- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Palo Alto Forward Proxy?
- LIVEcommunity
- Discussions
- General Topics
- Re: Palo Alto Forward Proxy?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Palo Alto Forward Proxy?
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-19-2017 12:28 PM
We presently leverage a fwd-proxy solution that a selection of hosts (2000-3000) on various networks pass through in order for us to funnel them to a few IP's and enforce a more STRICT URL policy at the perimeter. The hosts are managed through GPO.
My question is will PAN or has PAN developed the capability to take the role of a fwd-proxy server that hosts can be pointed too so Internet connections are funnled to a specific interface or similar like this type of scenario?
Thank you
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-19-2017 02:28 PM
Hello @Gun-Slinger,
I think it would help the community out if you explain exactly what your current proxy is doing, just logging, captive portal, ssl decrypt etc. With the PAN you can funnel all of your traffic out one interface, or more in case of failover for upstream issues. The more detail you provide (obiously redact any info that can used against you) the more we can help out.
Cheers!
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-19-2017 03:10 PM - edited 10-19-2017 03:11 PM
Do you mean that your devices are behind proxy server?
In this case your proxy server should add X-Forwarded-For for Palo to identify UserID and apply Security Policies and profiles based on user/group.
Palo itself is not proxy. It does not cache or do url rewrites.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-20-2017 12:20 PM
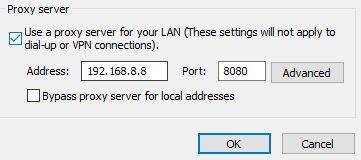
To clarify, we use a fwd-proxy environment that hosts through GPO are pointed too (See example from IE):
This proxy strictly just completes a fwd-proxy on 2000-3000 hosts on subnets across the institution. No other services are performed on this proxy.
The 2 proxy servers are 192.168.8.8 and 192.168.9.9 for this example. Our Pan URL filtering is at the perimeter and these 2000-3000 hosts require a more strict URL filtering profile then the other traffic in the istitution. In order to do this without adding every host to the policy with this URL filtering profile, we point through GPO (see above) to the 2 proxy servers that then proxy the connections behind 192.168.8.8 or 9.9.
From there our policy on the perimeter is built to apply the more restrictive URL filtering policy to these 2 IP's 192.168.8.8 and 9.9 which in turn is applied to those 2000-3000 hosts.
The question is if this proxy function can be obsorbed into the PAN? Where we could point through GPO the hosts to an interface on the PAN and from there it is treated like a proxy but a point we could apply specific URL filtering profiles too.
Thank you for any guidance.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-20-2017 12:38 PM
Hello,
Ah the old URL filtering and who gets the more strickt one. So with reference to the GPO and pointing to a proxy, that piece would be removed. Then you would have security policies on the PAN for the different levels of URL filtering. My personal favorite way is to use AD groups. For this you would have to setup the user-id feature set, either agentless or with the agents or both. https://www.paloaltonetworks.com/documentation/80/pan-os/pan-os/user-id This way we can just add and remove users without having to touch the firewall. Another methow could be source subnets or zones.
i.e. you have a URL filtering policy 'More Strict URL' and assign a AD group to it. That way no matter which machine or where the user is located, they are always in the More Strict URL filtering group.
Here is the link to the general guide for PANOS8
https://www.paloaltonetworks.com/documentation/80/pan-os/pan-os/url-filtering
I hope this makes sense. Please feel free to ask additional questions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-20-2017 12:52 PM
The firewall does not perform web-proxy services
a different approach however could be to leverage User-ID and create policy based on group membership or on the fact a user has been/has not been identified
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-20-2017 01:16 PM
Thanks @OtakarKlier and @reaper for the feedback. I had forgotten until it got mentioned, but originally I went the user-id route as these machines use a resource account across all of them which made it very easy. This worked well until a desktop admin logged in to the machine to work on an issue and it would override the machine allowing the machine to now bypoass the more restrictive URL filtering process. The option was looked at to ignore these admins but the list was very long and used in other User-id rules. This is why we had to go the proxy route.
- 5908 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- web file blocking in Next-Generation Firewall Discussions
- Request Advice – BGP Failover Route-Based IPsec VPN With WatchGuard (WG) in Next-Generation Firewall Discussions
- Issue with IOS 26 and SMTP in Next-Generation Firewall Discussions
- Newsletter: Cloud Delivered Security Services, Oct-2025 in Advanced Threat Prevention Discussions
- LGTV and Netflix bugs out when going through Palo Alto in General Topics