- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Global Protect and User-ID
- LIVEcommunity
- Discussions
- Network Security
- GlobalProtect Discussions
- Global Protect and User-ID
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-11-2021 06:42 AM
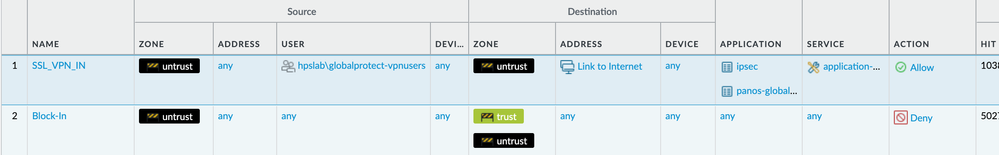
I want to make my GP portal more secure by adding User-ID to my GP inbound rule so that only users in the AD group can authenticate.
At the moment source user is just set to 'any' and the VPN is working fine.
When I add the group as in the attached image it breaks. I'm guessing there are some extra configuration steps i'm missing here...
Note that the group mapping is working fine in other rules once users are authenticated. I'm just wondering if I can utilise user-id at the first step in the authentication process.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-11-2021 07:29 AM
Ya by default this wouldn't work. The problem is that your firewall doesn't know who the user is when a user is attempting to connect from untrust to your GlobalProtect portal/gateway. So the SSL_VPN_IN is never going to be matched and you'll always hit the Block-In entry. For this to work, you would need to tie it with an authentication rulebase entry to feed unidentified users attempting to access GlobalProtect and have them login so that they actually have a user-id mapping on their public IP so they match your SSL_VPN_IN entry.
I honestly don't recommend you try do anything like this. Let your GlobalProtect Portal do it's job of authenticating the users. If you want to secure it as much as possible, restrict access to regions that you expect/allow users to work from and setup an automatic block for the source address after X number of GlobalProtect authentication failures.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-11-2021 07:29 AM
Ya by default this wouldn't work. The problem is that your firewall doesn't know who the user is when a user is attempting to connect from untrust to your GlobalProtect portal/gateway. So the SSL_VPN_IN is never going to be matched and you'll always hit the Block-In entry. For this to work, you would need to tie it with an authentication rulebase entry to feed unidentified users attempting to access GlobalProtect and have them login so that they actually have a user-id mapping on their public IP so they match your SSL_VPN_IN entry.
I honestly don't recommend you try do anything like this. Let your GlobalProtect Portal do it's job of authenticating the users. If you want to secure it as much as possible, restrict access to regions that you expect/allow users to work from and setup an automatic block for the source address after X number of GlobalProtect authentication failures.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-11-2021 09:03 AM
Yeah that makes sense.
Do you have any more information about how to set the number of authentication failures before lockout on the portal?
Thanks,
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-12-2021 07:12 AM - edited 05-12-2021 07:18 AM
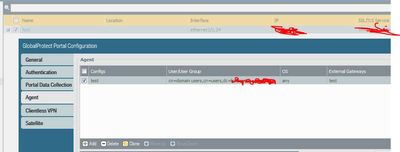
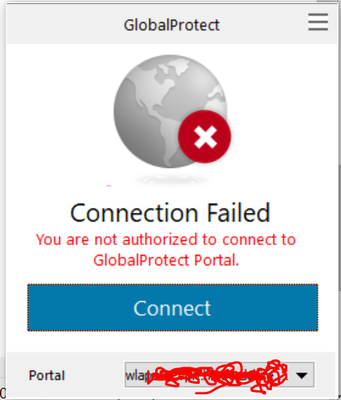
As an alternative you can use the portal agent to only allow selected users to connect,
if you are not in the AD group you will get this message,,
- 1 accepted solution
- 3543 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Global Protect users are unable to access SQL database which hosted in Azure in GlobalProtect Discussions
- Global protect intermittency in GlobalProtect Discussions
- Associate user credentials with a given portal in GlobalProtect Discussions
- Global Protect App for Surface Pro 9 - Chip SQ3 in GlobalProtect Discussions
- I cannot select user account to login with GlobalProtect App for Windows in GlobalProtect Discussions