- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
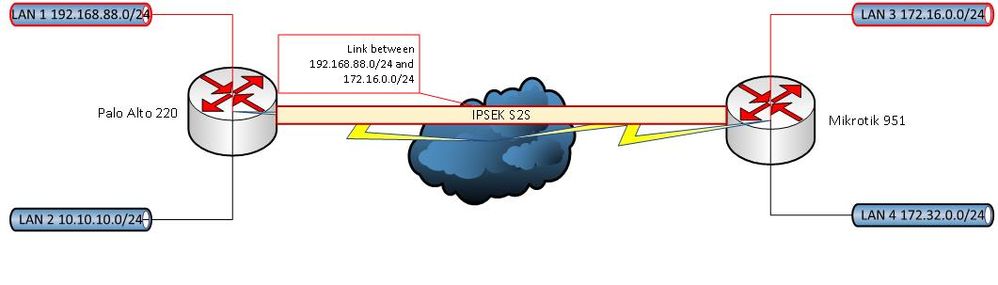
Several subnetworks through the tunnel between Palo Alto and Mikrotik
- LIVEcommunity
- Discussions
- General Topics
- Re: Several subnetworks through the tunnel between Palo Alto and Mikrotik
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Several subnetworks through the tunnel between Palo Alto and Mikrotik
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-22-2020 01:03 AM
Site 2 site allows only two networks to be pulled inside the tunnel (one of them behind the mikrotik and the other one behind the palo alto).I’ve tried different settings and it doesn't help.
Has anyone had experience building a tunnel between them based on GRE tunnel over IPsec?
Several subnetworks need to be passed through the tunnel.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-22-2020 02:17 AM
is GRE a requirement?
a regular IPSec tunnel will allow as many subnets as you need, adding GRE will create some limitations because of GRE
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-22-2020 03:12 AM
I have configured s2s between mikrotik and palo alto.
Local networks go between them. I need to add other networks through this tunnel.
On the Palo Alto, I added another network on the tunnel to the proxy id.
In mikrotik, the accept rule from the LAN(Firewall - NAT) to the network behind the tunnel.
But there is no ping.
Only two networks can be specified in the IPSEC settings.
It does not work to create another policy, as the keys begin to break.
Also, there is no separate interface on Mikrotik (like with GRE).
When adding routes, I indicate the local interface.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-22-2020 03:07 PM
Hello,
Do either of the firewall logs show where the pings are failing? It could be a policy rule that is preventing the traffic?
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-23-2020 02:13 AM
In monitoring (traffic) PA there are no records from the network 10.10.10.0/24 (from source and dest)
ssh PA utility: ping source 10.10.10.1 host 172.16.0.254 (no response)
Mikrotik terminal: ping source 172.16.0.254 10.10.10.1 (no response)
ip - firewall -connection (no response)
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-23-2020 08:15 AM
Hello,
Make sure the policies on the PAN are set to log at session end. On the PAN, are the routes to the 172 networksi n the virtual router and pointed at the Tunnel? Also in order for the PAN interface to respond to pings, it must have a management profile attached to it that allows PING.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-26-2020 06:41 AM
Hello/
In the rules, there is a permissive rule from this zone to the lan zone. Then, as a test, I added it to the LAN (LOCAL) zone where all traffic is allowed inside.
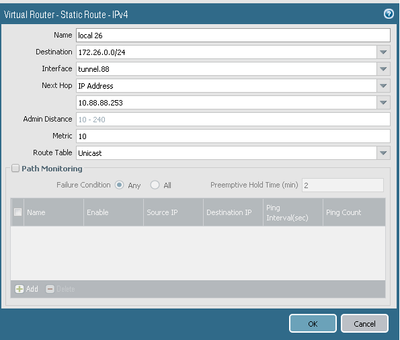
Yes, there is a route to the network through the tunnel.
Added MNG profile trust (ping allow) on the tunnel.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-09-2020 06:47 AM
Previously, I set up a tunnel between a cisco router and a PA.
IPsec Site-to-Site VPN Palo Alto <-> Cisco Router w / VTI cc
They used a virtual tunnel interface (VTI) in a cisco router.
Drawing an analogy, I tried to collect between PAlo alto and Mikrotik.
As you know, on microtik you need to separately create a GRE interface, and then apply IPSEC.
I tried creating a loopback on it to hang the address on it.
Then I made the settings for IPSEC, and added a route.
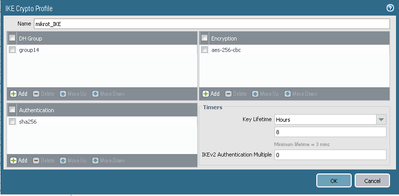
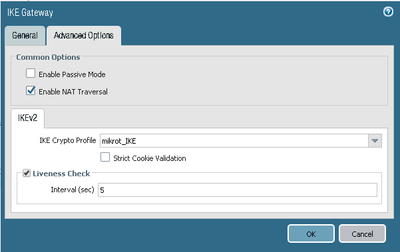
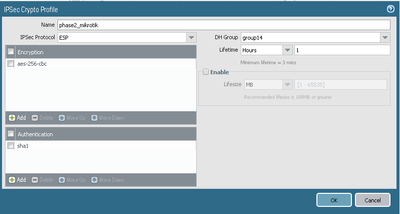
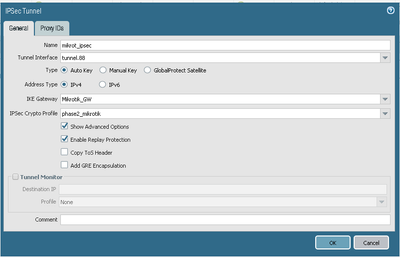
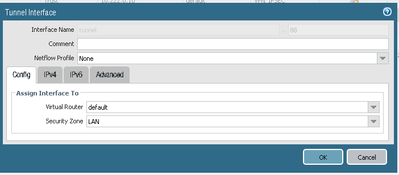
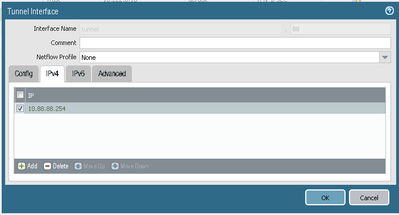
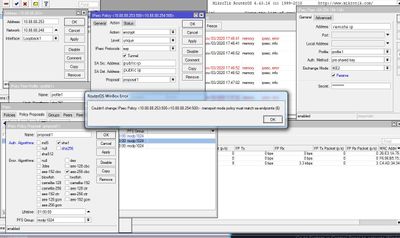
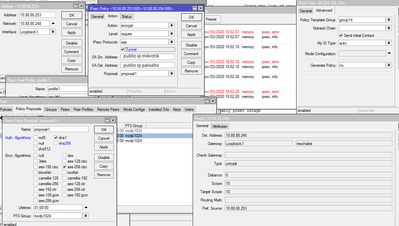
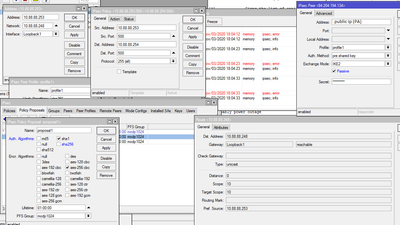
Below I am attaching screenshots of both of the devices with settings.
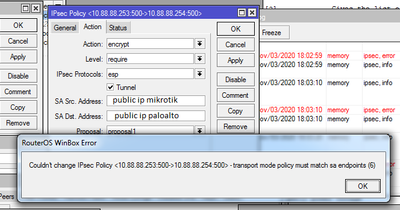
I encountered an error in the IPSEC settings, it does not allow unchecking the Tunnel checkbox.
Instead, it issues an error message "Couldn't change IPSEC Policy - transport mode policy must match sa endpoints".
If you enter the IPSec settings:
Peer Address - 0.0.0.0/0
IPSec Policy- SA Dst. Address 0.0.0.0/0
It does not help.
In 'IPSec/Peer' set only remote peer, not local.
https://wiki.mikrotik.com/wiki/Manual:IP/IPsec
Tried changing policy settings - action , level, protocols. It does not help too.
Anybody have idea?
- 4540 Views
- 7 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Allow traffic mikrotik site to site. in General Topics
- Unsupported protocol "IPv6 Control Protocol Error" in General Topics
- DNS routing issue - OpenVPN inside GlobalProtect VPN in Next-Generation Firewall Discussions
- PA-VM testing / homelab in General Topics
- Include or Exclude Subnetworks for User Mapping in General Topics