- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
IPSec Site-to-Site between PA-200 and PFSense one direction route only
- LIVEcommunity
- Discussions
- General Topics
- Re: IPSec Site-to-Site between PA-200 and PFSense one direction route only
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
IPSec Site-to-Site between PA-200 and PFSense one direction route only
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-07-2017 02:30 PM
Hi All!!
I setup a IPSec site-to-site VPN between PA-200 and PfSense using this how to: https://blog.kingj.net/2014/08/24/how-to/setting-up-a-policy-based-ipsec-vpn-between-a-palo-alto-pa-...
P1 and P2 is ok and I can access network from PA-200 to PfSense but from network PfSense side to PAN network side I can’t access.
Anyone have any idea?
Thanks a lot!!
Rodrigo
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-08-2017 02:10 AM
Hi,
Looks like palo works fine. Did you check pfsense logs, security policy and NAT rules (if any)?
Thx,
Myky
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-23-2017 04:47 AM
Thank you for your quickly response.
Sorry for delay, but I was sick in last weeks.
Yes, I checked and I can't see any error.
Before we put Palo Alto, we had 2 PfSense working very well, after when we changed 1 PfSense by Palo Alto the IPsec don't work anymore.
Best regards
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-23-2017 04:53 AM
Hi,
How do you have your security policy set up?
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-23-2017 07:49 AM
To add to this without displaying any logs or security policies beforehand nobody is going to be able to point you in the right direction. It sounds like the Palo Alto is likely setup perfectly fine but you could be missing a rule on the PA-200 to allow PFSense back into the PA-200 network, or the PFSense could be stopping the traffic before it ever gets to the PA-200.
Check over the security policies, double check your route entries on both sides and possibly post screenshots for both. If the tunnel is up perfectly fine then it really sounds like a routing or security rulebase issue.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-23-2017 09:13 AM - edited 01-23-2017 09:17 AM
Hi,
Where is your external VPN IP addresss assiged. Into which zone? How is the traffic flowing from PFSense > Palo?
Thx,
Myky
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-23-2017 10:12 AM
One thing I would highly recommend is the following.
1) Temporarly override the interzone-default policy and enable log at session start and log at session end. Verify in the logs that you even have a rule allowing the traffic to come back.
2) Once you have the tunnel up what IP address are you assigning these users; they will need a rule to allow them to the specified zones that they need access to.
Once you have enabled the additional logging you should be able to tell if the traffic is at least being forwared from your PFSense correctly and if it's actually hitting the PA-200. If you aren't seeing the traffic then you need to look at the routing on the PFSense and make sure it's correct, along with any security policy that needs to be in place to allow the traffic. If it's hitting the PA-200 but it's being denied then you need to create a rule to actually allow the traffic to come back in.
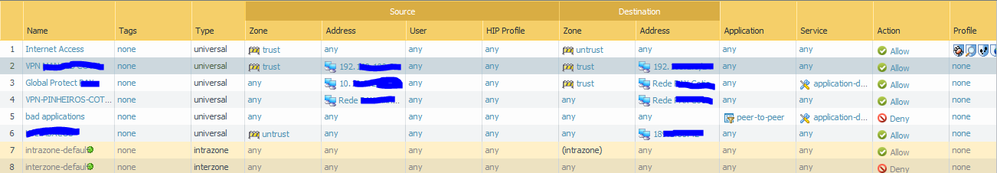
The information that you are feeding kinda needs to be more detailed. Currently with the screenshot that you provided I'm unsure which rule(s) you believe are associated with your tunnel. Generally you would segregate your IPSec tunnels into a different security zone besides 'untrust' or 'trust' and we could at least identify them like that, since you are not doing that we can't tell what zone the IPSec traffic should really be identified under. I'm also completely unaware of how your route table looks, what the config on the other end looks, or anything of the like. I'm not trying to put you off or come off like an ass, but you need to provide a little bit more information if you want help. Enabling the additional logging will give you a fair hint on where the issue actually is and we can go from there.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-23-2017 12:33 PM
@BPry nice long email. Anyway as more info we got the easier and quicker we can help/advice. Same info needed on what you have already done.
- 11274 Views
- 8 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!