- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Never ending globalprotect VPN drops
- LIVEcommunity
- Discussions
- General Topics
- Never ending globalprotect VPN drops
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Never ending globalprotect VPN drops
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-28-2018 07:08 AM
Supporting VPN for people is a challenge no matter what VPN you are using but people never consider the reliabilty of their own ISP provider as part of that issue. So what is the best way to rule out the users ISP as the problem and not the globalprotect client/VPN access? But to be fair I do not want to rule that out either . This my users complaint :
We have been having an issue with the Global Protect client dropping us seemingly randomly when are connected. Sometimes we are remoted into local machines working in Clarion and/or Sybase. Other times we are remoted into our local machine and are dropped. The message we get sometimes is Global Protect is trying to reconnect and will do so in x amount of seconds. A user has been working from home this last hour and is having issues with this. We do need assistance as sometimes it is critical for us to remain connected to respond to an immediate issue. Could you please provide assistance?
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-28-2018 09:49 AM
Hello,
I feel your pain :(. What do the client GP logs state? I know its tought ot get them sometimes, but there could be an indicator. Also check the timeout settings, maybe they are too short? Also check the versions of GP and see if there are any known bugs, this has bitten me a few times in the past. I would probably even open a case with TAC and get their input on the issue.
Just some thoughts.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-28-2018 11:03 AM
I checked the timeout setting and they are set to 180 minutes or 3 hours. Yes tough to either get the users to collect them for you or to get them to sit down and collect the logs with you. I did some testing and I don't have any issue that they are having with any of the GP versions. The method they are using which is to VPN into their desktop at work and then work from it is not one that I would recommend to anyone. Not sure why we allow it
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-28-2018 05:11 PM
@jdprovine wrote:The method they are using which is to VPN into their desktop at work and then work from it is not one that I would recommend to anyone. Not sure why we allow it
That's probably the most common way people use a VPN connection back to their organization, just FYI. The only people utilizing VPN to simply connect back to internal resources via their machine are auditors provided a laptop and everything they do is local to that one machine. The rest of my users will always remote back to their desktop sitting at the Agency building or in the Capital.
I'd say that out of all of my VPN connections active at any given time only 20-ish are actually using the VPN as you are expecting; everyone else does exactly this.
As you've already stated however really the only thing you can do is hammer home the fact that it's their connection causing the issue. If need be have them work from a laptop via the VPN when they are on-site with a stable 'guest' connection that doesn't have any access to internal resources; when the issue doesn't reappear with a known good connection that's usually enough for me to drive the point home.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-29-2018 05:20 AM
Yeah this has been brought to me repeatedly by the same people they want somehow to have it work exactly the same as if they were sitting at work at their desk and there are too many variables outside my control to provide that. It like wireless, its never going to be as reliable as being plugged in with a cable no matter how many people complain about it. Quite frankly I never have the issue that they do so all i can do is run some trouble shooting tell them the same thing and then wait for them to come back again later. They always blame the palo and the globalprotecte client but never their own ISP LOL. FYI I did expect these people to use this method because they are IT people in my own department LOL
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-30-2018 05:08 AM
@BPry @OtakarKlier @jdelio @reaper
How to I download or get the logs for support if my VPN client,version 4, does not have the collect log button?
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-30-2018 05:52 AM
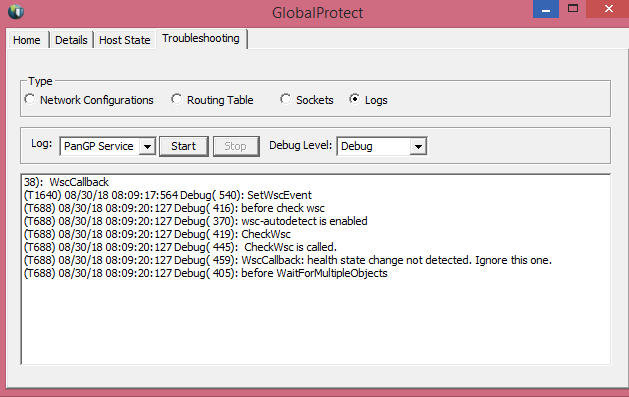
there's nothing under settings > troubleshooting?
they can also be collected from your system
on my MAC they're in
/Library/Logs/PaloAltoNetworks/GlobalProtect/
on a windows machine they should be under
%HOMEPATH%\AppData\Local\Paloaltonetworks\GlobalProtect
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-30-2018 06:21 AM
Well we are using version 4 of globalprotect and it does not have a settings tab but it does have a troubleshooting tab but no collect logs button. I want to make sure that I give the right logs to TAC and their instruction did not fit my situation and so far they have not responded to my question concerning that fact
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-30-2018 06:24 AM
did you click the 'start' button to start collecting logs? (just guessing here)
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-30-2018 06:32 AM
Does this only collect when you have logging turned on and what is the best logging setting to use to determine the drops
%HOMEPATH%\AppData\Local\Paloaltonetworks\GlobalProtect
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-30-2018 06:39 AM
To troubleshoot i'd go with 'debug' level. After you're done set it back to 'info'
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-30-2018 06:41 AM
I'd look at upgrading to 4.1, as you get a few more options when it when it comes to troubleshooting and a real nice 'Collect Logs' button that will grab all the log files and zip them up for you; really easy to get people to get you log files at that time.
As @reaper mentioned the AppData folder will hold a few of the logs regardless of what you have for Troubleshooting settings that might be helpful.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-30-2018 06:51 AM
Yes and I have done the collecting of logs before, I just want to make sure I get the logs that TAC needs to help diagnose if there is an issue
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-30-2018 06:52 AM
Set to panservice not panagent?
- 12755 Views
- 26 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Slowness in a specific gateway in GlobalProtect Discussions
- End users selects DENY on the MFA prompt on the phone still are able to connect to GlobalProtect agents in General Topics
- GlobalProtect never-ending "Finding the Best Available Gateway" in GlobalProtect Discussions
- GlobalProtect | External Gateway | SAML | Reconnect Issue in GlobalProtect Discussions
- Unable to connect GlobalProtect in Next-Generation Firewall Discussions