- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Why I see no logs for DoS policies
- LIVEcommunity
- Discussions
- General Topics
- Re: Why I see no logs for DoS policies
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-25-2021 08:19 AM
I am testing DoS policies and have alarm rate set as 1. I did not intend to be that low but I was not seeing logs under monitor for a server that is continuously used. There are flood logs from Zone Protection and they use a different log forwarding profile for easy differentiation.
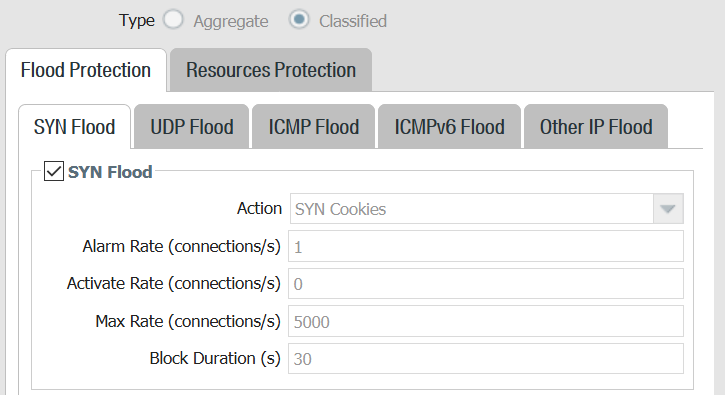
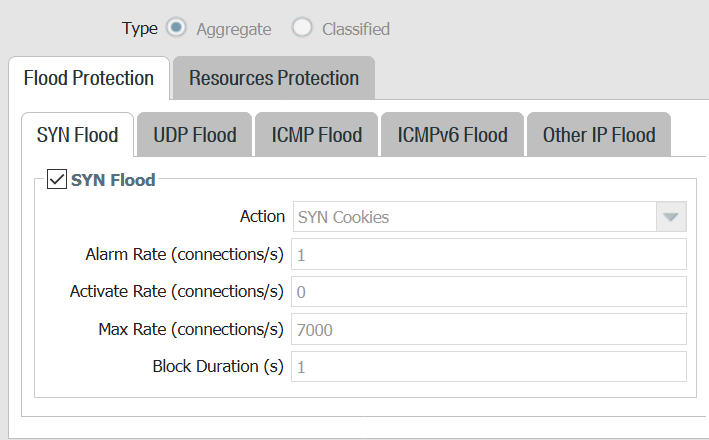
DOS policy
Aggregate and classified profiles used in policy
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-22-2021 11:14 AM
Both Zone Protection and DoS policies cannot have TCP-SYN enabled at the same time, Resolved while troubleshooting with support.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-25-2021 11:11 AM
Here is some information that may help..
Global Counters for DoS Activity Monitoring
To supplement the Threat event logs for Zone and DoS protection, the following CLI commands can provide additional
information in the form of global counters and session count information to help identify DoS activity.
>show counter global name ? Lists all global counters
>show counter global filter aspect dos List all global counters with active DoS aspect values
Counter Aspects
PAN-OS allows filtering of the Global Counters by category, aspect, and severity to make it easy to pull the relevant
counters for review. Counters of interest that are related to Zone and DoS protection include:
Category: Flow Aspect: dos
Category: Flow Aspect: parse
Category: Flow Aspect: ipfrag
Example of CLI command to extract Flow counters with a DoS aspect:
>show counter global filter category flow aspect dos
Stay Secure,
Joe
Don't forget to Like items if a post is helpful to you!
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-25-2021 11:54 AM
@jdelio I checked and as you can see below on setting the filter to that IP i can see Syn cookies are sent. But why does it not show in logs is my problem. I know its not much but its still higher than alarm rate of 1 and should show in threat logs as cookie sent.
---------------------------------------------
debug dataplane packet-diag set filter match destination X.X.X.X
debug dataplane packet-diag set filter on
---------------------------------------------
show counter global filter delta yes packet-filter yes aspect dos
Global counters:
Elapsed time since last sampling: 7.374 seconds
name value rate severity category aspect description
--------------------------------------------------------------------------------
flow_dos_syncookie_cookie_sent 16 1 info flow dos TCP SYN cookies: cookies sent, aggregate profile/zone
flow_dos_syncookie_ack_rcv 25 1 info flow dos TCP SYN cookies: ACKs to cookies received, aggregate profile/zone
flow_dos_cl_syncookie_ack_rcv 4 0 info flow dos TCP SYN cookies: ACKs to cookies received, classified profile
flow_dos_rule_allow_under_rate 78 6 info flow dos Packets allowed: Rate within thresholds of DoS policy
flow_dos_rule_match 78 6 info flow dos Packets matched DoS policy
flow_dos_ag_curr_sess_add_incr 12 0 info flow dos Incremented aggregate current session count on session create
flow_dos_cl_curr_sess_add_incr 12 0 info flow dos Incremented classified current session count on session create
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-22-2021 11:14 AM
Both Zone Protection and DoS policies cannot have TCP-SYN enabled at the same time, Resolved while troubleshooting with support.
- 1 accepted solution
- 6362 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Windows-Remote-Management & Implicit Use of Web-Browsing in General Topics
- Problem with downloading PAN OS in General Topics
- Security Policy with Destination Criteria in Strata Cloud Manager
- User-ID mapping log is empty in General Topics
- NGFW admin account is locked. What should I do? in Next-Generation Firewall Discussions