- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Questions on Palo Alto safe practices
- LIVEcommunity
- Discussions
- General Topics
- Re: Questions on Palo Alto safe practices
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-24-2012 09:02 AM
Hi i have a few outstanding questions on Palo Alto devices. We just migrated from Juniper to PA line. So these might sound silly for people who already are on PA line.
- Do we have any primary and back up images on PA firewall . Just like in JUNOS if one image is corrupt it tries to load from the back up image file.
- How many rollbacks does the PA device support by default ? Can we actually delete some of them if we don't wish to have them on the device?
- How do we load factory default configuration on the device ? What does the factory default config contain ? Does it have some templates?
- What are the safe practices in operating a device ? Powering off and on PA firewall do we have some CLI commands ? I think we have a restart option in WEB GUI . But wanted to know about halting and forceful power off.
- How do we clean up the database once it is full ? Can we delete the logs like system logs and all?
- Flow diagram keeps changing in all of the modules (eg NAT ) . If you can throw some light on that , it would be helpful.
- Can we apply import policies for route redistribution? The reason why i ask this is i did not find any import for RIP , OSPF except for BGP.
- When we are configuring DNAT, what should we match on the destination IP address ( the pre NAT IP ) and i check mark on translated packet and give my post nat ip ? But i could not implement that on my device for some reason. Same goes with Static NAT
- When doing lab on Route redistribution , i matched on my default route and tried to redistribute that in OSPF but for some reason everything was visible except my default route which i exported in OSPF.
Hoping to get answers for these .. Thanks a lot guys !!
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-24-2012 01:16 PM
Hi Srikanth,
For Palo alto firewall, you can always re-install a software image. This can be achieved by going to Device > Software > and clicking the
As far as the partitions are concerned on the device, there are 2 partitions, running and revertible. Revertible would be the last version of OS installed on to the device.
>debug swm status
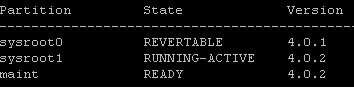
The revertible version is available if fallback is needed . With the next PAN-OS upgrade the revertible version will be replaced with the current running-active version. You will then be able to delete 4.0.1.
To boot from the partition in use prior to the upgrade, issue the command ,
>debug swm revert
Factory default configurations will have only management ip-addresses set to 192.168.1.1 and the default admin password.
For sample configurations please have a look at the following links to see if it useful to you,
https://live.paloaltonetworks.com/docs/DOC-2561
https://live.paloaltonetworks.com/docs/DOC-2560
At this time we don not have a CLI command to power off the device but we can restart the system
>request restart system
Force ful power off will be removing the power cable from the device.
You can delete the system traffic threat logs using the following commnads:-
To remove these logs, use the following CLI command:
clear log <log name>
where log name is:
acc
config
system
threat
traffic
Let me know if this is helpful.
Regards
Parth
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-24-2012 01:16 PM
Hi Srikanth,
For Palo alto firewall, you can always re-install a software image. This can be achieved by going to Device > Software > and clicking the
As far as the partitions are concerned on the device, there are 2 partitions, running and revertible. Revertible would be the last version of OS installed on to the device.
>debug swm status

The revertible version is available if fallback is needed . With the next PAN-OS upgrade the revertible version will be replaced with the current running-active version. You will then be able to delete 4.0.1.
To boot from the partition in use prior to the upgrade, issue the command ,
>debug swm revert
Factory default configurations will have only management ip-addresses set to 192.168.1.1 and the default admin password.
For sample configurations please have a look at the following links to see if it useful to you,
https://live.paloaltonetworks.com/docs/DOC-2561
https://live.paloaltonetworks.com/docs/DOC-2560
At this time we don not have a CLI command to power off the device but we can restart the system
>request restart system
Force ful power off will be removing the power cable from the device.
You can delete the system traffic threat logs using the following commnads:-
To remove these logs, use the following CLI command:
clear log <log name>
where log name is:
acc
config
system
threat
traffic
Let me know if this is helpful.
Regards
Parth
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-24-2012 01:34 PM
Srikanth,
Flow diagram for a packet when it ingress the firewall is explained beautifully in this document:-
https://live.paloaltonetworks.com/docs/DOC-1628
Also here is the link to the redistribution of routes from one area to the other using the firewall.
https://live.paloaltonetworks.com/docs/DOC-3377
https://live.paloaltonetworks.com/docs/DOC-1113
Document is also attached to the thread.
Here is the sample config snapshot of the DNAT rule
Make sure you also have a security rule to allow traffic from untrust to trust zone.
Link to NAT document :
https://live.paloaltonetworks.com/docs/DOC-1517
Advertising a default route via OSPF. Is this what you were looking for?
https://live.paloaltonetworks.com/docs/DOC-3700
Let me know of it is helpful.
Regards
Parth
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-24-2012 09:30 PM
1. See ppatel answer. You have a revertable image and you can also load other images aswell (the later will take a few minutes to complete since it will re-install the image you like).
2. I think that depends on the model and how large the drives are. I prefer to delete stuff I no longer have use for and keep only the previous (and perhaps the version before that) still on the box. You can always download the images again if needed (keeping the old images is just to not to have to wait for the download to complete in case one need to rollback).
3. You can use the maint-mode to reset the device into factory settings (the current image will be used but all settings and logs will be wiped).
4. I think its safe to use a PA box just like any other networkconnected device. The main difference (depending on which models of Juniper you used previously) is that the PA have a dedicated mgmtplane running linux. So if you just unplug the powercoard it might take a few more seconds to boot up next time due to harddrive checks. Compared to Juniper the PA main configuration method is to use the WEB rather than CLI as GUI.
5. The logs are like a cyclic buffer so oldest entries will be overwritten by default. If you need to store the logs for a longer time of period you can get a Panorama log-only installation which your PA devices will push their logs to. You can also use plain syslog to archive the logs. Also CEF is supported in case you run Arcsight.
6. Except for what ppatel already said the guideline when setting up security policies in a PA for NAT-use is:
srczone: <prenat srczone>
dstzone: <postnat dstzone>
dstip: <prenat dstip>
7. Sorry I havent done dynamic routing with PA so I dont know.
8. See 6 above.
9. See 7 above.
Bonus: If you havent seen these docs before these 2-3 docs are great in order to better learn how a PA can be used:
Designing Networks with Palo Alto Networks Firewalls
https://live.paloaltonetworks.com/docs/DOC-2561
Diagrams and Tested Configurations
https://live.paloaltonetworks.com/docs/DOC-2560
Threat Prevention Deployment Tech Note
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-24-2012 10:19 PM
Hi Parth thanks for the useful info
I am using 6 PA 500 devices and 1 PA 2020 device . I assume that this has a storage capacity of 120 gb . But it shows 5.96 gb free and rest is occupied and i am pretty sure that i did not create any logs. How can i free this storage space and make use of the rest of 115 gb on my PA firewalls
Thanks in advance..
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-24-2012 10:33 PM
Hi Srikanth,
Where do you see these ? Is it under Device > Setup > management ?
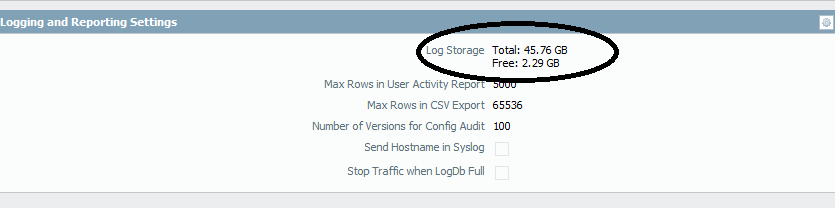
Once you click edit under these settings, you will see the following:-
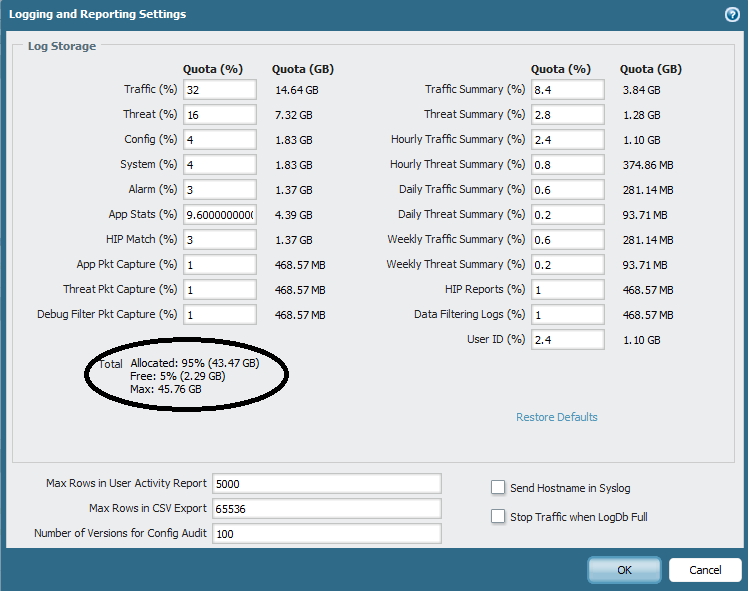
This means that 45.76 GB of your total space is allocated to logging and reporting and the rest of it is free.
If you add up the% quotas, it will be 95%. (As an example to the above screenshot)
Please let me know if it is helpful.
Regards
Parth
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-24-2012 10:41 PM
Hi Parth,
I could see this under Device > Setup > Management tab the space reserved as 95 percent
But i could not see the other one precisely how much memory is occupied on my firewall currently .
Could you help ?
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-24-2012 10:46 PM
Hi Mikand thanks for the prompt reply
3. You can use the maint-mode to reset the device into factory settings (the current image will be used but all settings and logs will be wiped).
Except for this one i think i have a clarity on rest of the things.
How do i load the maint mode on PA both from CLI and Web GUI?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-24-2012 10:55 PM
Srikanth,
The following command will help you to see the disk space on the device.
admin@Lab-59-PA-500> show system disk-space [example output]
Filesystem Size Used Avail Use% Mounted on
/dev/sda2 3.8G 1.2G 2.5G 31% /
/dev/sda5 7.6G 3.3G 3.9G 47% /opt/pancfg
/dev/sda6 3.8G 2.5G 1.2G 69% /opt/panrepo
tmpfs 487M 37M 451M 8% /dev/shm
/dev/sda8 51G 1.9G 47G 4% /opt/panlogs
Log-Quota:-
admin@Lab-59-PA-500> show system logdb-quota
Quotas:
traffic: 32.00%, 14.643 GB
threat: 16.00%, 7.322 GB
system: 4.00%, 1.830 GB
config: 4.00%, 1.830 GB
alarm: 3.00%, 1.373 GB
trsum: 8.40%, 3.844 GB
hourlytrsum: 2.40%, 1.098 GB
dailytrsum: 0.60%, 0.275 GB
weeklytrsum: 0.60%, 0.275 GB
thsum: 2.80%, 1.281 GB
hourlythsum: 0.80%, 0.366 GB
dailythsum: 0.20%, 0.092 GB
weeklythsum: 0.20%, 0.092 GB
appstat: 9.60%, 4.393 GB
userid: 2.40%, 1.098 GB
hipmatch: 3.00%, 1.373 GB
application-pcaps: 1.00%, 0.458 GB
threat-pcaps: 1.00%, 0.458 GB
debug-filter-pcaps: 1.00%, 0.458 GB
hip-reports: 1.00%, 0.458 GB
dlp-logs: 1.00%, 0.458 GB
Disk usage:
traffic: Logs: 211M, Index: 54M
threat: Logs: 53M, Index: 2.8M
system: Logs: 954M, Index: 149M
config: Logs: 97M, Index: 1.4M
alarm: Logs: 16K, Index: 16K
trsum: Logs: 138M, Index: 5.7M
hourlytrsum: Logs: 2.4M, Index: 2.4M
dailytrsum: Logs: 1.4M, Index: 2.2M
weeklytrsum: Logs: 728K, Index: 468K
thsum: Logs: 612K, Index: 772K
hourlythsum: Logs: 600K, Index: 600K
dailythsum: Logs: 560K, Index: 560K
weeklythsum: Logs: 88K, Index: 88K
appstatdb: Logs: 6.2M, Index: 5.7M
userid: Logs: 12K, Index: 12K
hipmatch: Logs: 16K, Index: 16K
application-pcaps: 32M
threat-pcaps: 60K
debug-filter-pcaps: 26M
dlp-logs: 4.0K
hip-reports: 1.1M
wildfire: 4.0K
Let me know if this helps.
Regards
Parth
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-24-2012 10:59 PM
Hi Srikanth,
Reboot device, monitor the boot sequence for the following message: Autboot to default partition in 3 seconds.
- Select m to boot to maintenance partition. OR type "maint" to enter into maintenance mode.
Once you execute that, you will be in maint mode .
Additionally to factory default the device,
- From the maint partition select factory reset.
- At the password prompt, enter MA1NT.
- Allow the device to complete the boot sequence.
- After booting is completed, login using the default username password.
Is this helpful
Regards
Parth
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-24-2012 11:09 PM
HI Srikanth,
I forgot to add that there is NO WAY to enter into maintenance mode through the GUI.
It is only possible through the CLI with a console access since we have to monitor the boot up sequence.
Regards
Parth
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-24-2012 11:49 PM
Thanks Parth for patiently answering all my queries .
May be once i start working i get even more queries ! But thanks this has solved lot of my questions !!
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-25-2012 02:40 AM
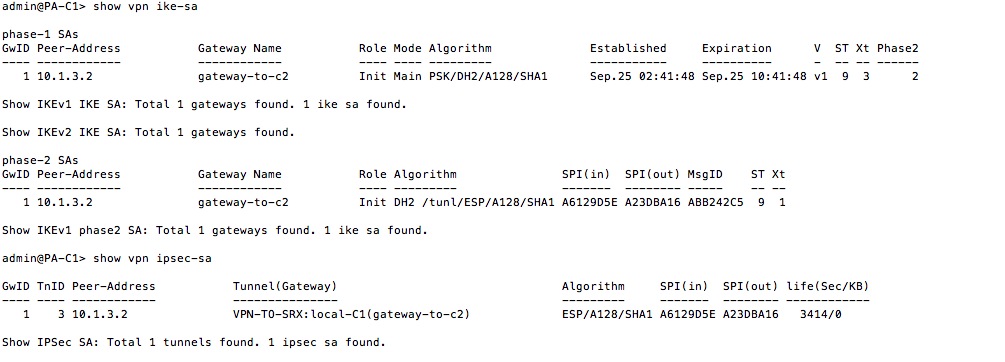
Hi this is one the sample output that i captured when i established a VPN tunnel between 2 PA firewalls.
As far as my knowledge goes Ike SA's are bi directional and IPSEC SA's are uni directional correct me if i am wrong.
But here i see 2 SA's in Phase 1 , but all i establised was only 1 VPN tunnel .
Can some throw some light on this please . Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-25-2012 03:00 AM
Hi Srikanth,
Since this is a different topic related to IPSEC lets go ahead and create a new discussion thread and so the techs can provide their inputs. The show commands actually shows you one negotiation for phase 1 and other for phase 2. I can explain in detail if you can create a new discussion thread.
Does that work for you?
Regards
Parth
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-25-2012 11:03 PM
Hi we normally use an external remote power management to turn on and off the devices.
This is like a forceful power off and am i afraid in the long run this might affect my devices. So is there any way that i can gracefully halt all the processes and then power off them remotely ?
I suddenly see msg after logging in system is intialising please wait or press ctrl + c to abort .
Is this something to worry about ?
Also wanted to know what is the netflow profile in the interfaces configuration tab.
What precise advantages we see when deploying interfaces on a tap mode and vwire mode.
Can we actually replicate the real time traffic on my firewall before i deploy by using tap mode?
- 1 accepted solution
- 10757 Views
- 20 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- web file blocking in Next-Generation Firewall Discussions
- Cortex XDR triggers Code 10 on USB Audio despite exception - Vendor not selectable, need per-device allow without vendor or something in Cortex XDR Discussions
- Struggling to Unset Virtual Router from Interface via API – Manual Works, API Always Fails in General Topics
- Slow get_alerts API response / Validity check in Cortex XDR Discussions
- How to Block Mobile Phones (iPhone/Android) via USB Using Device Control in Cortex XDR Discussions



