- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
VPN Site-to-Site Private IP and Public IP
- LIVEcommunity
- Discussions
- General Topics
- Re: VPN Site-to-Site Private IP and Public IP
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
VPN Site-to-Site Private IP and Public IP
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-04-2021 11:37 AM
VPN Site-to-Site Private IP and Public IP
Good afternoon everyone, is it possible to set up a Site-to-Site VPN between a site with a Palo Alto Private IP and a Palo Alto Public IP.
Site Privado: PaloAlto---IpWan-192.168.1.254---Router/Modem--------Internet-------Site Publico:IPWan:190.100.100.200
Thank you very much for your help and support, I remain attentive.
Best regards
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-04-2021 12:58 PM
Hello,
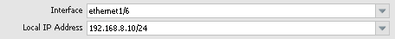
Yes it is! On the PAN with the private IP address make sure to give it a Local IP Address in the IKE Gateway setting.
Then on the other PAN point the IKE gateway at the public IP address however in the Ike Gateway, put in the Peer Address:
Hope that helps.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-04-2021 01:25 PM - edited 08-04-2021 02:16 PM
Good afternoon, thank you for your reply.
On the private IP side, I don't need to do any NAT or Port-Forwarding ?
That configuration would be enough ?
I remain attentive, thank you very much
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-07-2023 08:48 AM
Hello,
For your ISP router, dont have it filter anything. Leave it wide open and let the Palo Alto handle the traffic.
Just my thoughts.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-07-2023 08:49 AM
Hello @Metgatz
Apologies for the late response. For the VPN tunnel, no. If the traffic is going out the internet, then internal to external traffic will need attention.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-07-2023 05:03 PM
Hello @OtakarKlier thank you for your reply and collaboration.
I understand that it is feasible, I have not had to do it, but I understand that it is possible to do the following.
Scenario:
-Palo Alto Firewall Static Public IP directly connected to PA Interface.
-Firewall fortigate behind traditional Modem/Route/OTN almost domiciliary with Dynamica public IP but with private IP in
its WAN interface of the fortigate.
I.e.:
PaloAlto-Untrust-Interface-Static dedicated Public IP=======Internet=====VPN-Site-to-Site=============Dynamic-IP-traditional-Internet-Modem-ISP=====NAT===Private WAN IP Fortigate.
I can set up a Site to Site VPN tunnel between a Palo Alto FW with dedicated static public IP coming directly to the AP against a Fortigate firewall behind a traditional ISP modem/router/nat.
Is it feasible to realize this IPSEC tunnel, that is stable, operates correctly ?
What aspects, configurations, settings, etc. should I consider when making this configuration?
Thanks as always for the collaboration, good vibes and for all the advice and your time in answering.
Greetings and very attentive to your comments.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-13-2023 07:22 AM
Hello,
I not know the Fortigate devices well but on the Palo Alto you will setup the following:
Network > Network Profiles > IKE Gateways > General
- Peer IP Address = the public IP address on the other side (Fortigate side of hte ISP moden doing the NAT)
- Peer Identification = the Private NAT'ed IP of the Fortigate device.
Hope this helps.
Regards,
- 7982 Views
- 7 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Unable to establish tunnel during Service Connection configuration (Details Added with Screenshot) in Prisma Access Discussions
- VPN Gateway fails to authenticate clients with new certificate uploaded in General Topics
- NAT Translations Related to VPN Tunnels in Next-Generation Firewall Discussions
- Zscaler IPSec tunnel over Palo alto SD WAN in Advanced SD-WAN for NGFW Discussions
- Paloalto routing an IPSEC tunnel to another router in General Topics