- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Palo Alto Stopped taking New Policy Traffic.
- LIVEcommunity
- Discussions
- General Topics
- Re: Palo Alto Stopped taking New Policy Traffic.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Palo Alto Stopped taking New Policy Traffic.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-27-2021 12:35 AM
We recently upgraded the Palo Alto version to 9.1.7 on our physical hardware 3200 series. After 02 days we notice that before upgrade all policy rules and NAT works fine. However, The NAT and policy which we created after the upgrade not working. Not traffic or hit shows in monitoring.
We rebooted the PA once still is not fixed. Is it a bug in the current version.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-27-2021 01:40 AM
Hi @AmardeepSuri ,
There's not a lot of info in your post to help you on your way.
Is traffic reaching your firewall correctly ? Is it dropped before actually getting logged (check drop counters) ?
I'm not aware of a bug describing your issue.
While PAN-OS 9.1.7 seems fine, know that 9.1.8 is the recommended release at the time of this writing.
Cheers,
-Kiwi.
Cheers,
Kiwi
Please help out other users and “Accept as Solution” if a post helps solve your problem !
Read more about how and why to accept solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-27-2021 01:55 AM
Hi, Thanks,
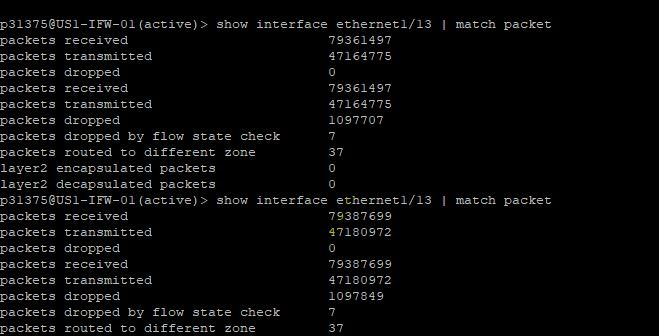
Yes, I observed packet drop increasing frequently.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-27-2021 02:51 AM
Hi @AmardeepSuri ,
Please make sure that the traffic you're investigating is actually reaching your firewall correctly (on the correct interface, etc...). You can confirm this with packet captures (https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClTJCA0).
Once you've confirmed that, create a packet filter based on the traffic you're investigating and check the global counter for specific drop counters. If there are any then it's likely they'll give you an indication of why it's being dropped.
Check out the following KB on how to check for global counters. There's even a use-case example that shows you how to check the drop counters specifically:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000CloNCAS
Cheers !
-Kiwi.
Cheers,
Kiwi
Please help out other users and “Accept as Solution” if a post helps solve your problem !
Read more about how and why to accept solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-27-2021 04:14 AM
Thanks!,
I tried packet capture earlier also using all 4 capturing options (drop, receive, transmit, and firewall ). and I enabled pre-match also. But that only showing me drop packet with only mac information no matching IP defined in filters.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-27-2021 04:37 AM
packets dropped on the interface may not reach the dataplane (where packetcaptures are performed)
disabling pre-parse will effectively cancel out filters as packets are captured before they are parsed (to filter). The drop packets you are seeing may be the mac frames you see in drop stage, are they 'normal' (no malformation?)
you may be distracted from your original issue:
since NAT does not appear to work, did you make sure the new NAT rules are in the proper order for them to match? rules are evaluated top to bottom with the first positive match being used. this could mean rules further down the rulebase are not hit as a preceding rule is too generic and you will need to reorder your rules
you can check if your rules exist on the dataplane by using the following command:
show running nat-rules
then see if the new rules exist or not
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-27-2021 10:29 AM
Thanks, Reaper.
As you suggested the checked the newly created NAT rule. However, I found that in the NAT rules list.
The command you shared not worked. But I tried with <show running nat-rule-ippool rule "Bi-Nat Rule 12-1">
Also, I would like to update not only the newly created NAT is not working. even an existing policy that allowing traffic from a specific source also not working when we added a new source in that.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-27-2021 12:41 PM - edited 05-27-2021 12:41 PM
In some cases saving a snapshot of the config, a fast factory default reset and again loading the config resolves such issues. If your firewall i in HA this is a thing that the TAC does many times
Before that check for commit errors:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000PMb2CAG
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-27-2021 07:40 PM
Tired the <commit force> still the problem is same.
- 4889 Views
- 9 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Security Policy with Destination Criteria in Strata Cloud Manager
- Not able to log XFF (Actual Client IP) in PaloAlto Logs even when we enable XFF and URL filtering profile in Palo's in Next-Generation Firewall Discussions
- Issue with allowing AnyDesk on a no-internet policy in Next-Generation Firewall Discussions
- Newsletter: Cloud Delivered Security Services, Oct-2025 in Advanced Threat Prevention Discussions
- ION Security Stack in Advanced SD-WAN for NGFW Discussions