- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Global Protect Gateway - Split-Tunnel Exluded Domains
- LIVEcommunity
- Discussions
- General Topics
- Global Protect Gateway - Split-Tunnel Exluded Domains
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Global Protect Gateway - Split-Tunnel Exluded Domains
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-06-2020 08:29 AM
Hello
I am trying to exclude some domain from coming through the gateway to improve user experience so they are not hair-pinning through our DC's
at the moment I have no access route entered so I am running 0.0.0.0/0 out of our DC's - there are are certain domains for Microsoft updates, teams and hosted business services
when I add them to exclude domain it seems to work correctly - for example if I add www.bbc.co.uk this will browse local as expected but all other websites are stop working
I was hoping when I add excluded domains to browse local, what remains continues to hairpin via the DC;s
I have been trying to find a wildcard I could enter in the include domain to continue to get the internet working but this does not seems to work
are there some examples there people are using to I can see what I am doing wrong? I have been through the admin documents but maybe I am missing something
is there something I an doing wrong here or am I expecting more than is possible?
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-06-2020 04:17 PM - edited 04-09-2020 06:32 PM
Hello Jake,
Do you have a valid GlobalProtect lincense (subscription) installed on your firewall(s)?
As soon as you were able to exclude traffic by configuring domain based split-tunneling, I do not think that it is the case. But, it would be worth to check your GlobalProtect license, because of split tunneling based on destination domain, client process, and video streaming application is required valid subscription. See more details here.
What is a version of PAN OS you use?
Could you please share a part of your GlobalProtect configuration related to split-tunneling?
What is an output of the command 'route print' on a PC connected to VPN gateway?
As a good example of split domain and application feature configuration you can use the document here.
Best regards,
Daniel
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-06-2020 05:20 PM
Hello,
If I understood correct, you could access www.bbc.co.uk via your ethernet/wireless adapter AND also all of the RFC 1918 or interested traffic is traversing your local adapter as opposed to go across the tunnel?
If this is the case, did you try adding adding RF1918 to access route Include tab and non-interested traffic to exclude tab?
Alternatively, you could just add the domains or app-id's under Domain and Application to specific's you need.
Hope this helps.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-07-2020 08:09 AM
Hello
thank you for the replies
I think I have a mixture of problems here - I look to have the split-tunnel working in out test environment just when I move to production I hit issues so its defiantly my issue to resolve - and most likely related to out HIP/browsing rules we have in place so I need to dig this out now
the new question I have now is if something is blocked by a policy, is that ignored if the exclusion is in? - I have not tested this yet so thought it might be easier to ask
for example - we block Netflix
if I was to exclude *netflix.com
and also add it to the exclude video traffic from the tunnel as Netflix-base, Netflix-streaming
would it then be allowed to VPN users? and would it be logged anywhere if allowed or denied?
PanOS - 8.1.4
GP - 4.1.11
PA - 3020
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-07-2020 08:56 AM
Hi Jake,
Is there any reason why you're still running 4.1.x? Take a look here to check out EOL summary: https://www.paloaltonetworks.com/services/support/end-of-life-announcements/end-of-life-summary
Once you've excluded that video traffic and excluded domain traffic, it will be routed using physical adapter and not via GP adapter.
Regards,
Varun
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-07-2020 09:21 AM
thank you,
yep I have been made aware of the EOL the problem I have is a have roughly 5000 users across multiple gateways all working from home due to COVID-19
our remote machines do not have admin rights granted and also do not have a local admin account direct on the machine so if we have any problems during upgrading these clients we could possibly disable remote working for multiple users as out support teams cannot install without the machine being directly on the domain for the correct rights
so at the moment it is not a risk is way to high to consider
I will be testing my exclusions tonight - the best tests I can do it with whatismyip.com to see if the IP changes to the local breakout rather than a DCs
is there a better way to test?
I can start packet tracing but it seems a bit too far to proof it is working
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-07-2020 09:32 AM
Hi Jake,
Please go through this document to troubleshoot split tunnel (domain) and exclude video traffic. Hope this helps 🙂
Regards,
Varun
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-07-2020 10:52 AM - edited 04-07-2020 11:17 AM
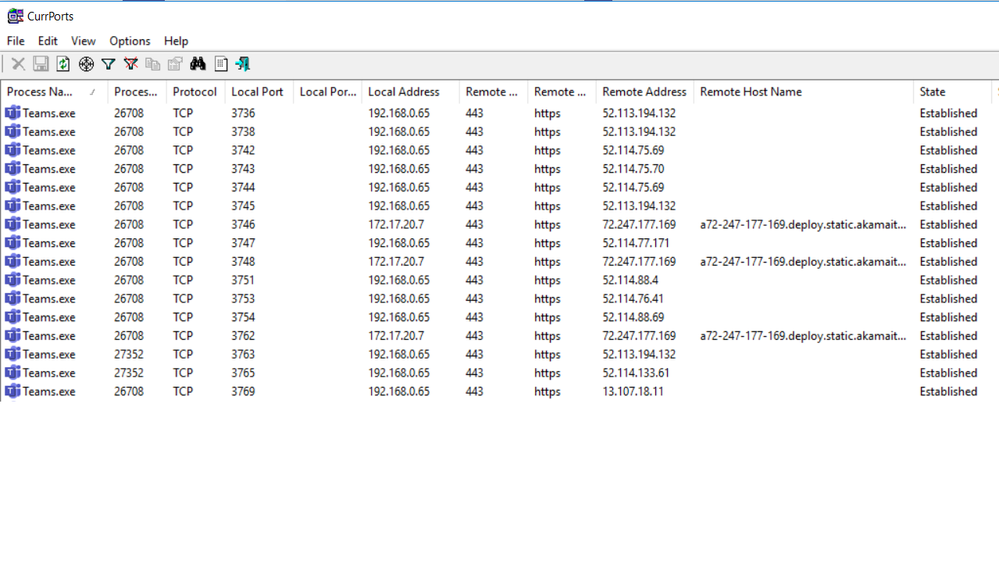
download and run currports.
it can display running processes and show the source address. this will determine if tunnelled or split.
screen shot below .. PS I have just added teams as a filter but you can see all or add whatever you like.
the 192.168 is my wifi and 172.17 GP address.
also... anything local will not be affected by your firewall policies. if you need to block it then don't split it.
also2... lots of bugs in domain split tunnelling below 5.0.7...
HTH.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-08-2020 01:57 AM
thanks Mike
I will try that now
also how are the excusing teams? but application directory or the URLs they publish on the MS website?
are you able to share a screenshot?
the company want to start doing weekly announcements not to everyone via a live stream and looks like teams will be the preferred method - so its a new thing I need to now try and split
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-08-2020 02:27 AM
we have tried all...
application directory was unreliable as this is installed under the users profile, also... the use of "%LOCALAPPDATA%\Microsoft\Teams\Teams.exe" is not currently supported by Palo.
Domain Split Tunnel was also unreliable as we have a few thousand users under version 5.01.
so we now use IP addresses.
you can make your own choice about which ones to use from here.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-09-2020 07:09 PM - edited 04-09-2020 07:11 PM
Hello @Jake.Ryan
I found the example of split-tunneling configuration based on IPs for Office 365 apps here.
Based on information in the section # 4 we can use IPs for the next few months:
"Per the information provided by Microsoft team, the current intent is to hold these subnets/IP addresses static for the next few months in order to allow for quick customer deployments related to the COVID-19 situation. In long term, customers would need to either build automation to keep this configuration up to date, or follow the suggestions and subscribe to update notifications at: https://docs.microsoft.com/en-us/office365/enterprise/office-365-ip-web-service#update-notifications".
Please note we could not add Address Group as an Exclude Access Route to the firewall that is running PAN-OS 8.1. It looks like this feature is available in 9.x only. We just added Addresses.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-09-2020 07:24 PM - edited 04-09-2020 07:25 PM
Hello @Jake.Ryan
I found the example of how to configure split-tunneling for Office 365 apps using IPs here. Based on info in the section #4 of the instruction, Microsoft is going to use the same IPs during next few months.
Please note we could not to add Address Groups as Exclude Access Routes on the firewall that is running PAN-OS 8.1. It looks like this feature is available in 9.x version only.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-08-2020 10:04 PM
I ran into this issue once SIP was issued on March 15th and most employees started to work from home. Although we had domains such as *.zoom.us, youtube.com, 8x8 etc defined in GP to NOT use the tunnel, traffic kept accessing via the tunnel even though configuration was correct . We are on Pan0S 9.0.5. I spent several days with support. When we switched from using domain names to IP address ranges the issue went away. This issue was not DNS related as internally we use the same DNS servers VPN clients use and internally we had no issues resolving DNS. Fix was to use IP addresses in the split-tunnel config until PAN figures out the bug.
- 7638 Views
- 13 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!