- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Why does traffic log show Application for a rule that uses a Service?
- LIVEcommunity
- Discussions
- General Topics
- Re: Why does traffic log show Application for a rule that uses a Service?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2017 11:48 AM
Hello folks,
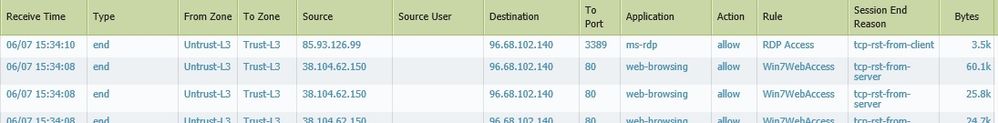
I am doing some testing (studying) on using Applications vs Services and have a question about the traffic log.
Why does the traffic log identify the traffic and rule to an Application when the rules are setup as Service?
My rules are setup as Service.
Traffic log identifies them as Applications.
Is it because Applications are set to any?
I assuming that even though the Traffic log identifies an application, the traffic is not inspected as so (Layer 7)?
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2017 12:47 PM
Layer 7 inspection happens on all sessions to a degree. An exception would be if you created an application override policy that would prevent it.
Your rules are port-based, but App-ID is still functioning. The application won't be taken into account when processing the rules, and with your profiles set to none it will not be doing any threat scanning on the traffic hitting those rules, but App-ID is still active.
Regards,
Greg
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2017 12:47 PM
Layer 7 inspection happens on all sessions to a degree. An exception would be if you created an application override policy that would prevent it.
Your rules are port-based, but App-ID is still functioning. The application won't be taken into account when processing the rules, and with your profiles set to none it will not be doing any threat scanning on the traffic hitting those rules, but App-ID is still active.
Regards,
Greg
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2017 12:56 PM - edited 06-07-2017 12:59 PM
Palo does APP-ID and it based on the traffic which is passing through. If you specify app as "any" and the services as http or RDP in the security policy, palo will scan all traffic that is matching this policy. Based on the allowed port (services) it will identify application using app-id future (based on signature, port number etc). So Palo always does L7 inspection unless you do app-override, then it is only up to L4 (TCP/UDP port numbers).
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2017 12:57 PM - edited 06-07-2017 01:05 PM
@gwesson took me a bit longer to finish my post 😉
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2017 01:13 PM
@TranceforLife Every once in a while I can be a post ninja, but you usually beat me 🙂
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2017 01:21 PM
Recently spending too much time next to the pc. Not good 😞
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2017 02:11 PM - edited 06-07-2017 02:14 PM
Thank guys!
So what if the traffic does not match an application in the database (when set to any)?
Does it just take the service port route and then skip Layer 7 inspection and stay at Layer 4?
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2017 03:17 PM
Nope, every initial packet will get Layer 7 inspection. It makes sense if you know the flow - if it has enough information to know it doesn't match any app, then it's already done the L7 inspection.
If no app is matched, you'll see the app listed as "unknown-tcp" or "unknown-udp" depending on the underlying protocol. That is fairly rare though, as the app-id database is pretty expansive.
- 1 accepted solution
- 3234 Views
- 8 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Microsoft Defender Outbound traffic policy in Next-Generation Firewall Discussions
- Global Protect for IPad auto-connect option partially works in General Topics
- NAT mapping public to private IP in General Topics
- Panorama REST API policy creation error with ' 'message': 'Invalid Body', in Panorama Discussions
- Not able to login into URL from behind the palo alto in Next-Generation Firewall Discussions