- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Global Protect Pre-Logon followed by SAML SSO
- LIVEcommunity
- Discussions
- Network Security
- GlobalProtect Discussions
- Global Protect Pre-Logon followed by SAML SSO
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Global Protect Pre-Logon followed by SAML SSO
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-07-2020 11:30 PM
Hi Guys,
I have implemented global protect with pre-logon (device certificate) followed by user logon using SAML (Azure AD as SAML IDP)
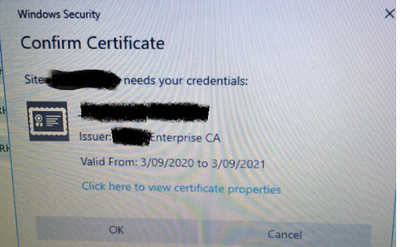
When global protect client initiate the user authentication below windows security pop up asking to confirm the certificate.
After confirming the certificate it connects fine and every time user reboot same pop up box comes up, if I replace the SAML auth with LDAP auth, I don't get any pops for certificate and everything works fine.
I have client certificate profile (internal Root and Intermediate CA) attached to client profile in each scenario ( LDAP auth vs SAML)
Also note that pre-logon works fine on each scenario and I can see before login to the machine globalprotect shows connected.
Has anyone come across this or similar issue?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-08-2020 02:17 PM
I'm not sure if this applies in your case, but I saw something similar when a user had two client certificates which matched the certificate profile. We solved it by deleting one of the unneeded certificates.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-15-2020 09:46 PM - edited 09-15-2020 09:55 PM
I have seen this similar behaviour in our setup.
We also have GP pre logon with machine cert and then SAML Azure authentication.
That cert pop message is for the certificate to sign SAML messages to IDP and we select that in Authentication profile.
Regards
Help the community: Like helpful comments and mark solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-15-2020 10:02 PM
@MP18 Is there any workaround to fix it? This is not convenient for users
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-17-2020 07:15 PM
Do you have more than 1 certs issued by your Intermediate Certs.?
either way you need to have SSL/TLS profile cert trusted by either your Internal PKI or external certificate authority.
It needs same CA cert signed by the above one which your PC also trusts.
Regards
Help the community: Like helpful comments and mark solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-24-2020 09:34 AM
To stop the client certificate pop-up you need to make sure the VPN url is either in your local intranet zone or in your trusted sites with IE Options configured "don't prompt for client certificate selection when no certificates or only one certificate exists " which needs to be set to enable
For Chrome and Edge the policy AutoSelectCertificateForUrls
Microsoft Edge Browser Policy Documentation | Microsoft Docs
Chrome Enterprise Policy List & Management | Documentation (google.com)
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-04-2021 02:12 PM
Also you can push this registry setting with GP agent then cert pop up will not occur.
Check this link
Certificate Selection by OID (paloaltonetworks.com)
Regards
Help the community: Like helpful comments and mark solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-19-2022 07:35 AM
Did you ever resolve this? Have messed around with different certificates but still getting the scenario you described. If you did solve it, any pointers would be useful.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-04-2024 09:25 AM
One additional thing to add here is a clarifying question and some details about how to work around one of the scenarios:
-Are you looking to use user certificates in any way/shape form?
If not, one thing that's been suggested to use separate intermediate CAs for issuing user and machine certificates. When configuring the certificate profile, only configure the intermediate CA that signed the machine certificates and then the user certs won't match and therefore will keep the prompts suppressed. Testing currently in progress for this. Will report back
- 11763 Views
- 8 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Global Protect Portal / Clientless VPN does not recognize SAML username after update to 10.1.14-h20 in GlobalProtect Discussions
- Global Protect Connectivity Issue in GlobalProtect Discussions
- Global Protect, same IP pool with 2 gateways on a firewall in GlobalProtect Discussions
- PA Global Protect in GlobalProtect Discussions
- How to Patch Vulnerability - Plugin 43160 (CGI Generic SQL Injection) on GlobalProtect in Next-Generation Firewall Discussions