- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
How to limit global protect for specific android/ios users?
- LIVEcommunity
- Discussions
- General Topics
- Re: How to limit global protect for specific android/ios users?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
How to limit global protect for specific android/ios users?
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-18-2018 09:04 AM - edited 06-18-2018 09:20 AM
I have an interesting scenario. We have windows users accessing global protect. I am looking to buy gateway license to enable a set of users(10) out of 400 users to use android/iphone to connect to vpn. We have IBM MaaS360 MDM installed on phone to collect mobile attributes. Is there a way I can enforce a policy to limit specific users to use mobile phones?
Your help is greatly appreciated. TIA
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-18-2018 09:37 AM
There is actually a few different places that you could do something like this.
1) You could build out a special Authentication Profile specific to a group that is allowed to login via mobile devices and set the GlobalProtect Portal 'Authentication' Client Auth settings to include an entry that specifically lists the OS as [ Android iOS WindowsUWP ] and limit the other Client Auth settings specific to [ Browser Linux Mac ] and any user not included in the new profile simply couldn't auth if they attempted to utilize a mobile client.
This option would limit the Auth from a Portal perspective.
2) You could do the exact same thing but from the Gateway Auth page.
You could take it a step further and utilize a HIP check and the Agent Client Settings but that gets messy and isn't really required if you do either of the two options above.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-18-2018 09:38 AM
Hi,
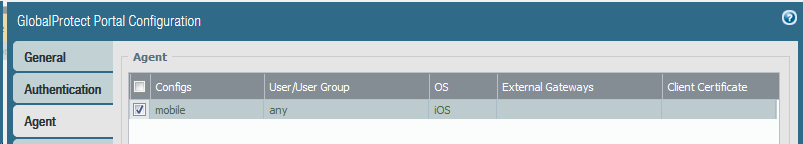
a) There are two ways you could do this, limit the OS in the portal agent configs section
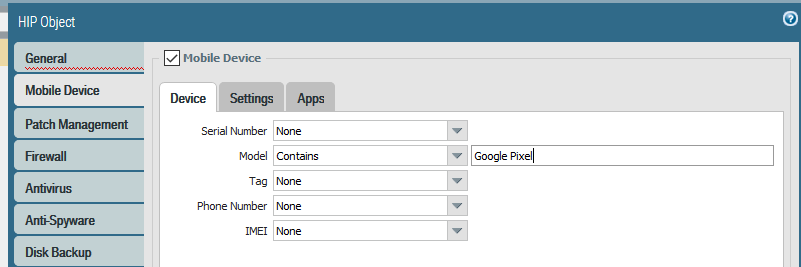
b) with GP gateway license you can enforce policy upon HIP objects. one HIP object is moible device model
Thanks,
Luke.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-18-2018 10:53 AM
@LukeBullimore wrote:Hi,
a) There are two ways you could do this, limit the OS in the portal agent configs section
This probably is the easiest/best way. Here you could specify a usergroup, so only users of that usergroup receive the configuration for Android/iOS devices. Other users will be able to login to the portal actually but cannot connect as they will not receive the required configuration.
But if you already have an MDM, you don't really need the Gateway license. With the MDM for example you could deploy a client certificate to the specific devices and so only these devices will be able to connect. This does not require the gateway license as you would use the integrated VPN clients on the mobile devices.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-18-2018 01:49 PM
@BPry Thank you so much for your suggestion. We have users authentication against our RADIUS server which utilizes one-time-password. Doing this will require me to configure other auth method(preferably local) but this is not what my organisation is looking for. I am little confused at this point.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-18-2018 01:51 PM - edited 06-18-2018 01:51 PM
@LukeBullimoreShouldn't I need a MDM to get the mobile attributes? We have a cloud based MDM server and unsure if the vendor provides HIP info.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-18-2018 01:55 PM
@Remo Your suggestion boils down to authenticating GP users based on client certificates? I dodnot want to make any kind of changes to exisiting windows users and add specific mobile users to exisiting gateway and portal. will this be addressed? Please correct me if I am wrong.
Thanks.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-18-2018 02:20 PM
You're right this "little" detail was missing in my post. But you could solve this with a dedicated global protect gateway for the iOS/Android devices.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-19-2018 01:31 AM - edited 06-19-2018 01:32 AM
Hi @SThatipelly
@SThatipelly wrote:@LukeBullimoreShouldn't I need a MDM to get the mobile attributes? We have a cloud based MDM server and unsure if the vendor provides HIP info.
No you don't. The GlobalProtect App that is run on the mobile device is capable of pulling this information - so provided you have the Gateway License you can make full use of this functionality.
Thanks,
Luke.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-19-2018 05:30 AM
@LukeBullimore I had gone through that document before and found this little note:
To collect mobile device attributes and utilize them in HIP enforcement policies, GlobalProtect requires an MDM server. GlobalProtect currently supports HIP integration with the AirWatch MDM server.
This is what concerning me.
- 4430 Views
- 9 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Unable to access resources on specific gateways for single user while on global protect in GlobalProtect Discussions
- SSL-VPN High Availability in Panorama Discussions
- Request for Delisting of Qnovate.com from Palo Altos firewall Blocked Sites in VirusTotal
- Cortex Data Lake - Looking for a sting of data in the Description field in General Topics
- HIP Checks failing GP failing GP users called in ACL's when source device is Apple in GlobalProtect Discussions