- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Deploying VM-Series on ESXi in Layer 3 Mode
- LIVEcommunity
- Products
- Network Security
- GlobalProtect
- GlobalProtect Articles
- Deploying VM-Series on ESXi in Layer 3 Mode
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
on 06-05-2020 07:12 PM - edited on 06-05-2020 08:17 PM by Retired Member
Palo Alto Networks shares key details about deploying VM-Series Next-Generation Firewall on the ESXi in Layer 3 Mode. Learn more about the requirements, Creating the Network Topology, VM-Series Layer 3 Configuration, and more.
Deploying the VM-Series on ESXi in Layer 3 Mode
All virtual machines on the ESXi hosts will be segregated from each other on the network by the VM-Series next-generation firewall by IP addressing and Layer 3 gateways. The basis for this design is to provide maximum resiliency with regards to VM-Series HA placement, guest VM protection, and the inherent networking capabilities of the ESXi hypervisor and virtual switching. This technote will cover a multiple ESXi host environment showcasing east/west traffic separation to demonstrate the Layer 3 capabilities of the VM-Series next-generation firewall.
Topology
A highly available Active/Passive pair of VM-Series next-generation firewalls are positioned between the physical datacenter network and Guest VM workloads. A single Distributed vSwitch will be used in this example topology. Port Groups are used to segregate traffic between the untrusted side and the trusted side of the firewall. Layer 3 interfaces will be used to provide untrust/trust boundaries on the firewall as well as provide for default IP gateway reachability for the entire subnet.

Requirements
This design was validated with ESXi version 6.7u3, vCenter version 6.7, VM-Series PAN-OS version 9.1.2.
Creating the Network Topology
We often make virtual networking more complicated than it needs to be. ESXi virtual switches work on similar principles as physical network switches. Don’t overcomplicate it. The same principles that you would use to deploy our firewall in a physical Layer 2/3 networking environment is the same methodology that you would use to deploy the VM-Series in a virtualized environment.
Building the ESXi network topology is a crucial part of any Layer 3 design. Distributed vSwitches by themselves do not necessarily segregate traffic between port groups. The default configuration of a vSwitch, the initial port group configuration, and the vSwitch uplinks create a flat Layer 2 network.
There is a misconception about what port groups are. Port groups are simply a collection of virtual ports that share a common configuration set. A port group is not a VLAN. There are many attributes that can be configured under a port group and the VLAN ID is one of those attributes.
This design calls for only a couple of port groups to be configured on the vSwitch.
- A single vSwitch was created - tswitch1
- 2 port groups for the firewall and VM guests
- untrust (connected to IP Gateway)
- trust (for L3 guest: Ubuntu Web & App)
- uplink ports, tswitch1-DVUplinks, connect this vSwitch to the physical network switches
Uplink ports: tswitch1_vDS uplinks
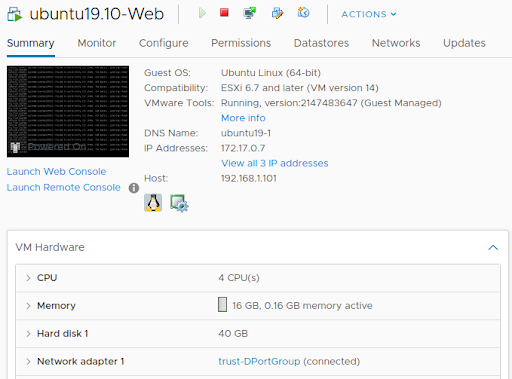
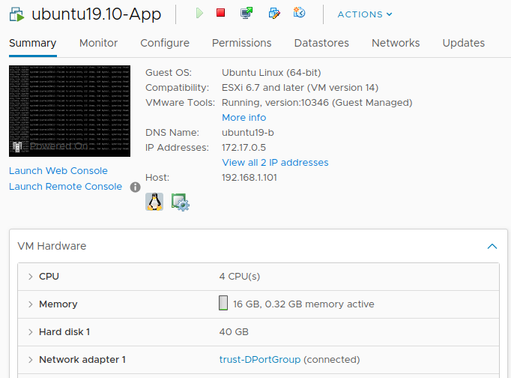
The following image shows the two (distributed) port groups assigned to the VM-Series:
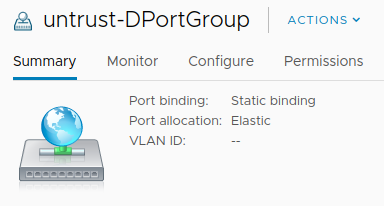
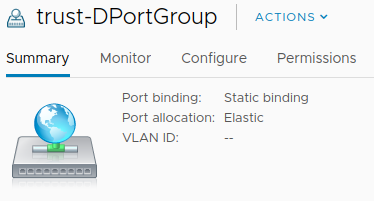
Assign Port Groups to VM-Series
VM-Series Firewalls are assigned to the firewall port groups. Network Adapter 1 is used for the firewall’s management interface. Network Adapter 2 is used for the untrusted side of the firewall. Network Adapter 3 is used for the trusted side of the firewall.
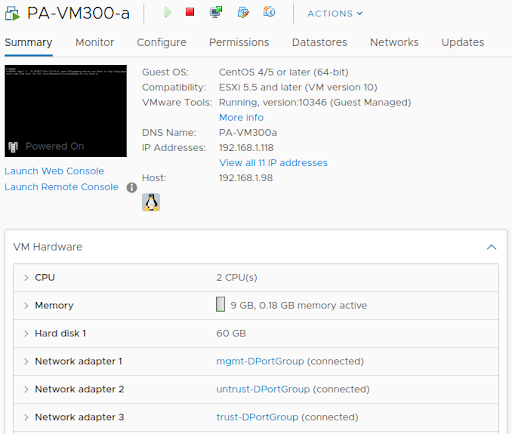
The guest machines are assigned to their respective port-groups.
VM-Series Layer 3 Configuration
This section covers the VM-Series next-generation firewall network configuration. All configuration is completed in the PAN-OS web interface.
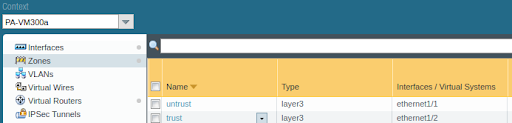
Zones
Two zones were used in this example:
Virtual-Routers
For this technote, two virtual routers were employed: both the default virtual router (VR) and a separately configured VR representing an internal trusted network boundary. A VR is a function of the firewall that participates in Layer 3 routing.
The firewall uses virtual routers to obtain routes to other subnets by either manually defining static routes or through participation in one or more Layer 3 routing protocols (dynamic routes). The routes that the firewall obtains through these methods populate the IP routing information base (RIB) on the firewall. When a packet is destined for a different subnet than the one it arrived on, the virtual router obtains the best route from the RIB, places it in the forwarding information base (FIB), and forwards the packet to the next hop router defined in the FIB.
In addition to routing to other network devices, virtual routers can route to other virtual routers within the same firewall if a next hop is specified to point to another virtual router as illustrated below.
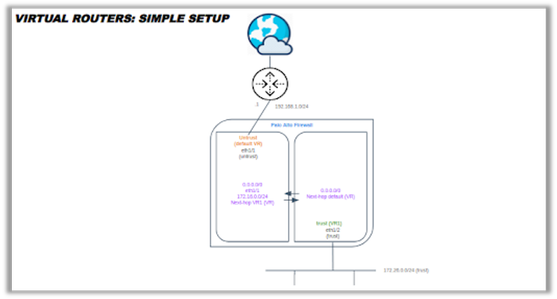
In a Layer 3 deployment, the firewall routes traffic between multiple ports. This deployment requires that you assign an IP address to each interface and configure Virtual Routers to rout the traffic. Choose this option when routing is required.

Default virtual router static routes (NOTE: next-vr next-hop) :😞
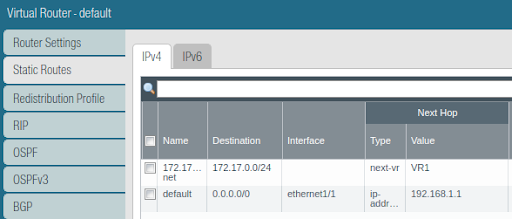
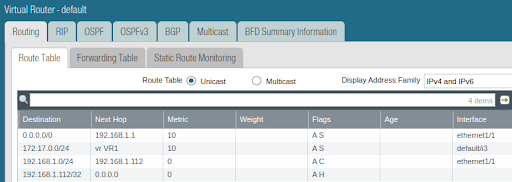
Default virtual router static route table (NOTE: next-vr next-hop) :
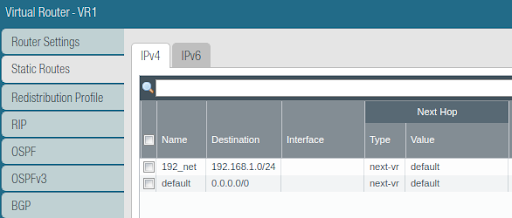
Virtual Router 1:
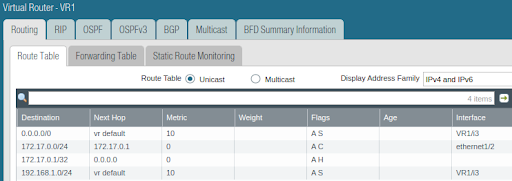
VR1 static route table:
Interfaces
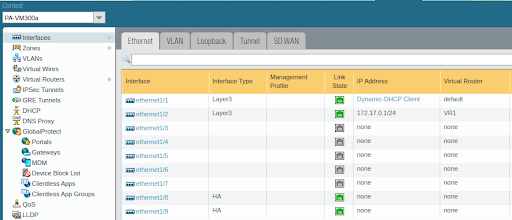
Interfaces will need to be configured under the Interfaces > Ethernet tab. Assign the Interface Type of the physical interface as Layer 3. Nothing else needs to be configured under the physical interface. Interfaces can be provisioned with either DHCP client or static IP addressing.
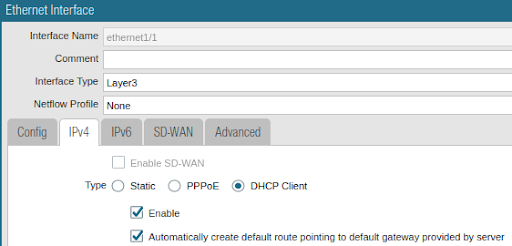
DHCP Layer 3 interface configuration:
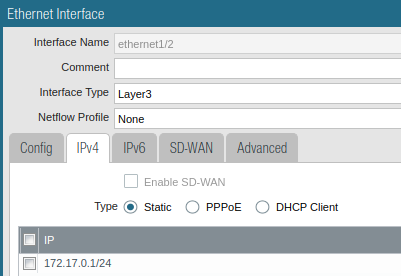
Static Layer 3 interface configuration:
Assign the interface to the correct zone untrust/trust.
Untrust and trust zone interface configuration:
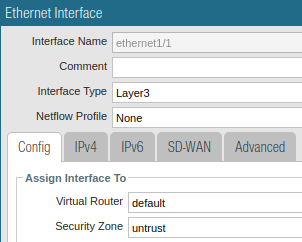 Ethernet1/1 untrust zone assignment illustration Ethernet1/1 untrust zone assignment illustration |
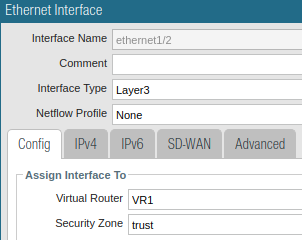 Ethernet1/2 trust zone assignment Ethernet1/2 trust zone assignment |
Policy
Add a policy to allow packets to traverse the VM-Series next-generation firewall.
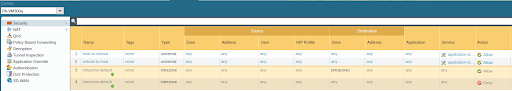
Commit the Configuration
Commit the configuration.
Verifying the Environment
Working with a Layer 3 environment requires investigating the guest VM’s connectivity by testing IP reachability to internal and external Internet hosts. The guest VM IP address information is listed below.
- Ubuntu 19.10 Web VM: 172.17.0.724
- Ubuntu 19.10 App VM: 172.17.0.5/24
VM-series Commands
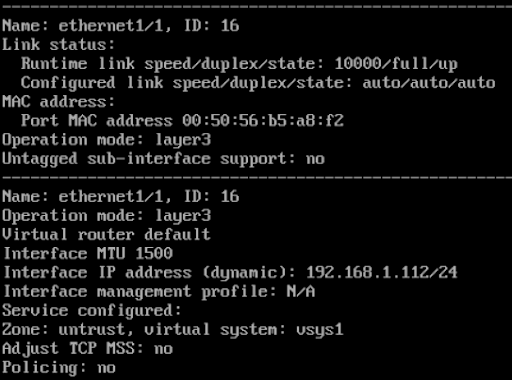
The CLI can be used to view MAC/IP address information on the VM-Series. The command is:
show interface ethernet 1/<interface #>
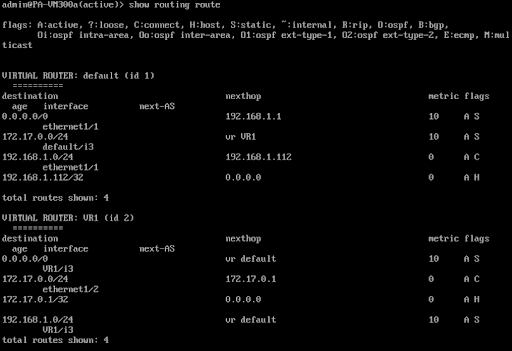
For the VM-Series routing table, the command is:
show routing route
Physical Network Commands
The command you are going to use to verify any MAC/IP address learning will differ based on your network switch vendor. This lab utilizes Juniper Networks EX Series Switches:
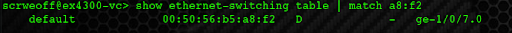
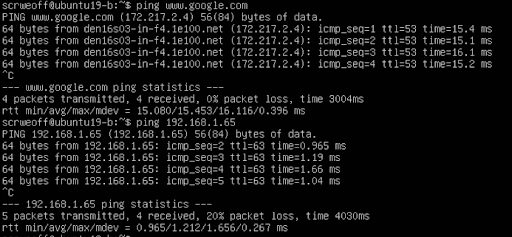
Guest VM Commands
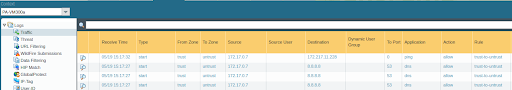
Firewall Traffic Log
You can view the firewall traffic log by navigating to Monitor Tab > Logs > Traffic.

Additional Information
Virtual Routers Technical Documentation
Configure Layer 3 Interfaces Technical Documentation
Video Tutorial: How To Configure a Layer 3 Interface
- 8829 Views
- 0 comments
- 1 Likes