- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
show counter global filter category flow aspect dos
- LIVEcommunity
- Discussions
- General Topics
- Re: show counter global filter category flow aspect dos
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
show counter global filter category flow aspect dos
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-24-2016 11:59 PM
Hi,
Below is output of 'show counter global filter category flow aspect dos'
What does it mean by value and rate . Does it mean '143291' packets dropped ?
| name | value | rate | severity | category | aspect |
| flow_dos_red_tcp | 1143291 | 0 | drop | flow | dos |
| flow_dos_pf_ipfrag | 57444 | 0 | drop | flow | dos |
| flow_dos_pf_icmplpkt | 1100 | 0 | drop | flow | dos |
| flow_dos_pf_tcpoverlappingmismatch | 20411 | 0 | drop | flow | dos |
| flow_dos_zone_red_max | 446965 | 0 | drop | flow | dos |
| flow_dos_zone_red_act | 696326 | 0 | drop | flow | dos |
| flow_dos_rule_drop | 403117 | 0 | drop | flow | dos |
| flow_dos_rule_drop_classified | 403117 | 0 | drop | flow | dos |
| flow_dos_rule_allow_under_rate | 3402693 | 0 | info | flow | dos |
| flow_dos_rule_allow | 35492603 | 21 | info | flow | dos |
| flow_dos_rule_match | 39298413 | 22 | info | flow | dos |
| flow_dos_rule_nomatch | 129318926 | 32 | info | flow | dos |
| flow_dos_no_empty_entp | 517212 | 0 | info | flow | dos |
| flow_dos_curr_sess_add_no_entp | 114095 | 0 | info | flow | dos |
| flow_dos_curr_sess_del_no_entp | 124207 | 0 | info | flow | dos |
| flow_dos_cl_curr_sess_add_incr | 72234191 | 27 | info | flow | dos |
| flow_dos_cl_curr_sess_del_decr | 72222602 | 28 | info | flow | dos |
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-25-2016 12:09 AM
"value" is the total number of packets that hit this counter since the last time the counters were reset (in many cases, the lifetime of this device)
the "rate" is the amount of packets being dropped in a relative window of time
the best way to determine/control the actual rate is by adding the 'delta' function to your show command and then running the command a few times with a few seconds or minutes in between. that way the delta will only show the actual increase in the counter
> show counter global filter category flow aspect dos delta yes Global counters: Elapsed time since last sampling: 2.110 seconds -------------------------------------------------------------------------------- Total counters shown: 0 --------------------------------------------------------------------------------
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-25-2016 01:45 AM - edited 04-25-2016 01:48 AM
Hi,
Thanks reaper .
Traffic shows incomplete to a server from a host . but the other host can reachable
So i was thinking it may due to the dos policy (zone protection or dos rule ). So how can i verify which policy casuing the 'incomplete'
But there is no log under threats
Thanks again
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-25-2016 02:27 AM
an incomplete is nearly never due to a policy (a policy would be a drop or reset). An incomplete is usually because a syn packet was sent out and an ack was never returned. this can be due to several network related issues: the host is unreachable, NAT was not applied, there is an asymmetric path, there is another firewall blocking the connection ....
if you are unsure what is causing the issue, you can set up packetcaptures to help determine what is going on
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-25-2016 03:31 AM
Hi,
If i change the client ip address it works .
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-25-2016 03:50 AM
there could be an IP conflict, subnetting issue, an access list on the server or possibly NAT not being applied to the whole subnet.
setting up a packetcapture for send, receive and drop stage may help
check out this getting started guide: Getting Started: Packet Capture
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-25-2016 04:29 PM
Hi reaper
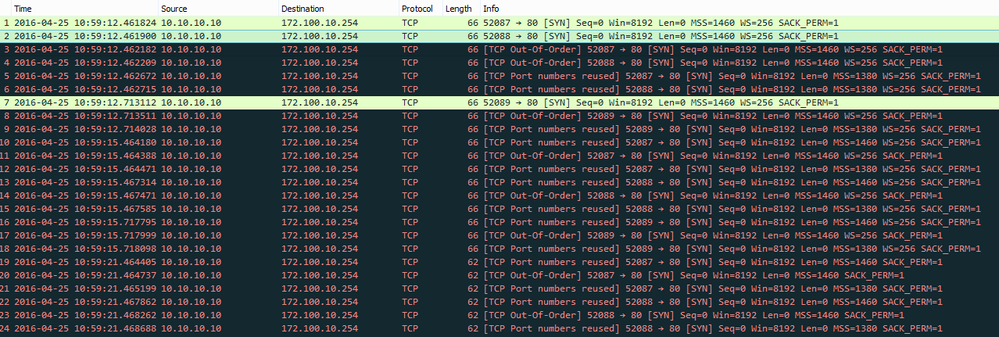
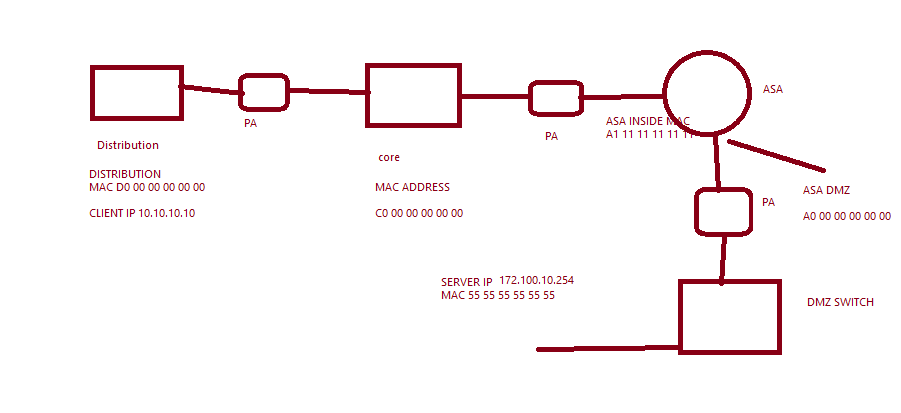
I have attached the rx capture file , and topology
filter : source 10.10.10.10 destination 172.100.10 .254
Please help to understand
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-26-2016 12:43 AM
Hi
so the pcap doesn't look good, there's only outgoing SYN packets and no reply
you indicate there are 3 PA firewalls ? i'd start by setting up pcaps on all 3 with these filters:
1 10.10.10.10 - 172.100.10.254 d-port 80
2 172.100.10.254 - 10.10.10.10 s-port 80
(unless there is NAT, then you'd need to adjust the IP's)
and if possible, also on the ASA
that will allow you to track the whole path the packets need to traverse so you can pinpoint where the link
-if you see the syn packet on all firewalls, you know it was delivered to the DMZ switch and something went wrong there
-if you see it on the first 2 PA's but not on the 3rd PA, you'll know it's on the ASA
-if you don't see it on the second PA you'll know it's going wrong on the core
since you're only seeing SYN packets, i'd also focus on the TX pcaps first, to make sure they're leaving the firewall
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-26-2016 02:26 PM
Actually there is only one physical firewall ,those three are in differnet zone
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-27-2016 01:03 AM
ok, that makes things a little more tricky 😉
did you make sure every single interface has a unique zone (the single session should go through 6 different zones)
have you checked the transmit (TX) stage of the firwall ? if you run a wireshark capture on the server, can you see the packet arriving ?
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-27-2016 09:37 PM
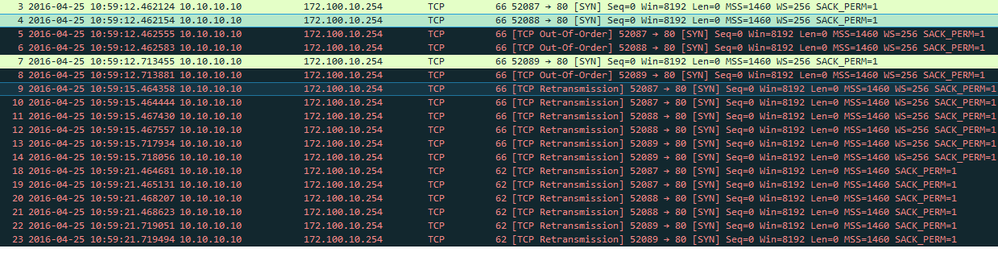
Hi
Here is the tx , it seems packets are leaving firewall ?
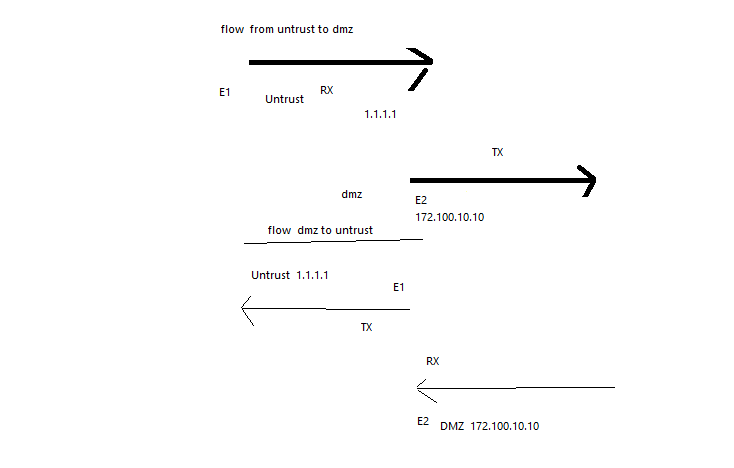
As per the below diagram rx of both interface will be recordeed in rx stage and tx in the tx stage,
At firewall stage what all will be recorded
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-27-2016 11:40 PM
if you see packets in the transmit stage, that means they are leaving the firewall on the egress interface
the tricky part in your case is that the packets go in and out of the firewall 3 times, but i only see 2 transmits (look for source port 52087) and then a retransmit, so according to your initial diagram, that would mean the ASA could be blocking your connection
the first transmit is from distri to core, the second entry is from core to asa, the third one should be asa to dmz
if you now compare the transmit to the receive, you can see if the receive also only has 2 entries, which means the packet from asa was not received, or if it has 3 entries, which means the 3rd leg of the PA firewall received and dropped the packet
PANgurus - Strata specialist; config reviews, policy optimization
- 4314 Views
- 11 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Packets dropped: forwarded to different zone in Next-Generation Firewall Discussions
- What's mean minus value and rate in global counter? in Next-Generation Firewall Discussions
- Global protect VPN disconnecting multiple times in GlobalProtect Discussions
- Receive errors on all traffic interfaces in Next-Generation Firewall Discussions
- how to allow NordVPN after done suggestion of BPA for advanced threat license in Next-Generation Firewall Discussions