- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Site-to-Site VPN - Palo alto to Cisco Router issue
- LIVEcommunity
- Discussions
- General Topics
- Re: Site-to-Site VPN - Palo alto to Cisco Router issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-16-2014 09:19 PM
Hi guys,
I'm doing a POC for S2S VPN but i cannot get it to work, I'm sure this is a simple thing i have overlooked, a ping from PC2 to PC1, the ping is encapsulated and encrypted ESP on the way over to PC1, but the return traffic is not..... i have the following topology;
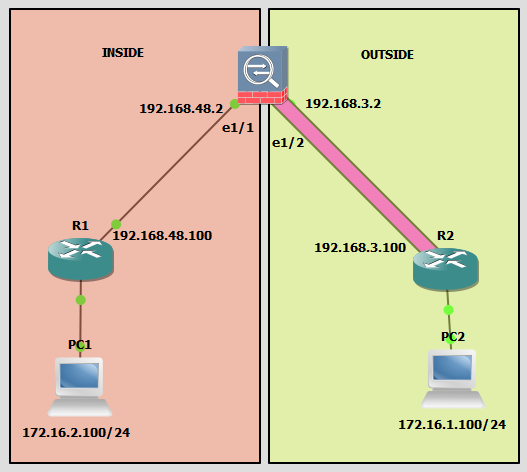
Now i have set up a site to site VPN from the PA to R2 with the following attributes;
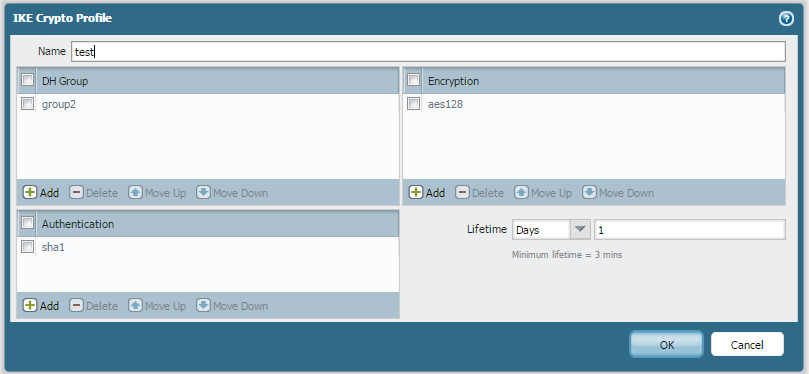
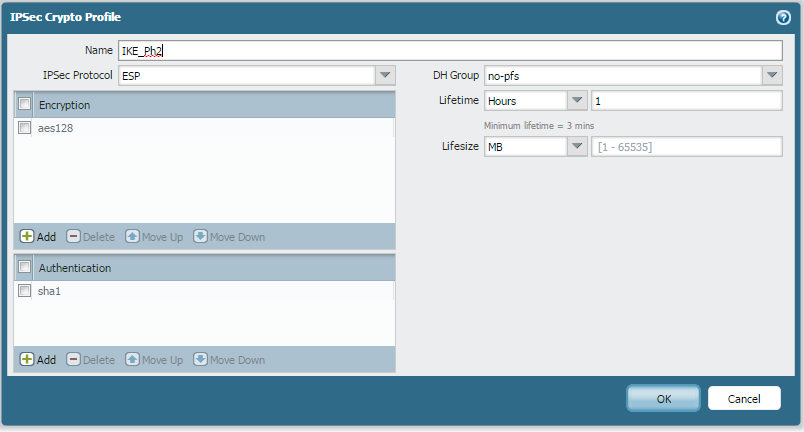
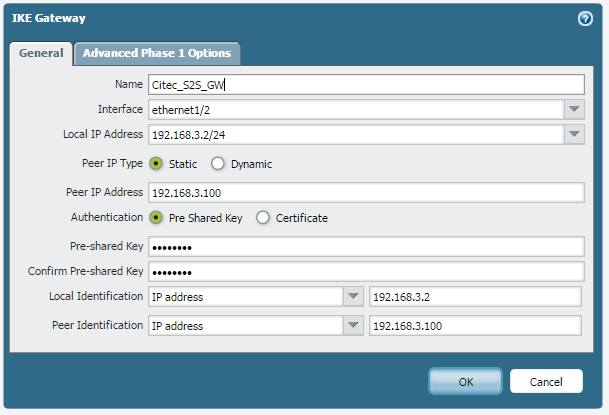

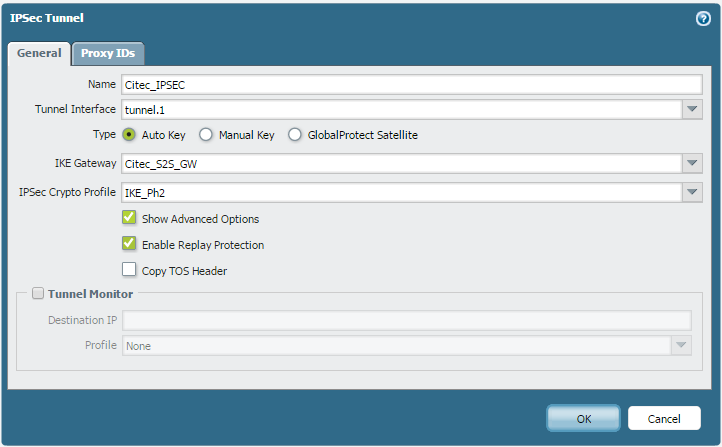
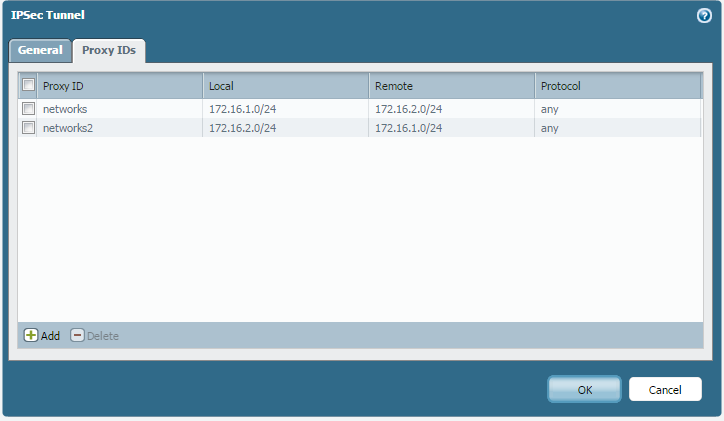
And with a ping from PC2 to PC1, IKE phase 1 and 2 come up.....but the ping fails
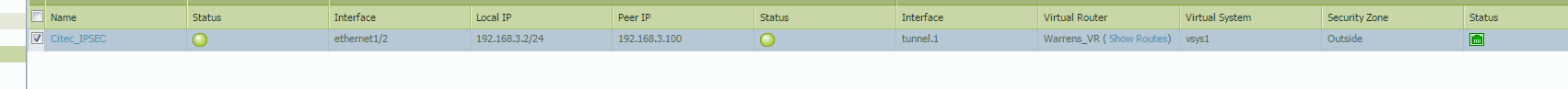
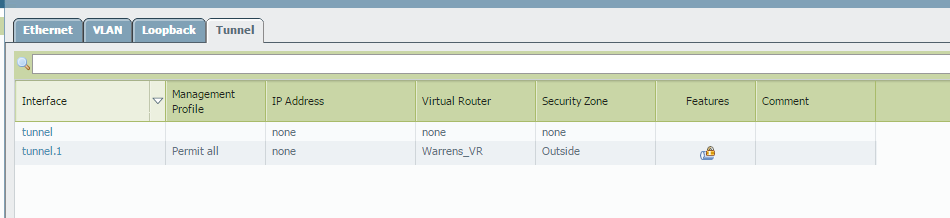
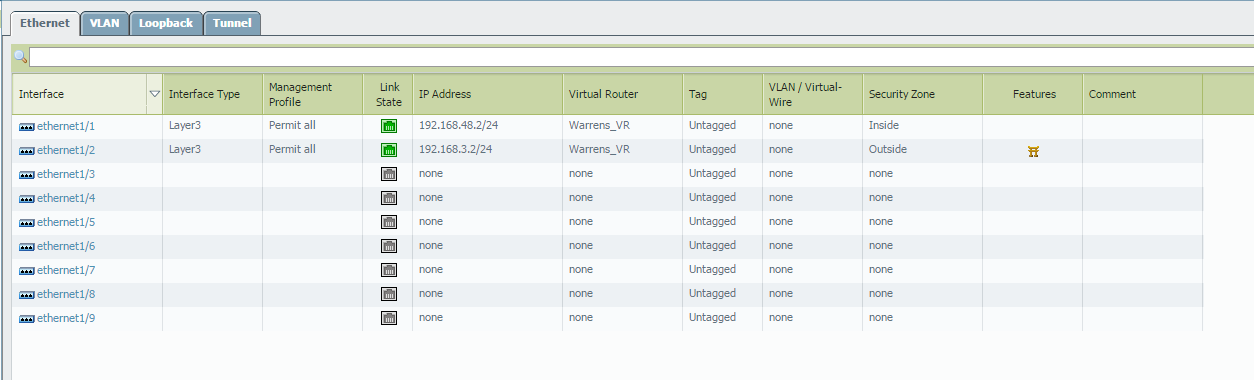
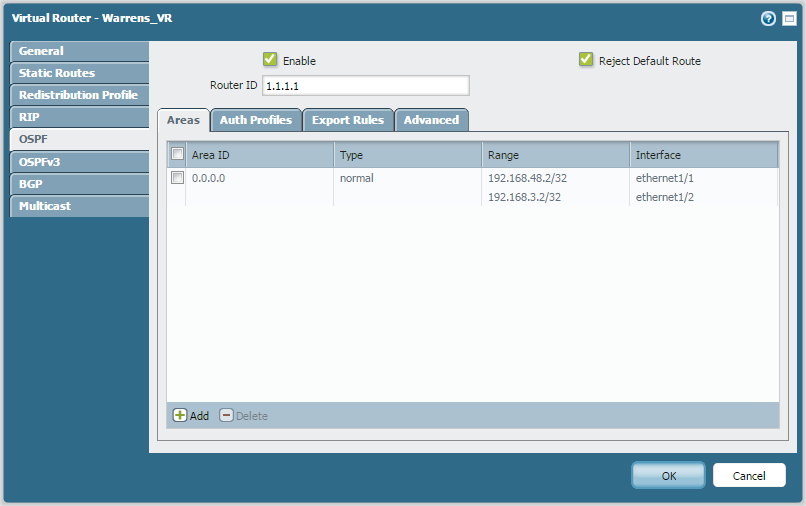
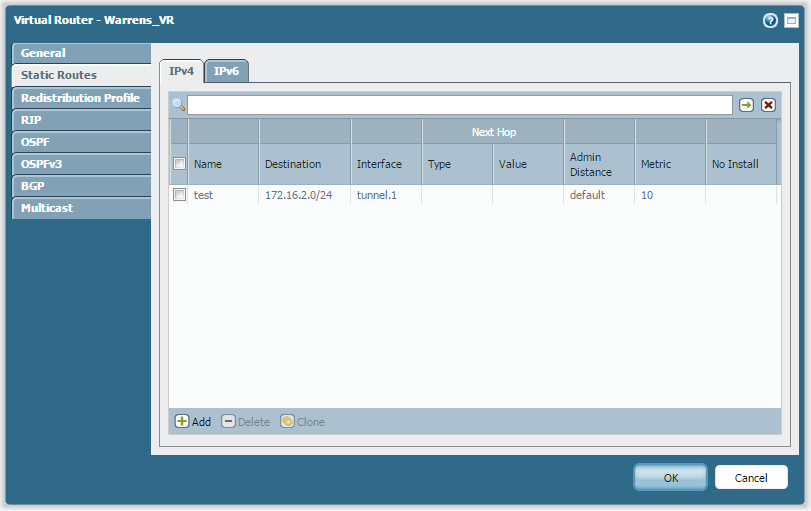
And the capture of the ping....outbound ESP, return traffic ICMP...
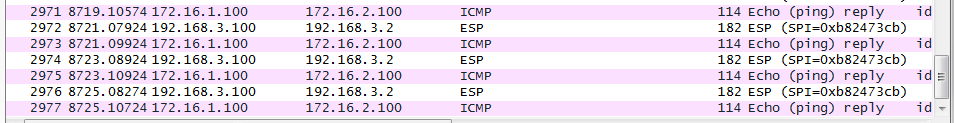
Confi on the Cisco router;
!
crypto isakmp policy 1
encr aes
authentication pre-share
group 2
lifetime 3600
crypto isakmp key cisco address 192.168.3.2
!
!
crypto ipsec transform-set Myset esp-aes esp-sha-hmac
!
crypto map Mymap 1 ipsec-isakmp
set peer 192.168.3.2
set transform-set Myset
match address 100
!
!
!
interface FastEthernet0/0
ip address 192.168.3.100 255.255.255.0
duplex auto
speed auto
crypto map Mymap
!
!
access-list 100 permit ip 172.16.2.0 0.0.0.255 172.16.1.0 0.0.0.255
access-list 100 permit ip 172.16.1.0 0.0.0.255 172.16.1.0 0.0.0.255
!
Any ideas guys?
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-17-2014 08:59 AM
Also I believe ACL configuration on the Cisco device is not correct. You mentioned same subnet in ACL source and destination.
"access-list 100 permit ip 172.16.1.0 0.0.0.255 172.16.1.0 0.0.0.255"
Regards,
P.Sarath
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-16-2014 10:13 PM
Hello netsupport1,
Could you please verify the VPN flow to ensure the encapand decappackets on this firewall. If only encap counter is increasing, but not the decap.Then you might need to check the other end of the VPN tunnel.
>showvpnflow
>showvpnflow tunnel-id x << where x=id number from above display
Hope this helps.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-17-2014 03:38 AM
Thanks Hulk,
See below for output
admin@PA-VM> show vpn flow
total tunnels configured: 2
filter - type IPSec, state any
total IPSec tunnel configured: 2
total IPSec tunnel shown: 2
id name state monitor local-ip peer-ip tunnel-i/f
-----------------------------------------------------------------------------------------------
7 Citec_IPSEC:networks active off 192.168.3.2 192.168.3.100 tunnel.1
9 Citec_IPSEC:networks2 init off 192.168.3.2 192.168.3.100 tunnel.1
admin@PA-VM>
admin@PA-VM> show vpn flow tunnel-id 7
tunnel Citec_IPSEC:networks
id: 7
type: IPSec
gateway id: 1
local ip: 192.168.3.2
peer ip: 192.168.3.100
inner interface: tunnel.1
outer interface: ethernet1/2
state: active
session: 107
tunnel mtu: 1428
lifetime remain: 3478 sec
latest rekey: 122 seconds ago
monitor: off
monitor packets seen: 0
monitor packets reply: 0
en/decap context: 3
local spi: 9183D0C8
remote spi: BA222D14
key type: auto key
protocol: ESP
auth algorithm: SHA1
enc algorithm: AES128
proxy-id local ip: 172.16.1.0/24
proxy-id remote ip: 172.16.2.0/24
proxy-id protocol: 0
proxy-id local port: 0
proxy-id remote port: 0
anti replay check: yes
copy tos: no
authentication errors: 0
decryption errors: 0
inner packet warnings: 0
replay packets: 0
packets received
when lifetime expired:0
when lifesize expired:0
sending sequence: 0
receive sequence: 4
encap packets: 0
decap packets: 4
encap bytes: 0
decap bytes: 544
key acquire requests: 0
owner state: 0
owner cpuid: s1dp0
ownership: 1
admin@PA-VM> show vpn flow tunnel-id 9
tunnel Citec_IPSEC:networks2
id: 9
type: IPSec
gateway id: 1
local ip: 192.168.3.2
peer ip: 192.168.3.100
inner interface: tunnel.1
outer interface: ethernet1/2
state: init
session: 2
tunnel mtu: 1448
lifetime remain: N/A
monitor: off
monitor packets seen: 0
monitor packets reply: 0
en/decap context: 2
local spi: 00000000
remote spi: 00000000
key type: auto key
protocol: ESP
auth algorithm: NOT ESTABLISHED
enc algorithm: NOT ESTABLISHED
proxy-id local ip: 172.16.2.0/24
proxy-id remote ip: 172.16.1.0/24
proxy-id protocol: 0
proxy-id local port: 0
proxy-id remote port: 0
anti replay check: yes
copy tos: no
authentication errors: 0
decryption errors: 0
inner packet warnings: 0
replay packets: 0
packets received
when lifetime expired:0
when lifesize expired:0
sending sequence: 0
receive sequence: 0
encap packets: 0
decap packets: 0
encap bytes: 0
decap bytes: 0
key acquire requests: 0
owner state: 0
owner cpuid: s1dp0
ownership: 1
admin@PA-VM>
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-17-2014 05:57 AM
Looks like you are decrypting packets but not encrypting packets. This means we need to look at your end. If packets are coming across that means the tunnel is built and configured properly. Usually this points to a Routing/ACL issue so we need to look at why your replys are not being sent into the tunnel.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-17-2014 07:33 AM
Hi,
Adding to what Hulk suggested, it is something with the routing table that I am worried about. I would like to know if the static route for the tunnel traffic is redistributed over OSPF. Can you please check the routing table on the PA to know if you are learning all the routes and are we taking the right static route to send and receive traffic through the defined tunnel interface. Probably the following command test routing fib-lookup ...... should help you know if we are forcing traffic on the static route defined. Also show routing route should give us the summary.
Please see if this track of investigation helps you.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-17-2014 08:07 AM
Hi,
This looks like configuration issue. You created static route for "172.16.2.0/24" pointing towards tunnel.1. However, you created tunnel between PA and R2 router. So you need to create static route for 172.16.1.0/24 and next hop as tunnel interface and redistribute this static route into OSPF. Also you need to remove the static route which configured for "172.16.2.0/24".
Regards,
P.Sarath
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-17-2014 08:57 AM
Agreed, according to the drawing the wrong subnet is pointed at the tunnel.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-17-2014 08:59 AM
Also I believe ACL configuration on the Cisco device is not correct. You mentioned same subnet in ACL source and destination.
"access-list 100 permit ip 172.16.1.0 0.0.0.255 172.16.1.0 0.0.0.255"
Regards,
P.Sarath
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-17-2014 02:28 PM
So sorry guys, i documented the topo wrong, the two LAN subnets are swapped;
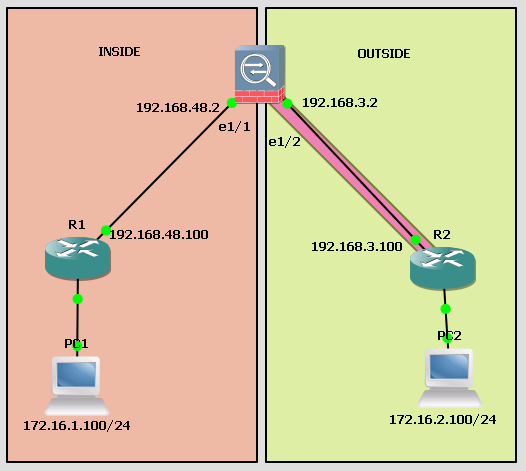
So the static is correct i believe, 172.16.1.0/24 to tunnel .1
Thank you all so so much for your help thus far, sorry about the bum steer!
regards
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-17-2014 02:47 PM
So I think your problem is a typo in the ACL configured on the router. Make sure you have it like this:
access-list 100 permit ip 172.16.1.0 0.0.0.255 172.16.2.0 0.0.0.255
access-list 100 permit ip 172.16.2.0 0.0.0.255 172.16.1.0 0.0.0.255
Thanks,
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-17-2014 03:14 PM
Ok so i have a confession to make, the hosts you see in the topo above aren't real, they are loopbacks, and i was sourcing pings from the loopback but it just wasn't working as stated, this morning i made them "real"" hosts and it all worked, i'm not 100% on why
I'm so thankful for your offered help, it's my first enquiry in this forum and i am impressed, being a Cisco guy i was a little doubtful that i would get a resolution ....wow! how wrong i was!
Thankyou all!!!!
- 1 accepted solution
- 16208 Views
- 10 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Prisma Access with ECMP in Prisma Access Discussions
- Unable to reach Palo Alto - Global Protect Portal. in GlobalProtect Discussions
- NATing Question in General Topics
- static route with path monitor down not removing BGP route in General Topics
- Struggling to Unset Virtual Router from Interface via API – Manual Works, API Always Fails in General Topics



