- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
PA-500 isn't allowing some Google services (Play store, calendar sync, etc.)
- LIVEcommunity
- Discussions
- General Topics
- Re: PA-500 isn't allowing some Google services (Play store, calendar sync, etc.)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
PA-500 isn't allowing some Google services (Play store, calendar sync, etc.)
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-02-2015 02:05 PM
Pardon the noob query or lack of actual technical knowledge in our PA-500 but I've been asked by my supervisor to see what might be blocking some Google services/apps on our new PA-500. I've tried to monitor the IP address (my personal cell phone) and gain some insight via the monitor tab and the traffic and url filtering components of this monitor section and I can't come up with much. Has anyone battled this out there? It must be blocked at a pretty high level because everyone here in I.S. can't connect to these Google services and we're in a filter group that can get to almost anything.
Any ideas as to where to start? Please remember I'm not super fluent in the firewall but can certainly log-in and poke around if anyone has any ideas. Thanks a ton for any help. It is a bit of a big deal since we have a dozen Android tablets for our Home Care department and they need to be able to update apps, etc. As of now, everything seems to be blocked regarding the Play store, calendar and Gmail syncing. On a side note, ESPN alerts are not coming through as well which isn't cool, hehehee!! Thanks again --Kirk
- Labels:
-
Configuration
-
Troubleshooting
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-03-2015 02:26 AM
Welcome to the forums Kirk,
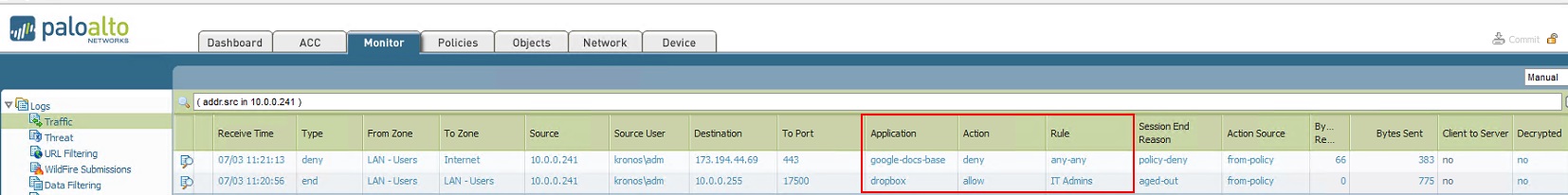
If you go to the Monitor -> Traffic and filter on your IP ( addr.src in x.x.x.x ) can you see the Google applications being blocked?
Example below shows how Google Docs is blocked and Dropbox is allowed and what rule causes that.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-03-2015 04:55 AM
If you cannot find your logs for sessions you know occurred, then go to your policy list and make sure you have logging turned on for the policies.
You are looking in the right place, your traffic and url filtering logs would be where this should show up.
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-03-2015 09:23 AM
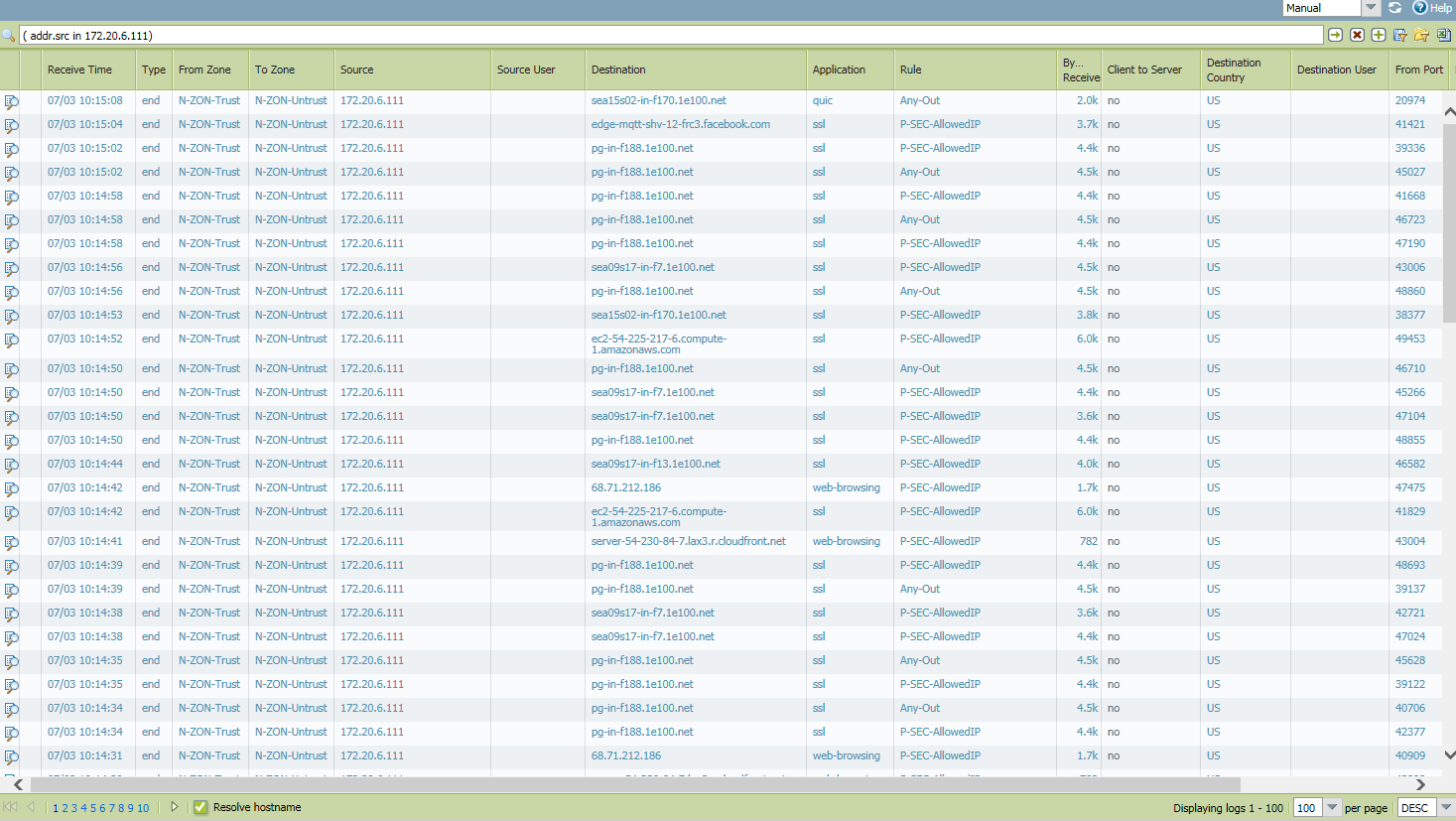
Thanks BLH! I don't actually see anything obvious like that. I've tried to safe-list some of the things I do see but they must not be Google's IPs/domains. This is what I see from my IP (cell phone) and I just don't see anything that is obvious to Google. Could it be blocked before it even gets to this point?
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-03-2015 09:27 AM
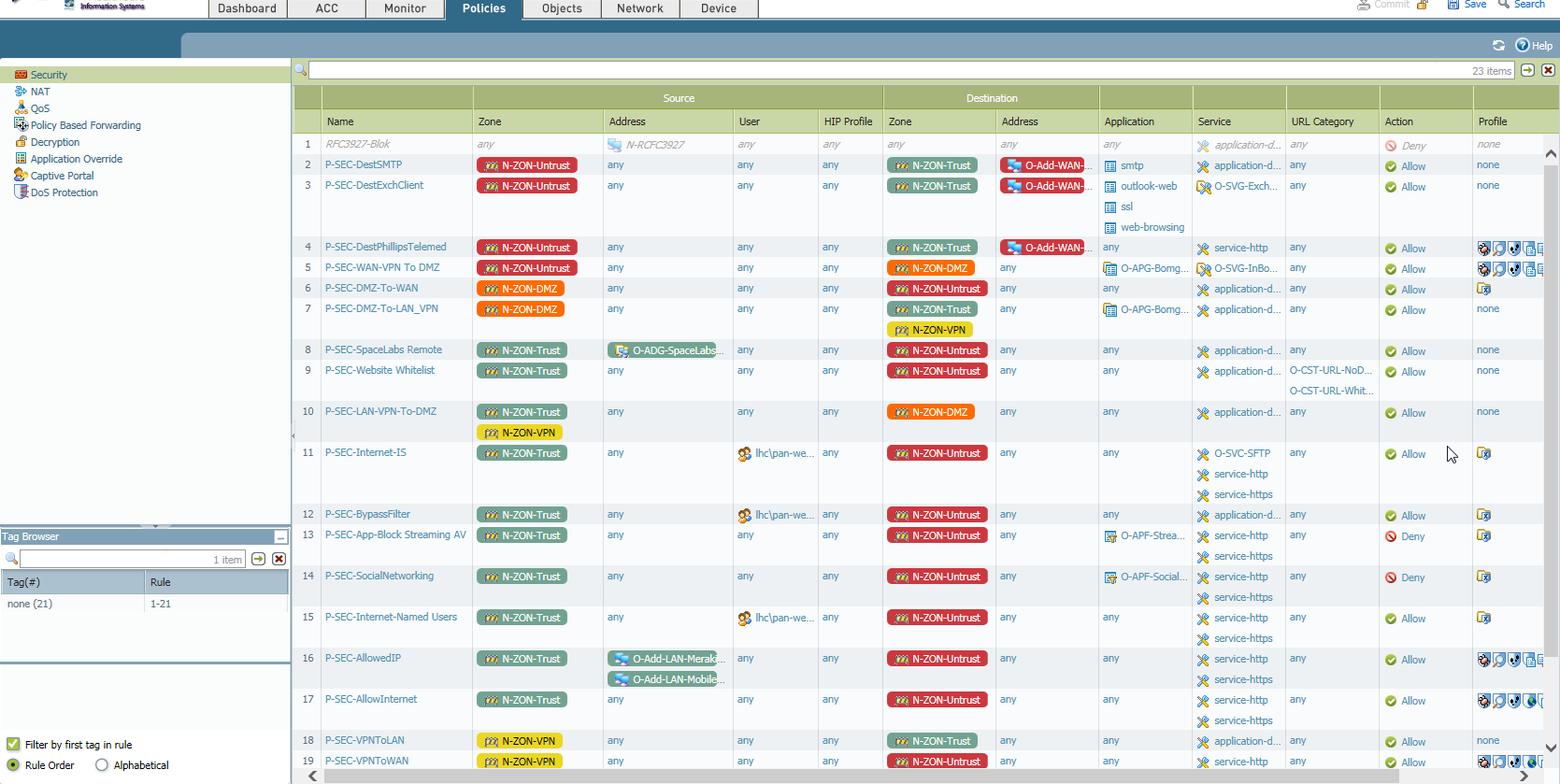
Steven, there looks to be about 23 policies in that section. How would I know what to turn on, if it isn't already? How would I know which one to even investigate? Sorry...again, my supervisor set this whole thing up. Thanks for the reply and help.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-03-2015 02:53 PM
Kirk,
In your screenshot of the traffic log, the traffic you did see is hitting two different security policies - "P-SEC-allowedIP" and "Any-Out". Those are being logged. To check whether or not logging is turned on for a particular security policy, click the name of it to open its settings. In the Actions tab, you will see two check boxes, Log at Session Start and Log at Session End. I would make sure that one of those boxes is checked for any other policies that may be affecting traffic from your phone. If you're not sure which one(s) that might be, check them all. Per the documentation for 7.0, Start should be checked and End is unchecked by default.
Once you're sure everything is being logged, you can filter for your phone's IP address again as the Source in the traffic log, and anything from your phone traversing the firewall to the internet should be shown. I would also do an OR and look for your phone's IP as the destination address as well, in case your requests are going out but the replies are not being allowed back in.
( addr.src in 172.20.6.111 ) OR (addr.dst in 172.20.6.111 )
Add the Action column to your traffic log view, too, and put it right next to Rule. That way you should be able to see what rules your tests are matching, and what the rule did with the traffic (allow, drop, reset, etc.) The Session End Reason field will also tell, e.g. policy-deny.
Keep in mind, too, that security rules are evaluated in order from top to bottom, the first match wins. It is possible a rule higher in the list is taking precedence and blocking your traffic, despite your very permissive IS dept rule applied to that group.
If you really need to dig in, there's always packet capture.
Finally - don't forget to back up your current configuration before you start changing things, and don't forget to do a Commit to make changes take effect before testing.
Dan
- 5298 Views
- 5 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Enterprise email had not been allowed to access Strata Cloud manager pro link and common services in Strata Cloud Manager
- PANOS URL filtering 11.0.4 in Next-Generation Firewall Discussions
- Allow only global protect from trust to untrust. in General Topics
- How to check not detected open or allowed ports in service rule policy in Next-Generation Firewall Discussions
- error: azure marketplace vm-series do not bootstrap in VM-Series in the Public Cloud



