- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
One-to-One NAT - DMZ to inside - how do I make it work?
- LIVEcommunity
- Discussions
- General Topics
- One-to-One NAT - DMZ to inside - how do I make it work?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
One-to-One NAT - DMZ to inside - how do I make it work?
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-25-2013 08:44 PM
Folks.
I'm apparently having a particularly stupid day, because I can;t make something as simple as one-to-one NAT work.
Scenario is this.
I have an IP in my DMZ. I have assigned this IP to a particular server which is hosted on my INSIDE (secure) network.
All I want to do is take this IP address and NAT it to the inside address. Something like this
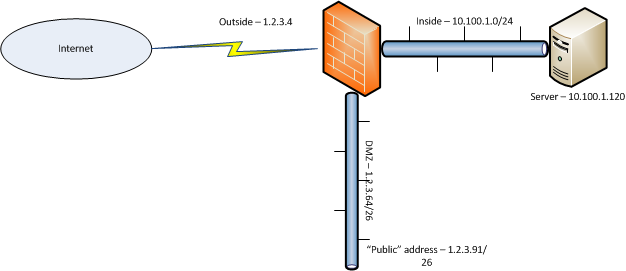
IP addresses have been changed to protect the stupid (me!).
So - request comes in from the web to 1.2.3.91, and I want to redirect it to 10.100.1.120 - only needs web browsing and PING.
but I can not, for the life of me, get it right.
I've got the following NAT rule
Original packet
Source Zone - Outside
Destination Zone - DMZ
Source Address - Any
Destination Address - 1.2.3.91
Translated Packet
Source Translation : None
Destination translation : 10.100.1.120
The security policy is as follows
Source : Outside
Source Address : Any
Destination : Inside
Destination Address : 10.100.1.120
I'm happy for anyone to point out where I'm being stupid and laugh at me - I know it's something obvious, but I'm banging my head trying to sort out what.
thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2013 09:31 PM
Hello Darren,
Please try below mentioned CLI command and share the O/P.
admin@62-PA> test security-policy-match from <source zone> source <IP address> destination <IP/MASK> protocol YY destination-port XX
admin@62-PA> test nat-policy-match source <IP public address> destination <IP address> protocol YY destination-port XX
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2013 10:24 PM
HULK wrote:
Hello Darren,
Please try below mentioned CLI command and share the O/P.
admin@62-PA> test security-policy-match from <source zone> source <IP address> destination <IP/MASK> protocol YY destination-port XX
admin@62-PA> test nat-policy-match source <IP public address> destination <IP address> protocol YY destination-port XX
Thanks
first one (I've replaced the actual outside address)
darren@Ai-Gate(active)> test security-policy-match from outside source 110.142.210.164 destination 1.2.3.91/32 protocol 1
Confluence-Outside-in {
from outside;
source any;
source-region none;
to inside;
destination 1.2.3.91;
destination-region none;
user any;
category any;
application/service [ icmp/icmp/any/any web-browsing/tcp/any/80 ping/icmp/any/any ];
action allow;
terminal yes;
}
Second one
darren@Ai-Gate(active)> test nat-policy-match source 110.142.210.164 destination 1.2.3.91 protocol 1
Destination-NAT: Rule matched: Inbound NAT Confluence
1.2.3.91:0 => 10.100.1.120:0
darren@Ai-Gate(active)>
I can't see a problem with either one, yet I can't PING the damn thing from the outside! I've definitively confirmed the host is online, has no local firewall running, and has a route to the internet. The NAT rule for this incoming is placed "above" my general-purpose NAT rules, so it should be processed first.
I am now officially scratching my head.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2013 10:49 PM
Can you add the o/p for following commands to this discussion
>show running nat-policy
>show routing route
Also start a continuous ping to the DMZ public IP and monitor the session table:
>show session all filter source <ip>
if you see any PING sessions displayed add the following o/p with this discussion
>show session <id>
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-27-2013 03:13 PM
akawimandan wrote:
Can you add the o/p for following commands to this discussion
>show running nat-policy
>show routing route
Also start a continuous ping to the DMZ public IP and monitor the session table:
>show session all filter source <ip>
if you see any PING sessions displayed add the following o/p with this discussion
>show session <id>
Running nat policy (somewhat obfuscated) - there are other components, but they refer to interfaces which aren't part of this problem.
"Inbound NAT Confluence" {
from outside;
source any;
to outside;
to-interface ;
destination 1.2.3.91;
service any/any/any;
translate-to "dst: 10.100.1.120";
terminal no;
}
No-NAT-DMZ {
from inside;
source any;
to DMZ;
to-interface ethernet1/3 ;
destination any;
service any/any/any;
terminal no;
}
"No-NAT Internet Router" {
from inside;
source any;
to outside;
to-interface ethernet1/2 ;
destination 1.2.3.2;
service any/any/any;
terminal no;
}
No-NAT-inbound-DMZ {
from outside;
source any;
to DMZ;
to-interface ethernet1/3 ;
destination any;
service any/any/any;
terminal no;
}
"Outbound Nat" {
from inside;
source any;
to outside;
to-interface ;
destination any;
service any/any/any;
translate-to "src: ethernet1/2 1.2.3.1 (dynamic-ip-and-port) (pool idx: 1)";
terminal no;
}
Some explanation - I have a /24 available on my router/firewall. 1.2.3.0/30 is used as a point-to-point link between my edge router running BGP and my firewall (1.2.3.1/30 is the firewall's "outside" interface)
My DMZ is 1.2.3.64/26, with 1.2.3.91 being one IP inside that range - the firewaall has 1.2.3.126 on the layer 3 interface for the DMZ.
Routing table (again, somewhat obfuscated)
VIRTUAL ROUTER: default (id 1)
==========
destination nexthop metric flags age interface next-AS
0.0.0.0/0 1.2.3.2 10 A S ethernet1/2
10.0.243.0/24 10.100.100.250 10 A S ethernet1/1
10.0.244.0/24 10.100.100.250 10 A S ethernet1/1
10.0.250.8/29 0.0.0.0 10 A S tunnel.5
10.0.250.16/29 0.0.0.0 10 A S tunnel.4
10.0.250.24/29 0.0.0.0 10 A S tunnel.6
10.0.252.0/24 10.100.100.250 10 A S ethernet1/1
10.0.253.0/24 10.100.100.250 10 A S ethernet1/1
10.0.254.0/24 10.100.100.250 10 A S ethernet1/1
10.10.0.0/24 10.10.0.0 10 A S tunnel
10.10.1.0/24 0.0.0.0 10 A S tunnel.3
10.50.0.0/24 10.100.100.250 10 A S ethernet1/1
10.50.1.0/24 10.100.100.250 10 A S ethernet1/1
10.50.10.0/24 10.100.100.250 10 A S ethernet1/1
10.50.12.0/24 10.100.100.250 10 A S ethernet1/1
10.50.13.0/24 10.100.100.250 10 A S ethernet1/1
10.50.14.0/23 10.100.100.250 10 A S ethernet1/1
10.50.16.0/24 10.100.100.250 10 A S ethernet1/1
10.50.17.0/24 10.100.100.250 10 A S ethernet1/1
10.50.50.0/24 10.100.100.250 10 A S ethernet1/1
10.100.1.0/24 10.100.100.250 10 A S ethernet1/1
10.100.2.0/24 10.100.100.250 10 A S ethernet1/1
10.100.3.0/24 10.100.100.250 10 A S ethernet1/1
10.100.4.0/24 10.100.100.250 10 A S ethernet1/1
10.100.5.0/24 10.100.5.254 0 A C ethernet1/4
10.100.5.254/32 0.0.0.0 0 A H
10.100.100.248/30 10.100.100.249 0 A C ethernet1/1
10.100.100.249/32 0.0.0.0 0 A H
172.20.12.0/24 10.100.100.250 10 A S ethernet1/1
192.9.200.0/24 0.0.0.0 10 A S tunnel.3
1.2.3.0/30 1.2.3.1 0 A C ethernet1/2
1.2.3.1/32 0.0.0.0 0 A H
1,2,3.64/26 1.2.3.126 0 A C ethernet1/3
1.2.3.126/32 0.0.0.0 0 A H
total routes shown: 34
I'm not seeing any sessions in the session table at all with a continuous PING running from an outside address to the host in question, but I *do* see sessions if I run one to another host in the DMZ, so I'm pretty sure the routing is right.
- 5218 Views
- 18 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- XSOAR - GET-GPO DisplayName in Cortex XSOAR Discussions
- Global Protect for IPad auto-connect option partially works in General Topics
- Block privileged accounts from accessing the Internet in Next-Generation Firewall Discussions
- XDR - Unable to clear user's APPDATA in Cortex XDR Discussions
- Query for CVE-2024-3400 in Threat & Vulnerability Discussions



