- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Threat False Positives?
- LIVEcommunity
- Discussions
- General Topics
- Re: Threat False Positives?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-10-2018 05:08 AM
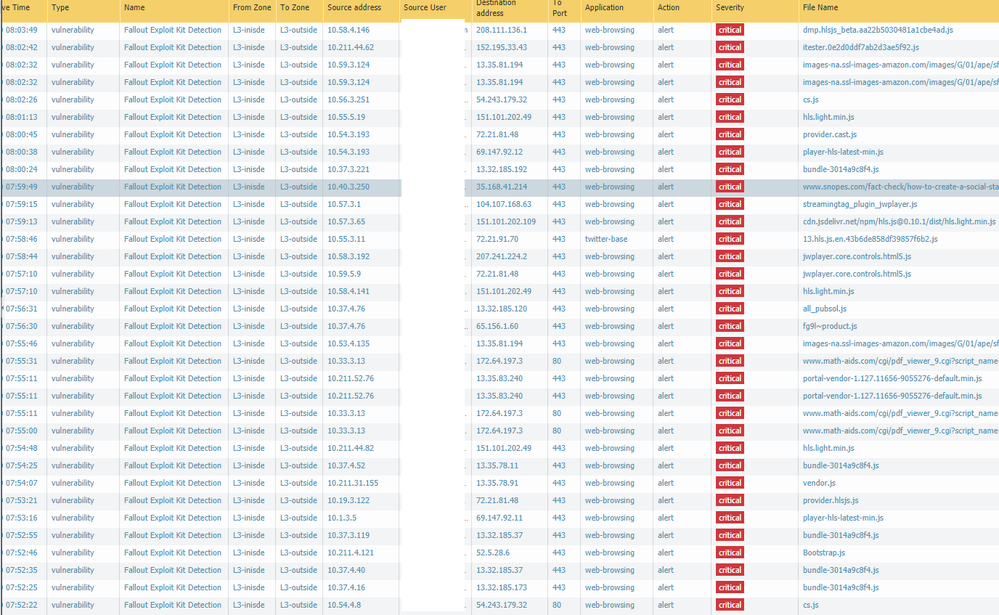
Our threat logs are full of 'Fallout Exploit Kit Detection' this morning from many of our networks, although no actul issues have been found.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-10-2018 06:14 AM - edited 10-10-2018 06:17 AM
Same here...I installed 8077 this morning when I get in after reading the email and I'm getting Fallout alerts like crazy. I don't have as many as you, but people just starting coming in.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-10-2018 06:39 AM
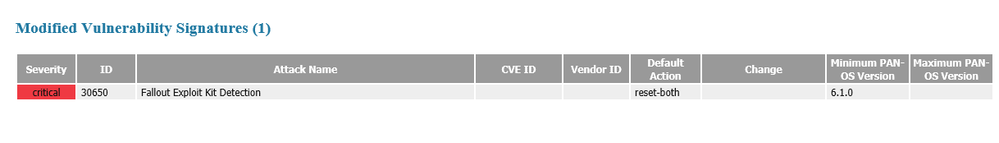
For the time being I would recommend rolling this back to 8076. The Fallout siganture has actually been around since 8074, but whatever modification PA has done to the signature is a tad to broad at the moment.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-10-2018 06:56 AM - edited 10-10-2018 07:05 AM
I'm rolling back to 8076 and I'll report back what happens. I was getting a detection about every minute or multiple per minute with 8077.
Edit: 8076 seems to have stopped the mass amount of alerts.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-10-2018 07:00 AM
Hello,
Looks like this was the emergency update that came out last night:
I usually set my dynamic updates with a threshold that will allow the updates to bake since they have released bum updates in the past. I understand there are some environments where this is not possible.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-10-2018 07:27 AM
I m rolling back to 8076 - and alers from IPS disappear.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-10-2018 07:32 AM
Yeah, we are also getting a lot of the Threat ID 30650 events. All events seem to include a *.min.js or *.js file name.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-10-2018 07:36 AM
I had the same files - *.js
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-10-2018 07:36 AM
I do the same... I'm usually a week behind because their updates have burnt me in the past several times. This one seemed urgent so I manually updated this morning. I guess that was a mistake.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-10-2018 07:41 AM - edited 10-10-2018 07:47 AM
..Palo Alto - not often makes mistakes in signatures... but .... 🙂 it happend...
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-10-2018 08:00 AM
Agreed, no one is perfect. I usually have a 24 hour threshold on any new signatures for app/threat.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-10-2018 09:12 AM
Same here. PaloAlto 5050 with Application and Threat Version 8077-5070.
Many critical threat log entrys with name-of-threatid eq 'Fallout Exploit Kit Detection' as false-positives.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-10-2018 09:20 AM
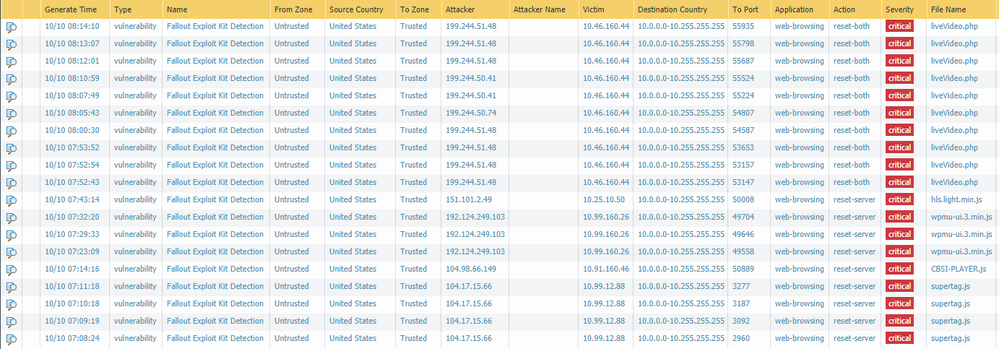
I looked at the js files being flagged. there must be something in them that is a close match. since these are not critial .js files I am leaving the block in place for now. Has anyone reported this to PA yet?
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-10-2018 09:25 AM - edited 10-10-2018 09:39 AM
I just opened a case with PA to see what they say. So far it's creating an issue for one website we use, blocking a particular js file from loading and rendering the website inoperable.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-10-2018 10:47 AM
FYI,
8078 was just released that is suppose to address the issue.
- 1 accepted solution
- 11309 Views
- 17 replies
- 2 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- False positive (generic.ml): HelpDesk Viewer in VirusTotal
- False Positive request for RemotePC HelpDesk Viewer in VirusTotal
- False positive : HelpDesk Viewer in VirusTotal
- Multiple High/Critical Alert Detected via Port 18264 | Possible FP in General Topics
- Multiple High/Critical Alert Detected via Port 18264 | Possible FP in VirusTotal