- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
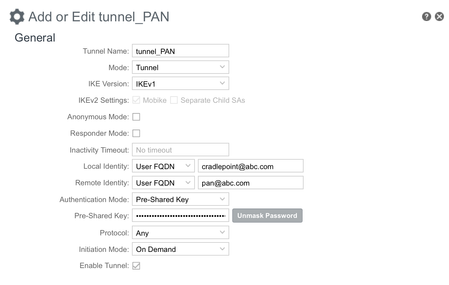
Site-to-Site IP Sec - PAN 220 [Static IP] to CradlePoint [Dynamic IP]
- LIVEcommunity
- Discussions
- General Topics
- Re: Site-to-Site IP Sec - PAN 220 [Static IP] to CradlePoint [Dynamic IP]
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-17-2020 08:00 PM
Does anyone have experience setting up an site-to-site IP Sec tunnel between a PAN firewall with a static IP address and a CradlePoint with a dynamic IP address? I am trying to determine if there's a way to setup the IP Sec tunnel between the 2 endpoints without having to pay a 3rd party for DDNS service.
I tried setting the firewall peering to Dynamic, and the IKE Phase 1 exchange modes to Aggressive, but no luck.
Any help is appreciated.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-18-2020 07:31 AM
try these for more detailed debug logs:
> debug ike gateway <gw> on debug
> tail follow yes mp-log ikemgr.log
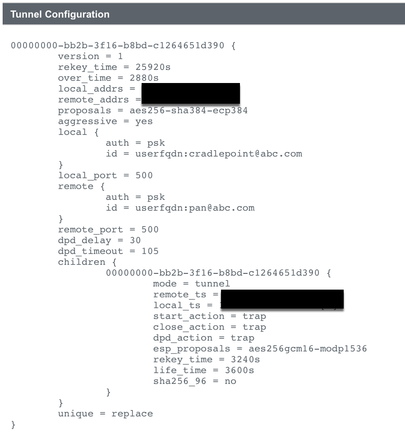
I noticed your local ip is 172.16x.x but you did not enable NAT-T, could you try turning that on?
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-17-2020 10:58 PM
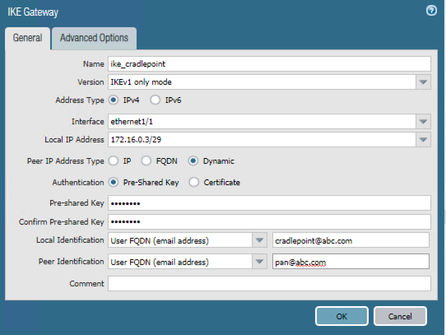
@acrxsupport-old What option have you selected under local/peer identification type? You need to select proper settings here. Also what do you see under system logs?
Mayur
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-18-2020 02:41 AM
as long as one side is static, this shouldn't be too difficult
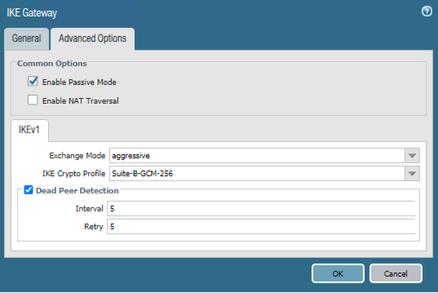
the PA will need to be set as 'passive' as it won't be able to connect out to the dynamic peer (without ddns) and you'll need to use set peer identification to some fictitious FQDN or email (or the local IP of the remote peer, if said peer lives behind a NAT device)
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-18-2020 04:00 AM
Thanks for the responses @reaper and @SutareMayur.
I've got Local and Remote Identities set on both, and it isn't coming up.
If I enable Passive Mode on the PAN, it hasn't actually responding to the IKE Phase 1 - even if I use a Static peer address instead of Dynamic. The system logs unfortunately also don't have anything showing up.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-18-2020 04:07 AM
I realized that I flipped the peering in the PAN IKE screenshot, this is corrected, but the results are the same.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-18-2020 07:31 AM
try these for more detailed debug logs:
> debug ike gateway <gw> on debug
> tail follow yes mp-log ikemgr.log
I noticed your local ip is 172.16x.x but you did not enable NAT-T, could you try turning that on?
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-20-2020 01:54 PM
@reaper thanks for your patience. This was very helpful for troubleshooting. It is working now with Responder Mode and NAT-T enabled, and using the matching identities.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-20-2020 01:59 PM
@acrxsupport-old that's great!
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-12-2023 09:30 PM
When using 'user FQDN (email address)' identity, is it a real email that the system checks? Or is it just a text string?
- 1 accepted solution
- 7326 Views
- 8 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!