- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Wildfire new threat signature update
- LIVEcommunity
- Discussions
- General Topics
- Re: Wildfire new threat signature update
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-26-2018 08:30 AM
As per Admin guide
The Palo Alto Networks WildFire system also provides signatures for persistent threats that are more evasive and have not yet been discovered by other antivirus solutions. As threats are discovered by WildFire, signatures are quickly created and then integrated into the standard Antivirus signatures that can be downloaded by Threat Prevention subscribers on a daily basis (sub-hourly for WildFire subscribers
Does it mean that WF if does not know any Antivirus signature it quickly creates it and when we have 5 mins update with
WF cloud that new signature comes and becomes part of antivirus profile only.
Need to know when new signature comes from WF it is only for the Antivirus profile?
Help the community: Like helpful comments and mark solutions.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-26-2018 10:47 AM
Hi Mike,
If WildFire analyses a file that it has never seen before - if the verdict is deemed as malicious it will create a signature that can be made available to people with a WildFire license within 5 minutes. Otherwise if you don't have a WildFire license, it will be made available within 24/48 hours via a threat content update - provided you have a threat prevention license.
WildFire signatures are enforced via the "WildFire Action" in an antivirus security profile, yes - but as well as the DNS signatures enforced via an antispyware security profile.
https://www.paloaltonetworks.com/documentation/81/pan-os/pan-os/threat-prevention/threat-signatures
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-26-2018 11:12 AM
Firewall will create hash of file and send it to WF to check if this file has been checked before.
If it has then based on verdict file is permitted through or blocked.
If it has not been checked then file is passed through and copy is sent to WF to be analyzed.
Verdict will come back in 5 mins or less.
Those who don't have WF subscription can upload only PE files to WF (exe, dll etc) and they get rest of WF signatures with next Antivirus and Antispyware update.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-26-2018 10:47 AM
Hi Mike,
If WildFire analyses a file that it has never seen before - if the verdict is deemed as malicious it will create a signature that can be made available to people with a WildFire license within 5 minutes. Otherwise if you don't have a WildFire license, it will be made available within 24/48 hours via a threat content update - provided you have a threat prevention license.
WildFire signatures are enforced via the "WildFire Action" in an antivirus security profile, yes - but as well as the DNS signatures enforced via an antispyware security profile.
https://www.paloaltonetworks.com/documentation/81/pan-os/pan-os/threat-prevention/threat-signatures
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-26-2018 11:12 AM
Firewall will create hash of file and send it to WF to check if this file has been checked before.
If it has then based on verdict file is permitted through or blocked.
If it has not been checked then file is passed through and copy is sent to WF to be analyzed.
Verdict will come back in 5 mins or less.
Those who don't have WF subscription can upload only PE files to WF (exe, dll etc) and they get rest of WF signatures with next Antivirus and Antispyware update.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-26-2018 02:07 PM
Sorry for being a smart aleck 😛
@Raido_Rattameister wrote:Firewall will create hash of file and send it to WF to check if this file has been checked before.
If it has then based on verdict file is permitted through or blocked.
The firewall does not allow/block based on a WF verdict, only Traps does. The firewall only blocks based on WF signatures of malware-verdict-files which it receives all few minutes. The hash check is only done to check if the file is unknown and needs to be uploaded to WF.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-26-2018 02:20 PM
Traps has capability to hold back execution of unknown file until verdict comes back from WF.
Firewall will pass unknown files through but those that have been already checked by WF and verdict was malicious are blocked.
This check is done based on file hash.
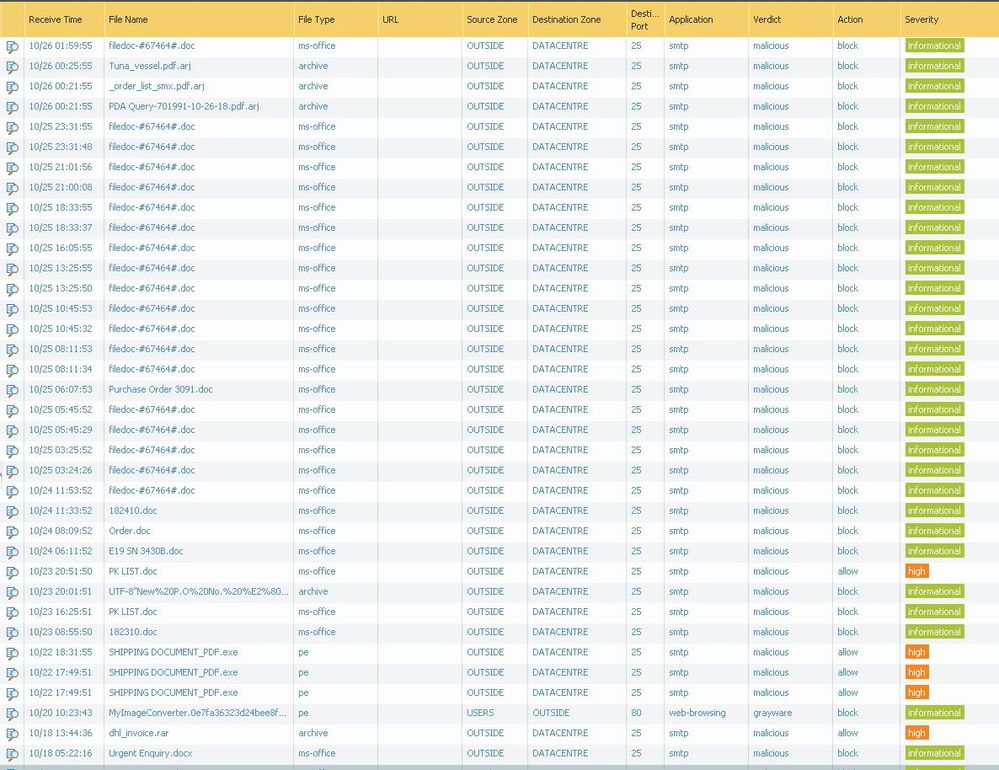
Check Action column on the screenshot.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-26-2018 02:47 PM
In the wildfire log the action is only based on the fact if there is already a WF signature. So for every WF log entry with action block you also have a threat log entry either as virus or wildfire-virus. Thats also the reason why (also in your screenshot) you have malicious files with action allow. These with action allow are the ones where so far isn't a WF signature available.
Another reason why a signature is required is because paloalto firewalls are still stream based, they block the file already when the signature matches a part of the file, at that point the file doesn't have to be fully transfered.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-10-2022 01:28 AM
HI Luke!
Which functionality is available to firewall users with an active Threat Prevention subscription, but no
WildFire license? Access to the WildFire API or PE file upload to WildFire?
Thanks
- 2 accepted solutions
- 6388 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Threat Protection Coverage for LockBit 5.0 in General Topics
- High Data Plane Utilization During Business Hours in Next-Generation Firewall Discussions
- Newsletter: Cloud Delivered Security Services, Oct-2025 in Advanced Threat Prevention Discussions
- Newsletter: Cloud Delivered Security Services, Aug-Sep, 2025 in Advanced WildFire Discussions
- Cortex XDR blocks MalwareBytes in Cortex XDR Discussions