- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Traffic denied by one context is allowed in the other
- LIVEcommunity
- Discussions
- General Topics
- Re: Traffic denied by one context is allowed in the other
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Traffic denied by one context is allowed in the other
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-13-2014 11:14 PM
Hello All,
I have a strange situation and need some help.
I have 2 legs of my firewall implemented on Core and Edge level.
I have a host 10.1.1.10 behind my Core layer firewall trying to access an external FTP server.
On the core layer I have a policy to deny ftp traffic from inside to outside and the logs show the traffic is denied.
But on the Edge level i see one more traffic log saying allow for the same traffic. ( Edge has a rule to allow any type of traffic)
The default gateway of Core firewall is pointing towards the edge firewall.
Any help on this is much appreciated.
Thanks.
Srikanth
- Labels:
-
Configuration
-
Troubleshooting
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-14-2014 12:57 PM
Hello Srikanth,
If you enable packet capture on the PAN firewall, please verify, if any packet received or transmitted through PAN.
Also, you can check the real time session in the CLI by using 'show session all filter source IP_ADD_OF_THE_TESTING_PC destination IP_ADD_OF_THE_DESTINATION'.
> If there is a session exist for the same traffic, then please apply CLI command PAN> show session id XYZ >>>>>>>> to get detailed information about that session, i.e NAT rule, security rule, ingress/egress interface etc.
Hope this helps.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-15-2014 03:42 AM
Hi Srikanth
If you enable packetcaptures you'll likely see that the edge firewall is receiving a tcp handshake (and is logging an accept action for that)
On your core firewall you are blocking based on application, but that application can only be determined after several packets have passed through that allow the forewall to positively identify ftp. In this case the tcp handshake will need to be allowed through before the first ftp packet is seen, identified and denied. by that time the edge firewall has also seen the handshake and has a session open pending the next packet, which will never arrive as the core firewall blocked it.
If you want a more strikt policy you can add service ports to your security policy which will block traffic before it requires identification. setting a block policy for port 21 will block normal ftp from the very first packet. on the other hand, using only the service port will not block an application if it is running on a different port (hence the power of appID), buit will require some packets (tcp handshake) to be trickled through for the process to function properly
hope this helps
Tom
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-15-2014 01:39 PM
Hi Srikanth,
Agree with what tpiens had to say. Also wanted to mention that there are users who try to use application default service in the security policy blocking FTP traffic so that traffic only on tcp port 21 is blocked. But this is not recommended. If you are trying to block FTP traffic, it is better to block on all service ports instead of default ports only.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-15-2014 01:45 PM
Hello All,
I was thinking about the same to determine the application palo alto needs several packets to understand the behaviour.
But the same thing is not happening for other tcp traffic like http and https and we have verified this.
Also just in case if there are 2 contexts of firewalls used for 2 different companies then seeing one firewall log on the other is a serious concern.
Support team isn't able to help me in this as well.
Thanks,
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-15-2014 01:58 PM
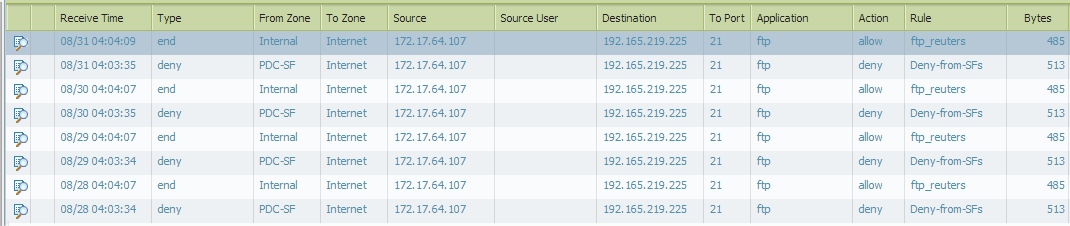
Please follow the logs from bottom to top
The host 172.17 is inside the core network and is being denied by the Core firewall.
The same traffic is reaching the Edge firewall and is being allowed according to a rule configured on the Edge firewall basically permitting ftp access outside.
Any help on this?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-15-2014 02:07 PM
Are you expecting that the traffic will never reach the Edge firewall because of the deny policy on the Core, and therefore you should not even see a session on the Edge?
Are the Core and Edge firewalls different vsys on the same physical device?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-15-2014 04:01 PM
Hi Srikant,
There is 40 second delay between similar traffic logs. If traffic log was generated because of same packet than log should have been generated immediately.
Regards,
Hardik Shah
- 6476 Views
- 8 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Multiple High/Critical Alert Detected via Port 18264 | Possible FP in General Topics
- Multiple High/Critical Alert Detected via Port 18264 | Possible FP in VirusTotal
- Windows-Remote-Management & Implicit Use of Web-Browsing in General Topics
- Security Policy with Destination Criteria in Strata Cloud Manager
- Whatsapp (IOS) Traffic not recognized in PaloAlto Firewall in General Topics



