- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
SSL decryption presenting untrusted certificate for certain site
- LIVEcommunity
- Discussions
- General Topics
- Re: SSL decryption presenting untrusted certificate for certain site
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
SSL decryption presenting untrusted certificate for certain site
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-01-2016 11:01 AM
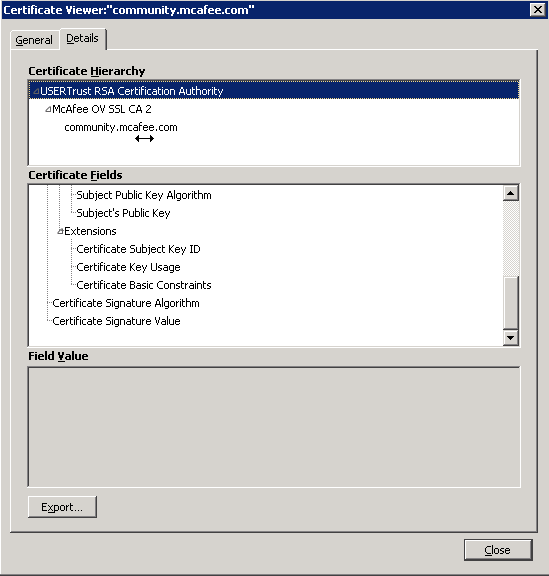
Can somebody explain why the PA is presenting the untrusted certificate when browsing to https://community.mcafee.com ?
So far all of the other HTTPS sites that I've tested have worked perfectly. This is on 7.1.3.
I opened a ticket with PAN and the tech said it's because the PAN doesn't trust some of the CA's used by that site's certificate, but I'm confused why the browsers trust it then?
Thanks.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-03-2016 01:17 AM
Palo Alto have certificate store and in that store we keep root CA certs. The Root CA of the website that you are visiting is not there in the store that's why you are getting that untrusted cert. If you google for the root ca usertrust RSA certification authority you will find people are complaining about the cert.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-26-2018 09:26 AM
Sorry for bringing up an old post, but this came up in my search and I just wanted to add to the explanation here.
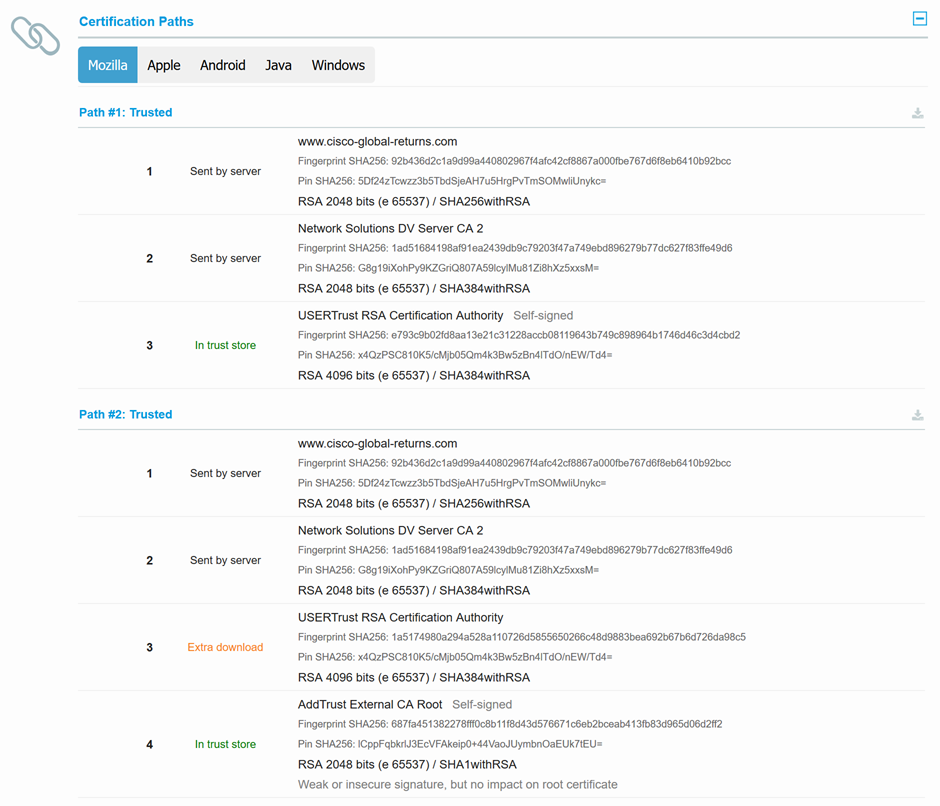
You can test the SSL certificate for any site here: https://www.ssllabs.com/ssltest/analyze.html. If the Certification Paths indicates that one of the certificates required an "extra download", then that is an indication that the remote site did not properly include all certificates in the chain in their SSL Handshake.
For example, I was having problems with https://www.cisco-global-returns.com.
In the Certification Paths section, we can see that the server did not provide the full certificate chain as it should (Sent by server). You can see that the certificate USERTrust RSA Certification Authority was not sent by the server, so the testing site had to download the certificate.
While this is technically a problem with the configuration at the remote site, users will be frustrated that the site works properly when browsed from networks not under Palo Alto SSL Decryption. To work around this problem, you can import the missing Intermediate certificate into your firewall. Note however, that you will now take responsibility for ensuring that the certificate you just imported has not been revoked, so use your best judgement here.
Directions for importing an Intermediate Cert: https://live.paloaltonetworks.com/t5/Management-Articles/How-to-Import-the-Intermediate-CA-on-the-Fi...
- 14010 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- web file blocking in Next-Generation Firewall Discussions
- High Data Plane Utilization During Business Hours in Next-Generation Firewall Discussions
- Trendmicro application identified as "ssl" despite of proper SNI, CN, SAN. in General Topics
- No "certificate used by" field when generating certs for SSL forward trust and untrust? in General Topics
- Azure "az" command and decryption in Next-Generation Firewall Discussions