- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Tagged subinterface in different zone than parent not working
- LIVEcommunity
- Discussions
- General Topics
- Re: Tagged subinterface in different zone than parent not working
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Tagged subinterface in different zone than parent not working
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-11-2017 12:59 PM
So up to this point I'd only been using tagged sub interfaces for capacity\housekeeping\etc, so they were all in the same security zone. Now I have a case where I'd like to be able to add some rules to where traffic from this new VLAN can go..
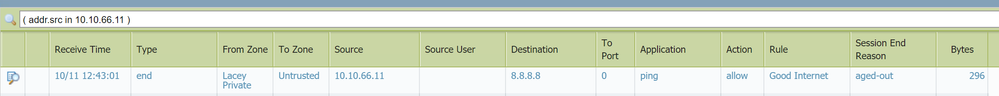
I put the new sub interface in a new zone, add the new zone to the general internet access rules and outbound NAT rule.. no love.. So I look in at the traffic monitor, I see the traffic but it has a source zone of the parent interface, not the zone it is configured with.. am I missing somthing obvious here?
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-11-2017 01:16 PM
Monitor > Traffic
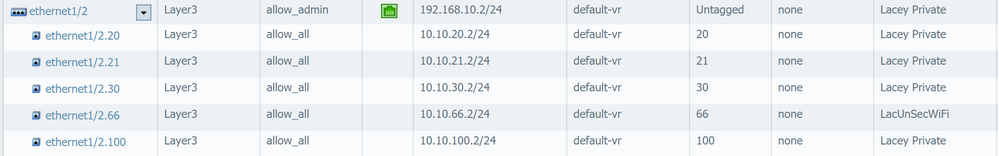
Add Ingress I/F column. Are those packets coming in from ethernet1/2.66 interface?
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-11-2017 02:22 PM
Hmmm.. No it says the are coming from the parent interface ethernet1/2.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-11-2017 03:09 PM
In this case your vlans are messed up. Maybe wifi access point is in incorrect vlan.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-12-2017 05:25 AM
if your traffic log is showing the sessions in the wrong zone you're probably receiving them untagged. your original source may be connected to an untagged switch port or your trunk/switch doesn;t support/isnt configured for the vlan tag you configured on the subinterface
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-12-2017 05:51 AM - edited 10-12-2017 07:09 AM
I agree with reaper. the tell-tale signs are there to support that particular view ...
Can you share the switch/router port/interface config here with us ...
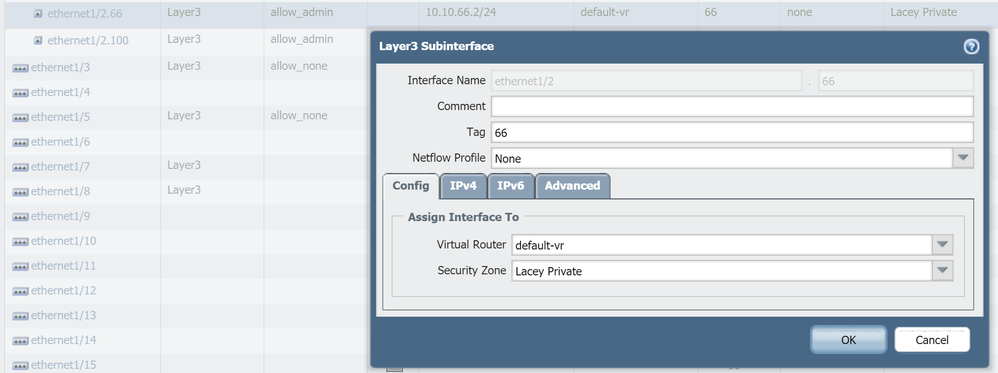
And also can I please ask you to confirm that you have set 'Tag' on the Palo side?
Ajaz Nawaz | Network & Security Consultant
JNCIE-SEC #254 | CCIE-RS #15721
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-19-2017 12:47 PM
I think I figgured out why this is happeing.. I have a Layer 3 core switch that sits in front of the PA and does inter VLAN routing. The only route it has to the interwebs is it's default gateway which is the 192.168.10.2 address of the parent interface on the PA. This setup works and VLAN traffic makes it's way to the interwebs. If I remove the Tagged subinterface for a VALN from the config, traffic for that VALN stops at the 192.168.10.2 interface. To be 100% honest I'm not clear on WHY this actually works, tagged VLAN traffic is being forwarded to an untagged interface, perhaps it has to be with the way PA is doing the subinterface? Anyhow, I think for this to work the way I want it to, traffic from each VLAN needs to be forwarded to the subinterface. The only way I can come up with to do this, and leave the core layer 3 switch doing inter VLAN routing, is to move to Policy Based Routing.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-19-2017 01:15 PM
this is the pertanant config from the core switch. and the sub interface on the PA
ip route 0.0.0.0 0.0.0.0 192.168.10.2
ip routing
interface 1
name "To PA Eth 2"
exit
vlan 66
name "UnSecuteWiFi-66"
tagged 1,A1
ip address 10.10.66.1 255.255.255.0
ip helper-address 192.168.10.216
exit
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-19-2017 02:37 PM
the 1st screen cap is a nonworking config.. the second screen cap is a working config
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-19-2017 02:39 PM
One other thing we do to cut down on the nmber of Zones, is to use Zones and Source IP's. That way you can write a rule with source zone and ip range.
Just another thought.
- 8989 Views
- 10 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Cortex XDR Agent & MDE in Endpoint (Traps) Discussions
- Cortex XDR Broker VM content cashing verification in General Topics
- Max number of units (aeX.Y subinterfaces) supported under a single AE interface? in Next-Generation Firewall Discussions
- Windows-Remote-Management & Implicit Use of Web-Browsing in General Topics
- Cortex XDR – Unable to Assign Read/Write Permissions for Mobile Device (Detected as CD-ROM) in Permanent Exceptions in Cortex XDR Discussions