- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
DynDNS client on PANOS 9.0
- LIVEcommunity
- Discussions
- General Topics
- Re: DynDNS client on PANOS 9.0
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-03-2019 01:37 AM
Hi,
I'm trying to setup DynDNS based on the instructions found at https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-admin/networking/configure-dynamic-dns-for-firew...
I'm using DuckDNS, but I'm stuck at the 'certificate profile' portion. As I understand it correctly I have to import the (public) SSL certificate of DuckDNS, but this is not provided by them.
I don't understand why this is needed since their certificate is signed by Starfield CA, which is already in the list of 'Default Trusted Certificate Authorities' on the Paloalto firewall.
Also other DynDNS provides such as DYN don't seem to provide their public certificates for download.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-26-2020 01:32 PM
Hey Rick.
I've been having a similar problem for while. I solved it by making the URL filtering categories of 'high-risk' and 'dynamic-dns' to alert or allow. Then I imported the certificates I got from a packet capture to that IP. Those certificates were different than what Firefox provided me with. You can find them here:
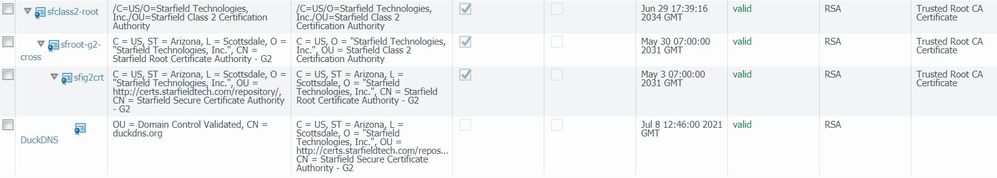
Starfield Class 2 Certification Authority Root Certificate
Starfield Secure Server Certificate (Cross Intermediate Certificate)
Starfield Secure Server Certificate (Intermediate Certificate) - G2
and finally DuckDNS's certificate (note: you will need to save that as a .pem file)
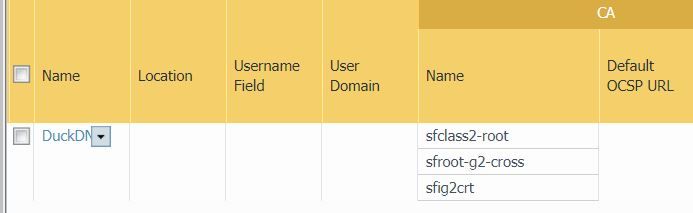
Then I selected all three Starfield certificates in my certificate profile
After commiting I went to the CLI and ran these commands:
test dns-proxy ddns update interface name ethernet1/1
show dns-proxy ddns interface name ethernet1/1
The return code was good.
Hope this helps
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-04-2021 12:38 PM - edited 03-04-2021 12:44 PM
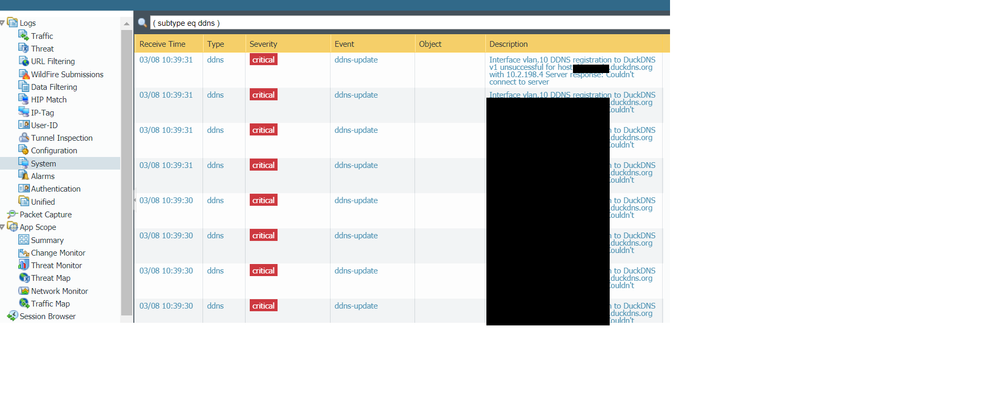
I tried all of the recommendations that were described here. None of them worked. I am currently with a setup and recommendation from MPipes and ddns is not working with DuckDNS service.
error i am getting: 'Interface vlan.10 DDNS registration to DuckDNS v1 unsuccessful for host #####.duckdns.org with 10.xx.xx.4 Server response: Couldn\'t connect to server'
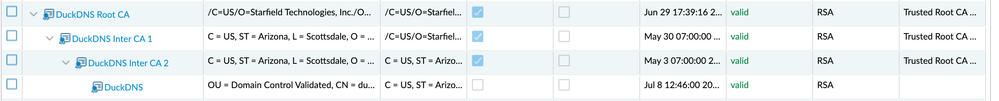
Certificates imported:
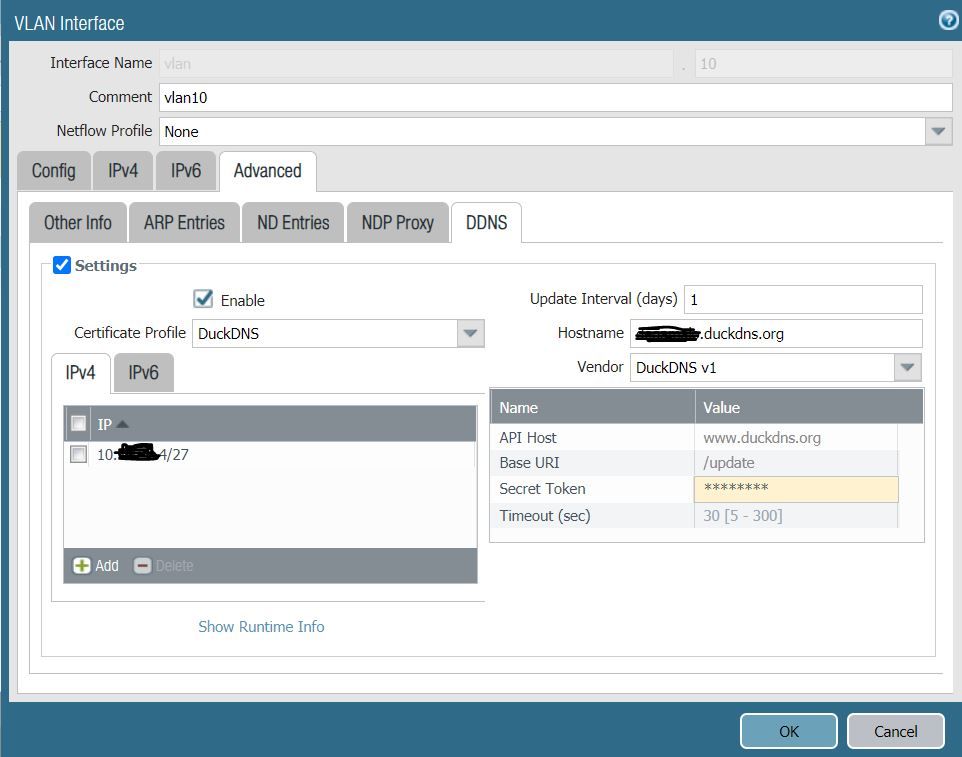
Certificate profile setup:
in my setup I am using vlan that has internet access and setup is as following:
vlan.10 == PA220 == eth1/1 == NAT router = ISP (no security profiles are used in security policy allowing traffic to internet)
Anyone with an idea what to do, what to troubleshoot?
I tried all of the previous recommendations and combinations with certificates and i am out of ideas. Any help more than welcome.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-05-2021 07:49 PM
Make sure you imported the certificates as Trusted Root CA Certificates. I also imported DuckDNS's certificate
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-08-2021 01:50 AM
updated certificates as Trusted CA and imported DuckDNS cert too.
DuckDNS cert cannot be imported under cert profile since it is not a CA certificate.
I am still getting the same error: "Interface vlan.10 DDNS registration to DuckDNS v1 unsuccessful for host ####.duckdns.org with 10.XX.XX.4 Server response: Couldn't connect to server."
after i checked the traffic logs and url logs, whenever i run the "test dns-proxy ddns update interface name vlan.10"
it only generates logs under system logs, no traffic logs for the source.
also debug dataplane shows no logs:
duckdns.org is resolved to 35.165.107.187.
having in mind that vlan.10 interface is local firewall interface that has to match fw policy and nat policy in order to reach to internet ran packet-diag:
admin@PAFW> debug dataplane packet-diag show setting
--------------------------------------------------------------------------------
Packet diagnosis setting:
--------------------------------------------------------------------------------
Packet filter
Enabled: yes
Match pre-parsed packet: yes
Index 1: 10.xx.xx.4/32[0]->35.165.107.187/32[0], proto 0
ingress-interface any, egress-interface any, exclude non-IP
Index 2: 35.165.107.187/32[0]->10.xx.xx.4/32[0], proto 0
ingress-interface any, egress-interface any, exclude non-IP
--------------------------------------------------------------------------------
Logging
Enabled: yes
Log-throttle: no
Sync-log-by-ticks: yes
Features:
flow : basic ager np arp receive ha nd mcast log track cluster pred
ctd : basic
ssl : basic
Counters:
--------------------------------------------------------------------------------
Packet capture
Enabled: yes
Snaplen: 0
Username:
Stage receive : file duck-receive
Captured: packets - 0 bytes - 0
Maximum: packets - 0 bytes - 0
Stage firewall : file duck-firewall
Captured: packets - 0 bytes - 0
Maximum: packets - 0 bytes - 0
Stage transmit : file duck-transmit
Captured: packets - 0 bytes - 0
Maximum: packets - 0 bytes - 0
Stage drop : file duck-drop
Captured: packets - 0 bytes - 0
Maximum: packets - 0 bytes - 0
--------------------------------------------------------------------------------
perhaps i might be wrong, but i do think that pa220 is not making requests to duckdns when i run test dns-proxy ddns update interface name vlan.10, and there is no ssl session for that matter to use certificate profiles.
- Mark as New
- Subscribe to RSS Feed
- Permalink
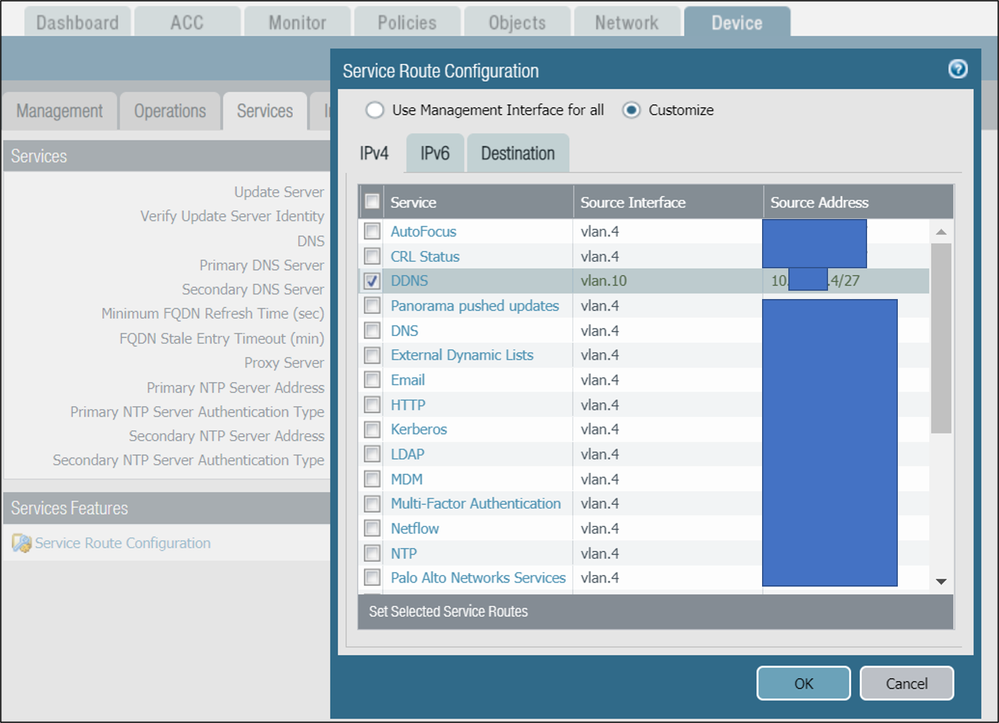
03-11-2021 03:20 AM
Based on my previous update and further digging, the PA was not initiating traffic due to incorrect (default) service route configuration. After changing the setting and placing vlan.10 instead of default value DuckDns started to update properly.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-21-2021 11:36 AM - edited 11-25-2021 01:50 PM
I originally tested without Cert Profile, thinking that PAN would use the the default Internet CA store, but this is not an option. You literally need to download and install the root CA (and intermediate) on PAN, which I think defeats the purpose of PAN-OS having a default CA store. Once you have installed the root CA, then create a cert profile and add the root CA (and intermediate if applicable). I called it cert_profile_1 as I assume I would add more root CAs for other things in the future. You do not need to add the web site cert. So all should be good unless the web site changes to a different root CA. It would be great if PA has the option to 'use default cert store' instead of an explicit cert profile.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-21-2021 02:10 PM
Hi @johnwalshaw
Setting the cert profile to none is not possible here, at least on 10.1.3
The error I get when saving the interface settings:
"Operation Failed ethernet1/1 -> layer3 -> ddns-config constraints failed : DDNS Cert Profile missing ethernet1/1 -> layer3 -> ddns-config is invalid"
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-25-2021 01:52 PM
Agreed and understood. I updated my original post. I have tested DDNS successfully now. Seems like a weird method considering there is a default CA store, which is inexplicably unavailable for a public internet public CA URL.
- 26706 Views
- 23 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Errors with Data Redistribution (User-ID Agent) on Labs Environment in Next-Generation Firewall Discussions
- Chromium-based traffic issue in Next-Generation Firewall Discussions
- GlobalProtect portal unresponsive error after upgrade to OSX 15.4 in GlobalProtect Discussions
- GlobalProtect Client updates software not working in GP Portal in General Topics
- Constant "management server failed to send phase 1 to client logd"??? in Panorama Discussions