- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
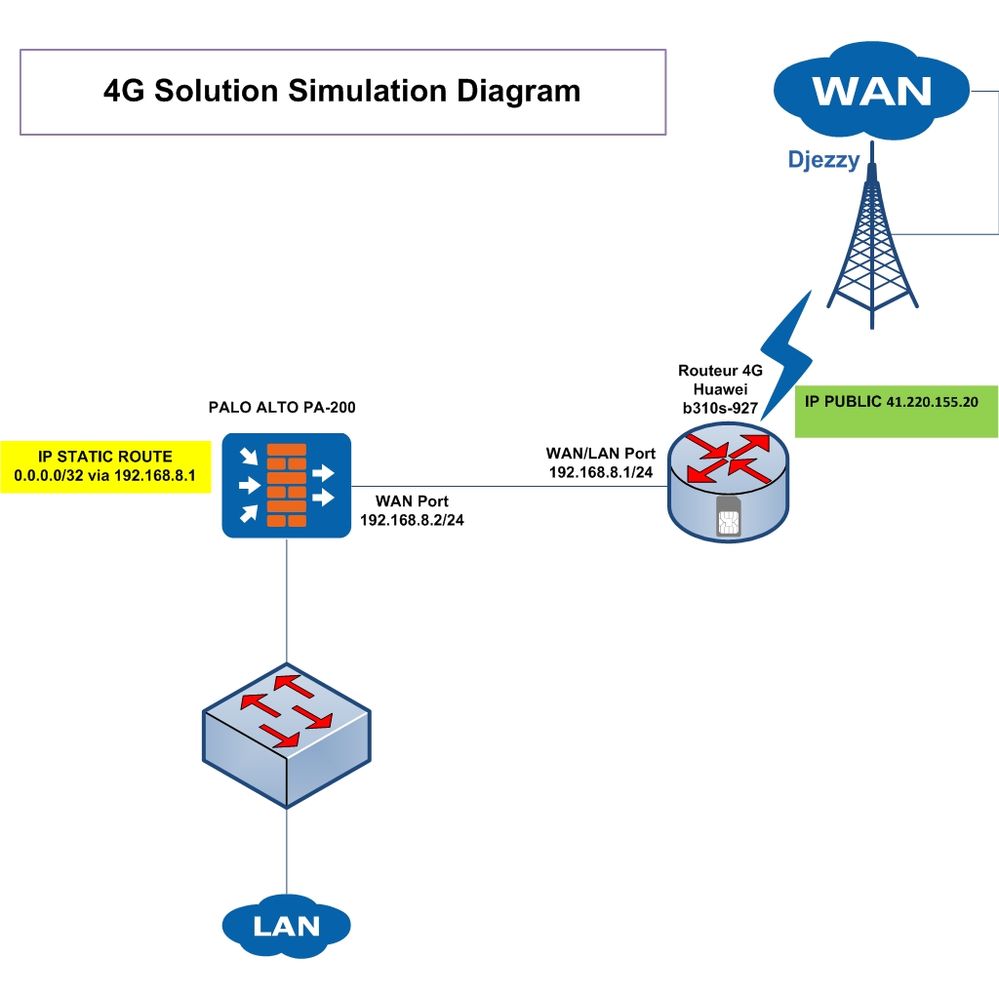
PA 200 Connected to 4G Router
- LIVEcommunity
- Discussions
- General Topics
- Re: PA 200 Connected to 4G Router
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
PA 200 Connected to 4G Router
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-15-2020 12:06 AM - edited 01-15-2020 12:09 AM
Hi Folks,
We currently have a primary direct internet from the ISP to the Palo Alto PA-200 configured with LSVPN .
As we plan to have a secondary Internet, we want to connect the Palo Alto PA-200 with 4G Router using LSVPN as well.
The problem is the public IP address is assigned to the 4G router and we'll connect it via LAN With PA-200 as the diagram illustrates below
How can Configure the PA-200 to implement the LSVPN as a client
Cordially
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-15-2020 07:13 AM
Hello,
Does the 4G router have the ability to just pass all traffic without performing any other tasks or to be a transparent device so the PAN could have the public IP? Meaning the PA-200 should be able to make the request to the core of the LSVPN and make the connection. Is this not working as designed?
Please advise,
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-15-2020 11:25 AM
Hi @Adam42
Why is it a problem if the public IP is on the 4G router? Btw. are you sure your 4G modem has a public IP? The way I used these modems so far, they always got a private IP ln the external interface and on provider side ther is carrier grade NAT for connections towards the internet.
Anyway, for GP LSVPN you don't need a public IP on your spoke firewall. Only the hub will need a public IP to receive the connections.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-15-2020 12:25 PM - edited 01-16-2020 12:04 AM
Hi @OtakarKlier
Which configuration should I do to make the router works transparent in order to carry the public IP address to the firewall? If I configure the DMZ IP on the router by assigning the IP address of the interface of the firewall PA200 will make it transparent?
Which configuration should I put on the firewall (spoke)
Thank you
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-16-2020 07:23 AM
Hello,
Back in the day when i was doing this, there was a setting in the 4g router that allowed it to be transparent and it would pass the public IP to the attached device/firewall. While I dont know what or if there is that in the device you are using, you might want to reach out to the vendor and check. However like @Remo pointed out. it might not be required.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-19-2020 12:54 AM
Hi @OtakarKlier
Thank you for your answer, Well i'm using Huawei AR160 series .
The Hub administrators are requesting the public ip and its Gatway but the 4G providers has just offered One Public IP /32 With NAT .
Thank you
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-04-2020 01:44 PM
Hi there,
You just need to NAT inbound ports from the 4G router to the Palo IP. Or simpler if you just set a DMZ host on the 4G router to send all traffic to the PA.
The ISP however will need to map a public address and inbound ports as the carriers usually only allocate you a private address. I've just bought a international SIM card that does this. They basically assign me a static public address their end, and it NATs through their cell provider VPN to the private IP on my router. I need to arrange with them what ports they pass inbound (which is good as it filters out port scans etc but bad as if I want to add a new service I have to ask them)
Ports for LSVPN are tcp/443 and udp/4501
That router then NAT's all inbound to the ip on the palo alto. The palo alto is configured with a private address but it doesnt matter as long as your public IP is used for LSVPN inbound.
If this is a remote office then you don't need any of the inbound NAT's setup as its a one way connection.
- 5065 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- SNMP (V3) not working on MGMT Interface in General Topics
- Allow traffic mikrotik site to site. in General Topics
- GlobalProtect disconnecting the RDP connection when trying to connect in General Topics
- XDR data lake and related questions in Cortex XDR Discussions
- Layer 3 Ethernet Interface vs Layer 3 VLAN interface in General Topics