- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Suspicious TLS Evasion Found(14978)
- LIVEcommunity
- Discussions
- General Topics
- Suspicious TLS Evasion Found(14978)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Suspicious TLS Evasion Found(14978)
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-13-2021 06:29 AM
Dear Team,
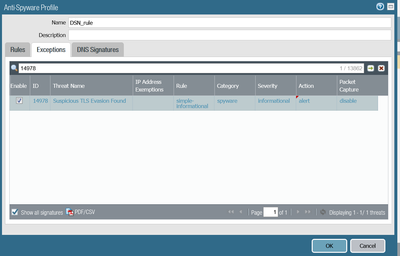
I have configured the web service behind PA. and attached the security profile . i can see in the thread logs the thread is generating "Suspicious TLS Evasion Found(14978)".
i have gone through the below KB but didn't understand
moreover, I can see the thread signature is showing in excpetion so I have enabled this and put the action is alert. the severity is informational. do i need to take any action on this?
the severity is informational
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-13-2021 10:55 AM
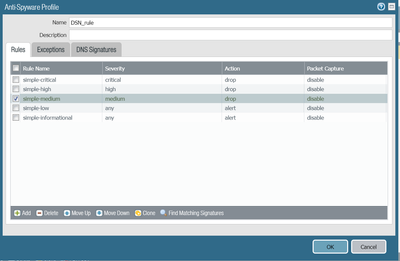
Please see our best practices guide here, in which we recommend changing the default alert behavior to drop.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-13-2021 01:58 PM
The piece that is actually relevant to your alert:
Evasion signatures that detect crafted HTTP or TLS requests can send alerts when clients connect to a domain other than the domain specified in the original DNS request. Make sure to configure DNS proxy before you enable evasion signatures. Without DNS proxy, evasion signatures can trigger alerts when a DNS server in the DNS load balancing configuration returns different IP addresses—for servers hosting identical resources—to the firewall and client in response to the same DNS request.
If you haven't used a DNS proxy object you can ignore these alerts, or override the action to allow so you don't have them filling up your threat logs. By default the 14978 signature is actually already set to allow, so you've actually modified the default action or setup a policy that otherwise overrides the default action for simple-informational alerts to receive any notice about these threats to begin with.
I'd recommend that you either configure the dns proxy object and get that setup so the signature actually functions correctly, or you set the action back to allow. Without the DNS proxy configured they aren't going to work effectively, which is why they are setup as informational allowed threats.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-13-2021 11:29 PM
@BPryI have checked, according to the below documents the best practice is we should set the action drop for the evasion signature 14978.
moreover, if i set the action drop so the service is stopped and drop all the traffic for my server, that I have attached the antispyware profile.
i have configured below antispyware profile:-
so now, i want to allow the traffic but an alert should not come. what i need to do.
- Do i need to allow the traffic instead of alert in the exception?
- If alerts are coming so i can ignore?
- or to work properly do i need to configure the DNS proxy. i believe if i configure the DNS proxy and if i will put in the antispyware rule and exception all the things is drop. it will work or not?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-15-2021 09:13 AM
DNS Proxy just allows the firewall to cache DNS responses and forward to your internal server, if you choose. See here. You *must* configure a DNS proxy for the TLS evasion blocks to work properly.
- 5917 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- XDR - Unable to clear user's APPDATA in Cortex XDR Discussions
- Suspicious Executable Detected in Cortex XDR Discussions
- Cortex XDR flagged malicious macros in Cortex XDR Discussions
- How can I get the scores of the indicators I extract with commands? in Cortex XSOAR Discussions
- Generate traffic report to identify any suspicious traffic in General Topics