- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
www server in DMZ - what aplication should me allowed?
- LIVEcommunity
- Discussions
- General Topics
- www server in DMZ - what aplication should me allowed?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
www server in DMZ - what aplication should me allowed?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-25-2014 01:52 AM
Hi
My www server is in DMZ, I have strict security policy that allow:
- web-browsing
- web-crawler
- ssl
- rss
- flash
I have application -default as a service.
Is it enought for indexing services like Google and any other?
Regards
SLawek
- Labels:
-
Configuration
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-25-2014 09:34 AM
Hello slv,
Looks like there is a server installed in dmz and you would like to know what apps or services should be allowed.
1 Based on what services the server offers accordingly the services and apps have to be configured to have access for the services from the server.
2 You can initially have apps "any" and services "any" if you want to know what kind of traffic is being requested. By this we can know what services and apps are being identified to be opened up appropriately.
3 Also with the existing setup you have certain apps and its default ports opened up. If you are seeing any drops in the traffic logs trying to reach the server then if that connections are legit then you know what more has to be opened up.
If we go to applipedia or the applications page on the firewall there are a lot of applications pertaining to google and it is best to search here to add the required apps to allow the required traffic.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-25-2014 09:52 AM
Hi
That all I know, I expected answer from real configuration and community users experience.
Could someone share it?
With regards
Slawek
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-25-2014 11:25 AM
Hi,
Think there is no similar config for google and other, demand what you put in other, depend content on your server, depend on many things.
Best thing should be to change your policy with app any, service http, audit the flow for couple of minutes and based on logs, create an accurate policy.
Hope help
V.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-26-2014 07:09 AM
Never use apps alone for inbound connections to your DMZ Server, always use service ports for that. If you use apps only you will open a big hole in your firewall.
Maybe I misunderstood your question and your talking outbound from your DMZ Server.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-26-2014 09:29 AM
Hi Gafrol
Could You explain me why I should use service ports insted of aplications. For me it's strange, ie: on port 80 we have more than 2000 aplications.
I'm using aplication because I prefer to protect my servers (by thread prevention) also PAN check traffic for inproper transmission.
Do I'm wrong?
Regards
Slawek
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-27-2014 03:15 AM
Hi
As you sugested I changed settings in policy, now it's any/any as an aplication and services. Report made from yesterdays logs says:
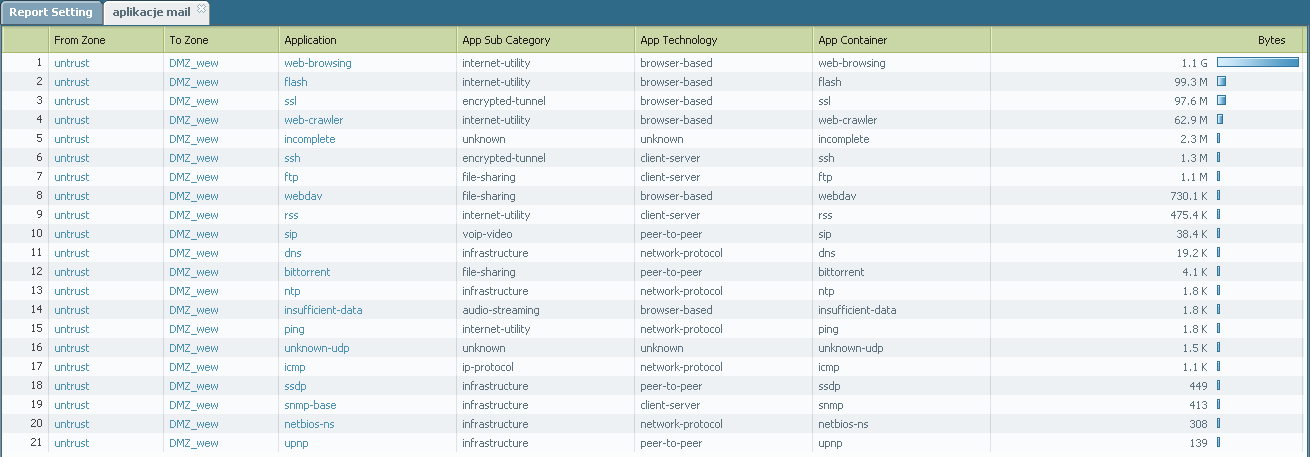
As You can see there is a lot of unwanted aplications, I'd like to let them working:
- web-browsing
- flash
- ssl
- web-crawler
- ssh
- ftp
- ping
Rest of applications are unwanted for me.
How I should reconfigure my security policy?
Should I put this applicatios into apps and create my own services:
web-browsing (tcp/80, tcp/443)
webdav (tcp/443, tcp/80)
ssh (tcp/22)
ftp (tcp/21, what about data stream?)
ping (icmp)
and put them into services?
Help me please to properly configure my device
With Regards
Slawek
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-27-2014 03:22 AM
I have another question for You - related to this problem. In dayly report I got:
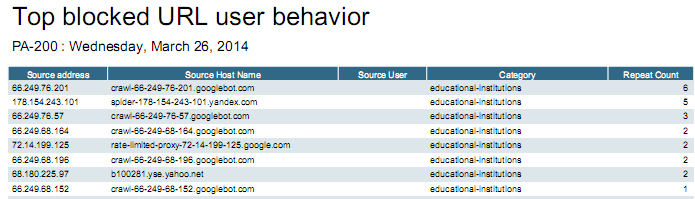
Why they are blocked? I'm not using URL filtering in this security policy.
How to troubleshoot it?
Regards
Slawek
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-27-2014 05:27 AM
In the service column of the rule instead of using service "any" change it to "application-default". That should help.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-27-2014 06:45 AM
Are You sure?
It's impossible to commit with aplication=any service=app-default.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-27-2014 06:54 AM
Hello Slawek,
As you have mentioned your requirements is :
--------------------
web-browsing (tcp/80, tcp/443)
webdav (tcp/443, tcp/80)
ssh (tcp/22)
ftp (tcp/21, what about data stream?)
ping (icmp)
--------------------
It's seems all applications are working on their default port. Hence, you can apply above mentioned applications in a security policy, set service as application-default and allow them ( please include SSL for TCP/443, as web-browsing will only allow TCP/80).
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-27-2014 07:12 AM
I'm not sure that I understud You clearly.
Is my policy should be like:
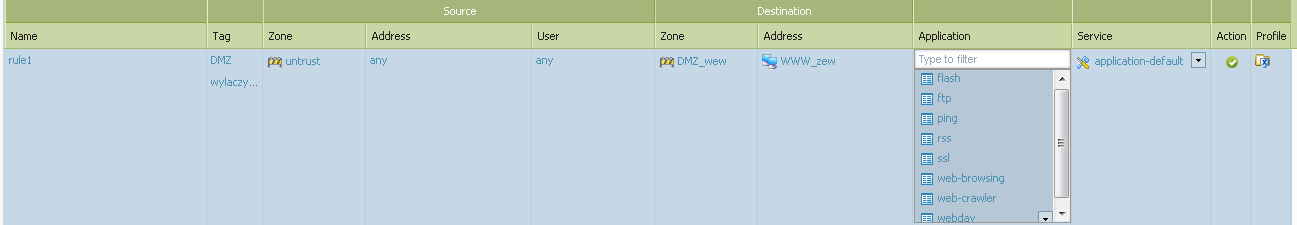
This is that what I alredy had.
What about "TOP blocked user bahavior"?
With Regards
Slawek
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-27-2014 07:21 AM
Hello Slawek,
Yes, your policy configuration is looking good here. Could you please let me know, how did you generate that "TOP blocked user bahavior" report...?
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-27-2014 11:17 AM
On my PA200 it is one of predefined reports:
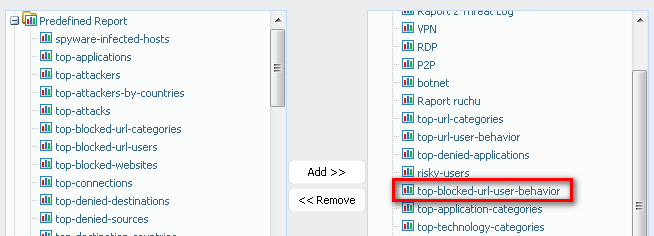
- 5416 Views
- 14 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Need clarification on URL Filtering logs in Next-Generation Firewall Discussions
- Allow traffic mikrotik site to site. in General Topics
- EWS O365 Instance - Not allowed to access Non IPM folder. (85) in Cortex XSOAR Discussions
- Custom URL to match allow policy matches halfway through URL in Next-Generation Firewall Discussions
- SIP TRunk over PA6-440 not working in Next-Generation Firewall Discussions



