- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
VPN Palo Alto - Microsoft Azure. Slow transfer. Not reaching internet by this tunnel.
- LIVEcommunity
- Discussions
- General Topics
- Re: VPN Palo Alto - Microsoft Azure. Slow transfer. Not reaching internet by this tunnel.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
VPN Palo Alto - Microsoft Azure. Slow transfer. Not reaching internet by this tunnel.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-06-2016 02:48 PM
Hello,
We are having a annoying issue :S We have configured a tunnel routed-based between PA (7.0.6) to Microsof azure. The tunnel is up but we are detecting several problems.
1) The transfer speeds are very low, fluctuate and are nothing stable: When we try to move a file using this tunel from Azure to one of our servers in PA, the transfer speed is so slow (200-300Kb/s). But if we use a RAD (windows machine which go up the tunnel) the transfer speed is 7Mb/s). Why the speed is slow if the PA bring up th tunnel?
2) The Azure server is not reaching internet through this tunnel. In addition, the server is still unable to navigate to the outside. We do not see in PA that traffic comes to us from Azure.
Coming from Azure, we only see in PA connections to internal networks, when all traffic from Azure (to internal or to EXTERNAL) should go in the tunnel.
If we want that this Azure server goes to internet using this tunnel its necessary to configure tunnel ikev2 and dynamic.These are requisites of Microsoft Azure. WE have configured all of this but we cant reach internet using tunel to PA.
We have tried to changed the MTU and several paramethers in VPN but its stilll hapening......any idea???'
thanks a lot
So that the server can browse to the outside our tunnel, the tunnel need to talk IKEv2 and that is dynamic, are the requirements of Azure.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-07-2016 01:01 PM
Hello,
Yes you are right. In order to initiate the tunnel in IKE-V2, we have to create the dynamic-gateway in AZURE side. On PAN FW we can change the IKE version based on requirement.
1) Regardig the throughput, if you take pcap on the PAN firewall, are you observing many re-trenasmission/fragmentation ...? That could lead towars the low throughput. Also, could you please choose low profile encription keys for the phase-2 negotiation i.e AES-128. This will reduce a small amount of encription/decryption overhead.
2) We need to take a look at the routing part. If you do a traceroute to a public IP i.e 4.2.2.2, where the packets are getting stuck...? ( Traceroute to an IP instead of domain-name will eleminate any issue with DNS )
Thanks
HULK
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-09-2016 04:13 AM
Hi,
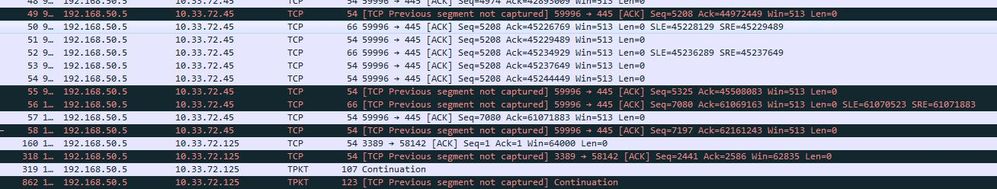
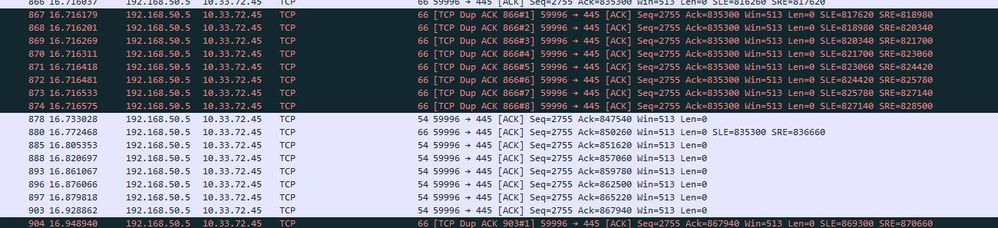
I see these lines in drop p.cap capture
A lot of TCP Previous segment not captured
In firewall pcap i see a lot of TCP Dup ACK
receive pcarp shows this:
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-16-2017 10:43 PM
Hi,
any news on the second Topic ? As have the same Problem. S2S Tunnel is established, forced tunneling is configured
on Azure side. A Server can reach local Subnets with no Problems but is not able to reach the Internet.
S2S Zone was taken into NAT, a Traceroute is stuck at the PA. Capturing Traffic fills the "Drop" Log.
Thanks for any Input !
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-20-2017 04:32 AM
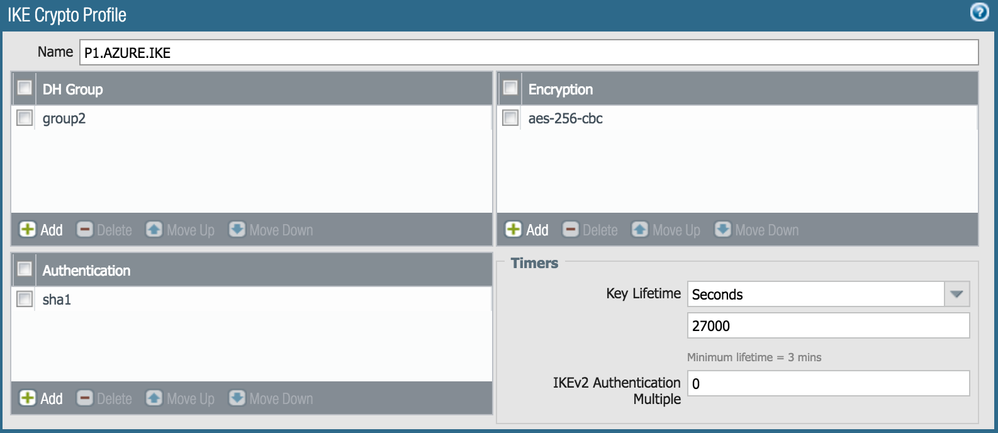
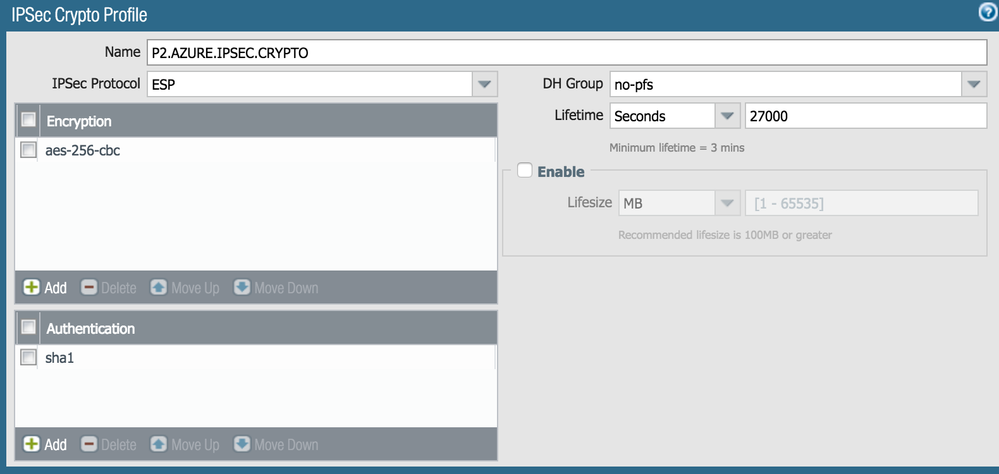
Use the following settings for Phase 1/2 and test
use IKEv2 only.
Had similiar issues and Microsoft Support advised to use the following settings after that the traffic flow was good.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-20-2017 10:27 PM
Thanks for sharing, unfortunately no change.
Capturing the Traffic (simple Ping to 8.8.4.4 from a Server in Azure), it passes the Firewall is NAT`ed, the Ping Reply hits the external IP of the Firewall and is then dropped.
Seems the Firewall does not know what to do with the Reply.
Any more hints ?
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-21-2017 12:23 AM - edited 08-21-2017 12:34 AM
Hi,
Can firewall ping the server? Can you try to capture 3-way handshake? Initiate any web request from the server to the web and check how Palo sees this session. Does it know how to get back to the server? If yes which interface it uses (tunnel or eth x/x?)
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-21-2017 02:02 AM
Hi,
yes the FW can ping the Server (through the Management Interface, which is on the trusted Zone).
All S2S Traffic from on premise to Azure works well, just forced tunneling from azure to the Internet is stuck.
Same as with ping. Capturing the Packets shows the reply doesn´t get back to the Server, so no Handshake is established.
In Traffic Log, the request "ages-out". In Session Browser all looks fine. The "Traverse Tunnel" Flag is set "true".
Maybe I didn´t understood you correctly, what do you mean by "how Palo sees this session" ?
- 9092 Views
- 7 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Log forwarding from Cloud NGFW in Azure to Log Analytics Workspace for Sentinel in VM-Series in the Public Cloud
- High Data Plane Utilization During Business Hours in Next-Generation Firewall Discussions
- Split tunnel is not working for Linux/IOS devices in General Topics
- FTP Evasion Detection (id:30401) in Next-Generation Firewall Discussions
- Help Needed: NAT & Security Policy Configuration for Azure LB → Palo Alto → DMZ Webserver (Public IP) in VM-Series in the Public Cloud