- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
User-ID not mapping all traffic
- LIVEcommunity
- Discussions
- General Topics
- Re: User-ID not mapping all traffic
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
User-ID not mapping all traffic
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-01-2020 02:41 PM - edited 06-01-2020 02:44 PM
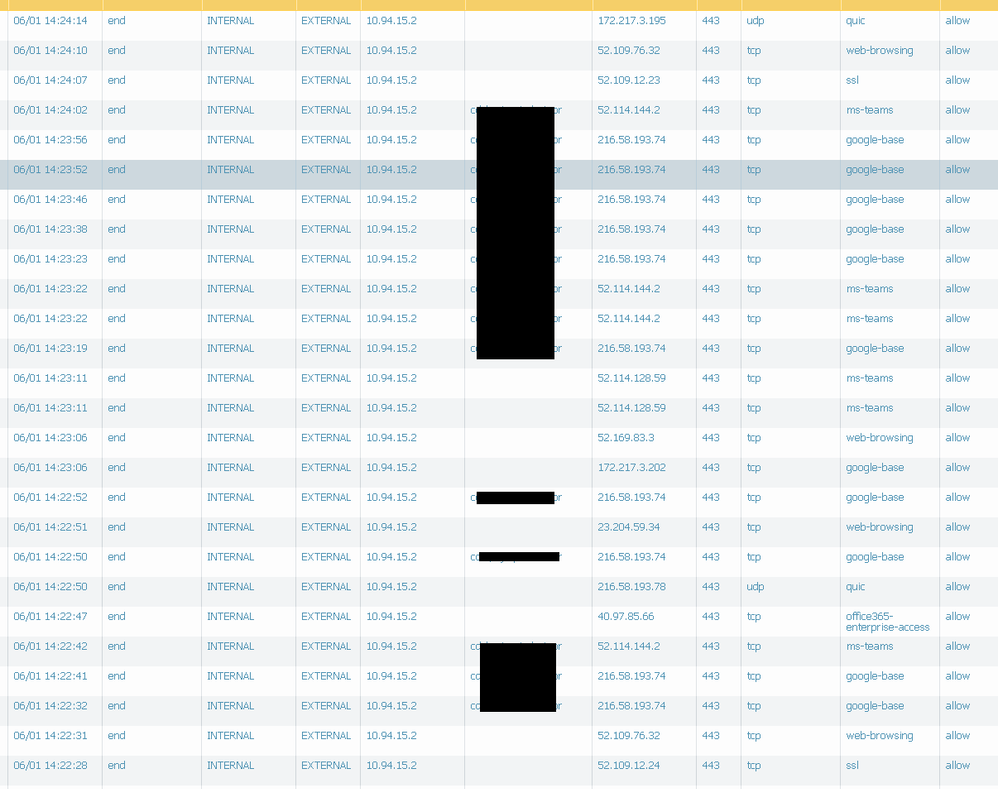
Why the user-id is missing for some traffic. This also causes issue with policies using user-id.
Below traffic log is for same user/zone/ip
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-01-2020 09:16 PM
@staustin We have agent-less configuration to pull user-ID's from domain controllers
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-02-2020 03:27 PM
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-03-2020 03:59 AM
You might have the timeout set too low. Default is 45 mins. I have mine set to 24 hours. Some suggest 8 is OK but it depends on domain activity.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-03-2020 11:53 AM
@Mick_Ball We have it for 15 hours and even if it was 45mins that would not explain why within matter of minutes there is username associated for some traffic while not for other.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-03-2020 12:25 PM
Yes i can now see that in your original post. How many servers are you monitoring. Could it be that one of them is not reading the security logs correctly and overwriting the correct information.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-03-2020 01:50 PM
Hello,
If you are using exchange, I would suggest checking against it. The reason is that when Outlook is open it is authenticating very frequently.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-03-2020 08:06 PM
@Mick_Ball and @OtakarKlier Thanks for suggestions. But how would i check/determine if some server is not reading security logs correctly. We are using 3 of them. Also there is no exchange server, its O365 that we have.
I did install agent on 1 of them and it seems better, but i will monitor and update
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-03-2020 10:00 PM
To test this i would remove 2 servers from user id and see what happens, then add a second, monitor, then add the third.... it should not cause any issues as you seem not to be using id’s for policies.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-05-2020 10:40 AM
this has become some serious issues in my environment. I have 20 firewalls and 10 ipsec site to site.
the recent issue I just realized is that if a user on GP crossing ipsec tunnel from PA to PA, the user id will be dropped at the destination,
and now all the rules will be denying because it can not see the username.
this is very unstable, since 2017, I have been opening tickets 2~3 times a year and still no solid solution.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-05-2020 12:01 PM
Some critical information is missing from your explanation but I will assuming your setup is the following:
1. UserA connects via GP to FirewallA
2. UserA then accesses a resource behind FirewallB
3. FirewallB has an ipsec s2s tunnel to FirewallA and this is how GP users are reaching the resource behind FirewallB
If the above is true, then FirewallB needs to be receiving redistributed GP mappings from FirewallA. FirewallB doesn't magically know about the ip to user mapping of UserA that is known to FirewallA. FirewallB must be told wha the ip to user mapping is by configuring user-id redistribution.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-05-2020 12:24 PM
you are right on the setup.
and I have user identification enabled on the tunnel ZONEs, and both firewall A and B are pointed 4 AD servers for monitoring and user id mapping.
but Im guessing I would need the redistribution ?
?
thanks for your reply.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-05-2020 12:26 PM
Your guess is correct, you do need user identification, but you also need redistribution. User identification turns on the ability to learn mappings and redistribution actually sends the mapping from FirewallA to FIrewallB.
- 8623 Views
- 13 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Windows User-ID Agents in Azure - Domain Normalization Not Working in General Topics
- Group Mapping Nesting LDAP Filters in General Topics
- USER_ID mapping constantly changing with Zscaler App in Next-Generation Firewall Discussions
- UserID domain name wrong in Next-Generation Firewall Discussions
- User having issues accessing internet after connecting to Global Protect -- Userid in GlobalProtect Discussions