- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Global Protect config problem: The server certificate is invalid.
- LIVEcommunity
- Discussions
- General Topics
- Re: Global Protect config problem: The server certificate is invalid.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Global Protect config problem: The server certificate is invalid.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-08-2018 05:42 AM - last edited on 03-20-2020 07:19 AM by arsimon
Hello,
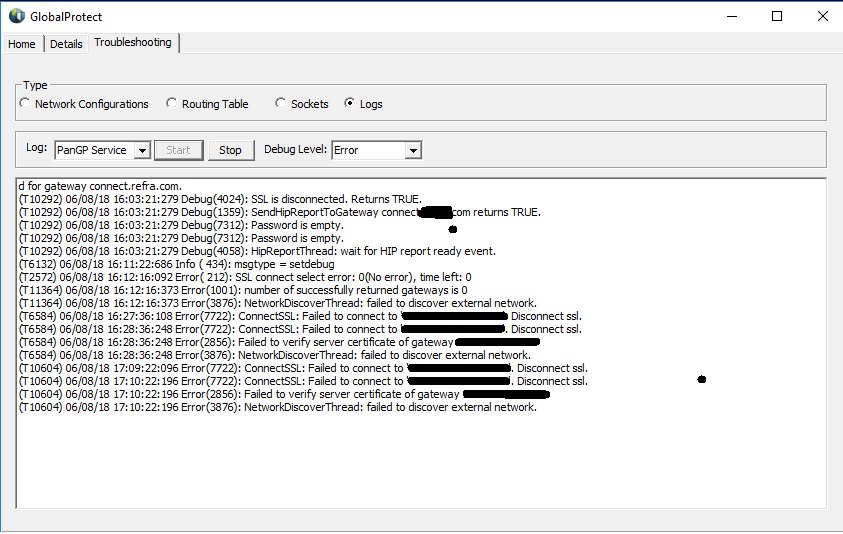
we are not able to connect to one of our Gateways anymore. We get the error: The server certificate is invalid.
I checked the following but this looks correct:
- Incorrect time settings on the firewall.
- Check the certificate's validation dates (valid from and valid until) to make sure the date range is correct.
- Check the Time Setting on the firewall. Use NTP if the time stamp isn't accurate.
We have a certificate with an IP adress, no FQDN.
Here is the log of the client:
The Gateway was wortking normally until today.
Anybody that can help me out with this?
- Labels:
-
GlobalProtect-COVID19
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-08-2018 08:03 AM
Are you positive that the server certificate is actually valid and wasn't pulled by whoever issued it to you? Do you connect via the IP address or an FQDN that you've configured?
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-11-2018 01:05 AM
Thank you very much for your reply.
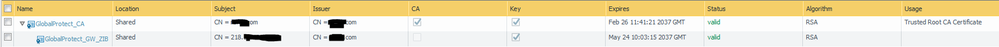
The certificate is self issued from our local root-ca.
The local firewall and the portal-firewall show it as valid:
We caonnect to the IP-adress, FQDN is not used in this case.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-11-2018 04:46 AM - edited 06-11-2018 04:48 AM
Did you tried to add this certificate as trusted in portal configuraion? Portal will send this certificate to agent as trusted. It helps a lot if there is an issue with verification of root certificate on client.
Do you have IP address of gateway configured on portal configuration?
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-11-2018 08:39 AM
1. If you browse to the GP portal address, do you receive any certificate errors?
1.1 If yes, and this is a publically signed certificate, there is an issue with the certificate chain. From the screenshot you sent there is only one root certificate, when I would expect one more, the intermediate certificate.
1.2 If yes, and its a self signed certificate, no issue we will get to this next.
2. The common name of the certificate needs to match the IP address of the GP gateway as specified in Network -> Portals -> Portal name -> Agent -> Agent name -> External/internal -> Gateways -> "IP Address"
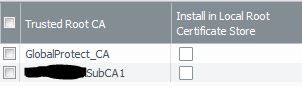
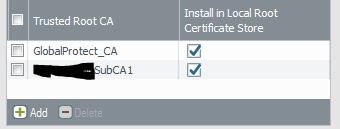
3. If yes to 1.2 then you can get the GP client to automatically import the root certificates to the machines trusted root store as per the below configuration. However as per point 1.1 I believe not all root certificates are present on the firewall.
Network -> Portals -> Portal name -> Agent -> Trusted Root CA
Select the boxes "Install in Local Root Certificate Store"
Thanks,
Luke.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-12-2018 01:45 AM
Hello,
Thank you for the advice. Can you tell me please where I can find ths point (add this certificate as trusted in portal configuraion)?
Is it unbder Network --> Global Protect --> Portals --> <Portal_Name> (GlobalProtect Portal Configuration) --> Agent ?
I'm sorry, I'm not that familier with the GlobalProtect Configuration, because I have not setup iut by myself
In the portal configuration we use the IP-adress (not FQDN)
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-12-2018 01:58 AM
Hi.
This step is only necessary if the certs are self signed. If you check both check boxes "Install in Local Root Certificate Store" the GP client will install the certs in the trusted root CA store so the client trusts the certs.
Are your certs publically signed? If yes, this isn''t necessary. If you browse to GP portal do you get cert errors? If yes there is something wrong with chain.
Thanks,
Luke.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-12-2018 02:04 AM
Hello Luke, thank you for your reply.
1. On the GP portal website we get a warning (issuer of the certificate is unknown). But this is always happening and there are no problems with GP gateways in other locations wich are also configured with this portal.
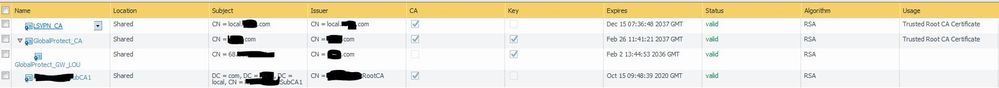
1.1 That is correct. It was just filtered out. Here a screenshot with all certificates of the gw:
2. IP and CN are exactly the same. It was working with this configuration over months without problems before.
3. I will activate this setting and check again
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-12-2018 02:08 AM
Hi,
There is definitely something wrong with the certificate chain. The primary certificate looks to be signed by the root CA and not the intermediate. The primary certificate also marked as "certificate authority".
What I would expect
Root CA (Common name can be anything), marked as Certificate Authority
Intermediate CA (Common name can be anything), marked as Certificate Authority, signed by root CA
Primary Certificate (Common name is IP address), not marked as Certificate Authority, signed by intermediate CA.
Then attach the primary certificate to a SSL/TLS profile; attach this profile to the "authentication" tab of any relevant portals and gateways.
Thanks,
Luke.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-12-2018 02:49 AM
Hello,
the strange thing is that it was wortking with this configuration for a long time before.
We have other similar configured gateways, that are still working now without this issue:
Here an example from another gw.
- 40489 Views
- 9 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Can't import a certificate via XML API using C# in General Topics
- Python Script isn't being executed completely in Cortex XDR in Cortex XDR Discussions
- GP Connection Failed - gateway could not verify the server certiticate of the gateway. in GlobalProtect Discussions
- Problem Using New Digitally Signed Certificate in GlobalProtect Discussions
- SSL Inspection in Next-Generation Firewall Discussions