, if it's disabled it won't pop-up an authentication request and will only try to do single sign-on authentication. For SSO you need to make sure that you are signing in to the workstation with the GP "credential provider" in windows (should be a globe icon under "more options" before you login, and only shows up after GP is installed.) We also had issues with pre-logon split tunnel settings not refreshing to per user split tunnels - so had to duplicate the settings to make it work. This was a fairly involved setup with a lot of moving parts and multiple TAC calls to iron things out. If you mean some other aspect, I don't have any tips off hand. Hopefully you get it figured out easily.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-26-2019 01:19 PM
Weird, i believe i did the same exact thing but it is still not working for me. Do you mind taking some screen shots of certificates and certificate profile?
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-02-2020 07:10 PM
Thank you @StevenEerdekens!!! Worked like a charm!!! Appreciate your help!
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-03-2020 01:44 PM
Steven,
Thank you very much for taking the time to post this. I feel like the biiggest "rock" in the world right now. I have been trying for two days to download the right files to get this to work. I thought I had them, but it continues to fail according to system logs. Is there any chance you could export the files that worked for you and let me know what order you have listed in the profile? I would be more then greatful and would add you to next years christmas card list 🙂 Seriously, and help would be much appreciated. Thanks, Rick
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-05-2020 11:31 AM
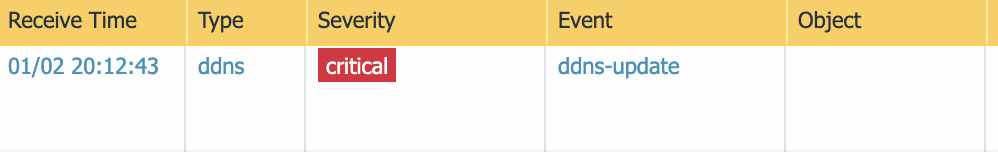
I have been working this for days. I'm thinking it is something else. Can anyone please tell me why I would get a Timeout message? Could it be policy related?
( description contains 'Interface ethernet1/1 DDNS update to DuckDNS v1 unsuccessful for host mybighost with 108.10.11.34 Server response: Timeout was reached' )
*Note I changed host and IP for privacy purposes.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-05-2020 01:16 PM
Figured it out. I had to change the service route configuration under /Device/Services/ServiceRouteConfiguration so the traffic would go out the WAN and not the default MGMNT interface.
- 1 accepted solution
- 27212 Views
- 23 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Errors with Data Redistribution (User-ID Agent) on Labs Environment in Next-Generation Firewall Discussions
- Chromium-based traffic issue in Next-Generation Firewall Discussions
- GlobalProtect portal unresponsive error after upgrade to OSX 15.4 in GlobalProtect Discussions
- GlobalProtect Client updates software not working in GP Portal in General Topics
- Constant "management server failed to send phase 1 to client logd"??? in Panorama Discussions