- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
PA to ASA Proxy-ID Mismatch
- LIVEcommunity
- Discussions
- General Topics
- Re: PA to ASA Proxy-ID Mismatch
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-30-2018 07:07 AM - edited 03-30-2018 10:15 AM
Hi all,
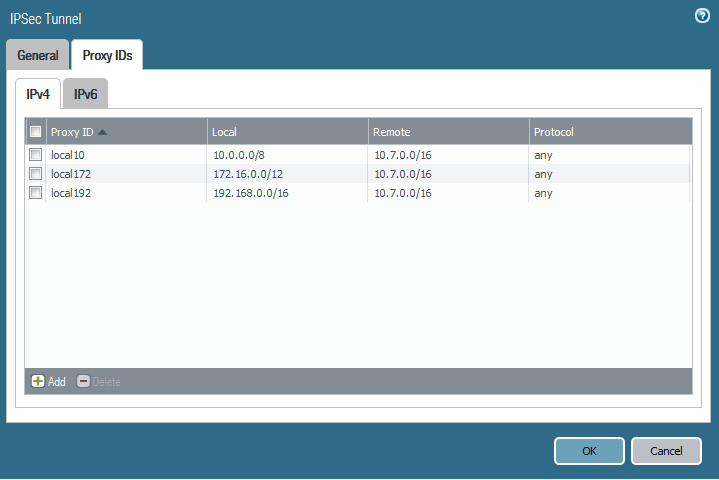
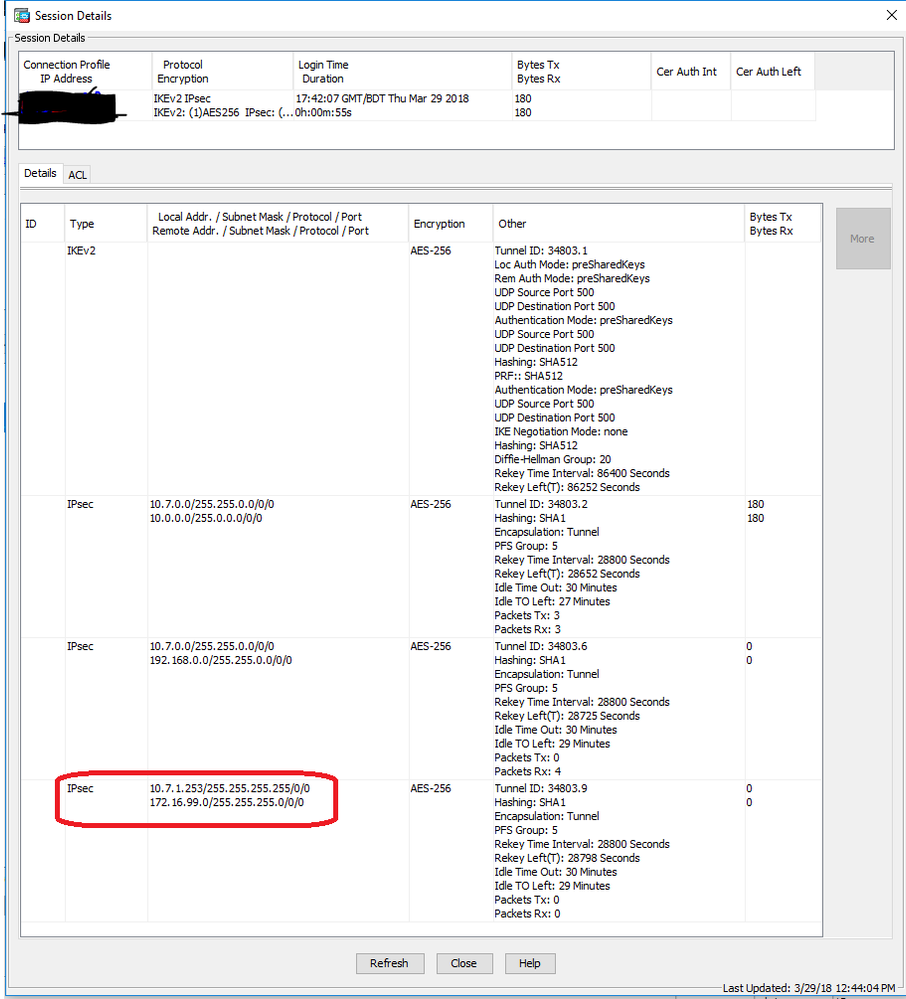
We have a standard IPSec tunnel one of our smaller sites with a strange issue related to the Proxy-IDs defined on the PA side of the tunnel. Our ASA side (10.7.0.0/16) is set to inherit all policy settings from the PA side, and our PA defines the "policies" with the Proxy-ID. Normal behavior with a policy based firewall (ASA) and a route based firewall (PA).
The issue is that while two of the networks defined on the PA side Proxy IDs are match the tunnel details on the ASA, the third network does not. Traffic from the 10.0.0.0/8 and 192.168.0.0/16 supernets is allowed over the tunnel without issue; however, the 172.16.0.0/12 supernet shows up on the ASA's as a smaller, but valid, subnet within the 172.16.0.0/12 supernet and only to one specific host. This is preventing anything in our 172 networks from accessing the site due to a mismatch in the negotiated session.
A quick note. Our PA is using SW version 7.1.10. In this version, we have seen some "ghosting" where some changes are not properly removed from the config file; as in objects still existing after removal, routes existing after removal, etc, so this may be related. We are upgrading this OS during our next maintenance window to 7.1.16.
Screenshots are below. I have also used proxy-ID local 0.0.0.0/0 but the results remain unchanged.
Thank you!
- Edit: a word
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-30-2018 10:12 AM - edited 03-30-2018 10:13 AM
Probably the only solution for you is upgrading to something higher than 7.1.10. The issue you are facing is fixed in 7.1.11.
PAN-77127 Fixed an issue where the firewall reduced the range of local and remote
IKEv2 traffic selectors in a way that disrupted traffic in a VPN tunnel
that a Cisco Adaptive Security Appliance (ASA) initiated.
So upgradin to 7.1.16 is a good idea, that will solve the issue.
Another workaround would be changing the tunnel to IKEv1.
(Ok, there is a very little chance that you have found another problem, but I am pretty sure that your issue is fixed after the upgrade becaue I had exactly the same issue a while ago)
Regards,
Remo
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-30-2018 10:12 AM - edited 03-30-2018 10:13 AM
Probably the only solution for you is upgrading to something higher than 7.1.10. The issue you are facing is fixed in 7.1.11.
PAN-77127 Fixed an issue where the firewall reduced the range of local and remote
IKEv2 traffic selectors in a way that disrupted traffic in a VPN tunnel
that a Cisco Adaptive Security Appliance (ASA) initiated.
So upgradin to 7.1.16 is a good idea, that will solve the issue.
Another workaround would be changing the tunnel to IKEv1.
(Ok, there is a very little chance that you have found another problem, but I am pretty sure that your issue is fixed after the upgrade becaue I had exactly the same issue a while ago)
Regards,
Remo
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-30-2018 10:16 AM
Thanks for the insight Remo. I'll monitor this and update the post once we have upgraded.
Cheers!
-josh
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-24-2018 09:22 AM
Hi Remo,
After updating our firewall cluster to 7.1.16, the issue with ProxyID mismatch has been resolved. Thanks for the help!
-josh
- 1 accepted solution
- 5204 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Failed to extract file panup-all-antivirus-4788-5306.tgz with sha256 in General Topics
- Managed Logcollector in Panorama Discussions
- Running 11.1.2 in production in Next-Generation Firewall Discussions
- Decryption: Client and decrypt profile version mismatch in Next-Generation Firewall Discussions
- HA pair not synchronizing in Next-Generation Firewall Discussions