- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Wildcard certificate on PA firewalls
- LIVEcommunity
- Discussions
- General Topics
- Re: Wildcard certificate on PA firewalls
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-30-2018 03:51 PM
Hi Team,
I'm trying to create a CSR in Panorama in order to get a wildcard certificate from our third party CA.
In order platforms, I define as common name the format *.mydomain.com but in Palo Alto I'm getting an error: Failed to generate certificate and key.
When I change the common name to .mydomain.com it allows me to create the CSR.
I just wanted to touch base with you guys in order to know about your experience working with wildcards on Palo Alto Plattform.
Any response will be very appreciated.
Thank you,
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-30-2018 06:28 PM
It would help to know Panorama version as @Remo mentioned.
In my case Panorama 8.1.4
Works like a charm.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-30-2018 05:12 PM
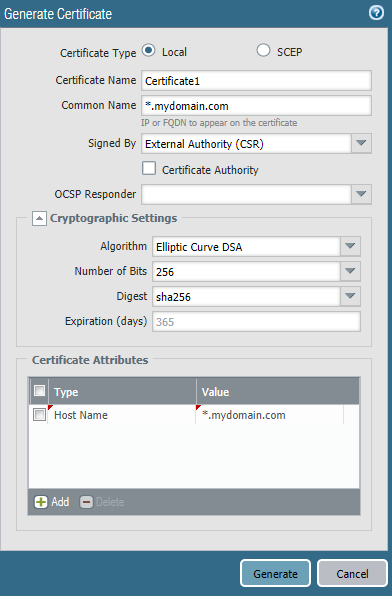
Are you choosing Signed by External Authority (CSR)?
Try to change Certificate Name to something else but leave Common Name to *.mydomain.com
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-30-2018 05:33 PM
Yup, just tested it as described by @Raido_Rattameister and it successfully generated a CSR for a wildcard cert.
(Remember to add *.mydomaim.com also as "hostname" when you generate the CSR)
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-30-2018 05:35 PM
Thanks for your feedback Raido,
Yes Sir, I'm choosing Signed by External Authority (CSR) and I'm still getting the same error. The error clears out when I change the Common name to .mydomain.com (removing the *).
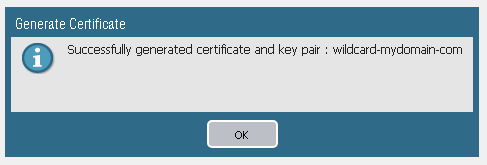
For the Certificate Name I'm adding wildcard-mydomain-com.
Other thing I forgot to mention was that I'm choosing Algorithm Elliptic Curve DSA.
Thanks,
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-30-2018 05:39 PM
Thanks vsys,
I just tested that and got error: "request -> certificate -> generate -> hostname '*.mydomain.com' is invalid"
Could you test it for an Elliptic Curve DSA cert?
Thanks,
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-30-2018 05:56 PM
What PAN-OS version do you have installed and are you logged in with a user that has "superuser" privileges?
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-30-2018 06:28 PM
It would help to know Panorama version as @Remo mentioned.
In my case Panorama 8.1.4
Works like a charm.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-31-2018 12:13 AM
Works fine on PAN OS 7.1.16 too. Defined *.mydomain.com in both CN and hostname feilds with superuser account and it was generated successfully. So was the commit too.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-31-2018 04:52 AM
I was asking about the version and the permissions because may be you are seeing this bug (which is fixes in PAN-OS 8.0.10):
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-31-2018 06:13 AM
Thanks for your feedback Team,
Our Panorama is already in 8.0.10 and yes, my account is a superuser. I guess it's time to escalate to PA Support, I just don't want to purchase a useless wildcard certificate.
Kind Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-31-2018 06:56 AM
Yes, looks like there is something wrong. (Did you try the generation with another browser?, if you're using windows - as bad as this sounds - try it once with IE)
And while you talk about this with PA support ... you could simply use tools like openssl to generate the key and CSR for you.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-31-2018 07:24 AM
Thanks for the recommendation vsys,
I just tried with IE and got the same error, OpenSSL will work fine for sure.
Kind Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-02-2018 12:20 PM
Hi Team,
Thank you very much everyone for your support, I left the Common Name as .mydomain.com and then on the CA directly you can indicate this is a wildcard certificate and they will prepend the * for you so the final result will be *.mydomain.com.
Then when I imported the signed certificate it was successful.
Kind Regards!
- 1 accepted solution
- 9927 Views
- 12 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Setup > Management > Cortex Data Lake > Cortex Data Lake Status > Show Status in AIOps for NGFW Discussions
- Firewall and Panorama mangement certificate expire in Panorama Discussions
- Firewall fails to register to Wildfire appliance in Next-Generation Firewall Discussions
- Subnetting question for a wildcard that covers a bunch of slash 25s in General Topics
- Panorama and Paloalto Firewall Communication in Panorama Discussions