- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Global protect saml using custome port number
- LIVEcommunity
- Discussions
- Network Security
- GlobalProtect Discussions
- Re: Global protect saml using custome port number
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Global protect saml using custome port number
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-07-2023 09:51 AM
we have configure the global products saml authentication with 443 in azure AD but we need to configure with the custom port number 1194 is it possible
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-20-2024 07:20 AM - edited 02-20-2024 07:25 AM
we encountered the same diffculty while trying to configure the GP port with a custom port number.
what do we need to configure under every section if we want to use a custom port like '10443'?
do i need to put ":10443" after the "test" and before the"/"?
and if so do i need to do that under every section?
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-20-2024 09:00 AM
After authentication, packets from Azure's SAML requests are restricted to pass through Palo Alto firewalls only on port 443. If you require a custom port, you'll need to create two NAT policies: one for port 443 and another for the custom port.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-20-2024 09:16 AM
Hi @n.major ,
The MS doc for GP/Azure is missing the port numbers. The PANW doc includes the port numbers (scroll down in red). https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g0000008U48CAE
The doc also answers your question. Where do I put the port numbers and on which URLs?
Thanks,
Tom
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-20-2024 09:22 AM
if i remember correctly i've configured it that way.
but as per what you say i dont need to change the SAML links on the palo alto firewall side, but i need to add a configuration of a
source NAT and Destination NAT?
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-20-2024 09:24 AM
thank you for your reply!
but in this link of KB that you sent me it is talked about as a 'regular' port and not a custom port.
i have managed to make it work as expected with port number 443 (with integration to SAML).
but when im changing it to a custom port on the GP-portal conf and on the azure side i get an error message.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-20-2024 09:28 AM
Hi @n.major ,
That is what @vasanth0611 said. I haven't looked into changing the port on the PANW side, but you can use NAT to do it.
Create an outbound destination NAT rule to change the port from 443 to 10443, and it should work.
Thanks,
Tom
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-20-2024 09:39 AM - edited 02-20-2024 09:42 AM
maybe i wasn't so clear.
when putting the url of the portal in the webbrowser i get the correct result and i am getting a redirect to the SAML.
on the SAML i get pass the credential part and get a 2FA which i approve.
than my screen is getting loaded, and i get an error message.
"AADSTS700016: Application with identifier 'https://test.com:443/SAML20/SP' was not found in the directory 'test.test'. This can happen if the application has not been installed by the administrator of the tenant or consented to by any user in the tenant. You may have sent your authentication request to the wrong tenant"
if you look carefully on the error you can see that it specify port number 443 and not 10443, so my feeling is that there is something wrong in the communication between the pafw and azure's SAML on the last handshake.
so the network side of the configuration seems to work fine.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-22-2024 06:37 AM
Hi @n.major ,
Thank you. It may be best if we build a ladder diagram of the communication between the NGFW and Azure.
- NGFW initiates connection to Azure on tcp/1194.
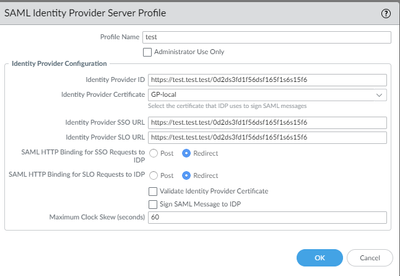
- Put the port number in the SAML Server Profile after the domain name and before the 1st / for all 3 URLs (not tested)
- Or change the destination port with outbound NAT.
- Configure Azure to listen on that port.
- Azure replies in the same TCP session.
- Azure also authenticates to the public interface of the NGFW.
- GP listens on tcp/443.
- The ports in the URL I listed should be ":443" configured on the Azure side.
Hi @vasanth0611 , Did you get this working?
Thanks,
Tom
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-22-2024 10:58 AM
Get to correct flow is this:
The user makes an authentication request to the equipment.
The equipment bounces and redirects the user to saml.
The user goes through an authentication and identification procedure with the SAML and receives a Token after successful authentication and identification.
With the identification token, the user returns to the equipment.
The equipment verifies the token against the cloud and allows access.
so by this flow and the scenario I’m in, the failure happens when the FW verifies the token against the cloud.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-19-2024 03:42 AM
I have the same problem, i think that the fw does not know how to return the authentication request to the changed port and only uses 443
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-21-2024 04:09 AM
i have not find any solution.
im doing it with the basic 443 port number when using SAML, so if you find a solution please @ me.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-17-2024 02:41 AM
Hi Vasanth0611,
I recently encountered this problem, but I don't quite understand the two NAT strategies you mentioned. Could you please explain it in more detail?
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-25-2025 01:51 AM
Hello everyone,
Did you manage to find a solution for custom port for the SAML Auth?
I am dealing with the same issue here with the error AADSTS700016.
Security Engineer
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-25-2025 08:56 AM - edited 02-25-2025 08:59 AM
Hi all,
I don't think either my ladder diagram or @n.major's is correct. I use Azure MFA for GP, and I see nothing under Monitor > Logs > Traffic between the outside interface and Azure. Because of the URLs configured in Azure, I assumed there was some communication between the two. Right now, it looks like all the communication to Azure is from the GP client. It looks like the GP client sends the identifier 'https://test.com:443/SAML20/SP' to Azure. A packet capture on the PC interface would confirm. If that traffic does not go to or through the NGFW, we cannot use NAT to change the port.
Maybe we cannot solve this issue, but if anyone wants to do a packet capture on the PC and post the actual ladder diagram of the traffic, that would be very helpful.
Thanks,
Tom
- 7509 Views
- 15 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- GP and auth fails in GlobalProtect Discussions
- I am attempting to login to the Customer Support portal to download a Global Protect Linux GUI package, but getting an error. in GlobalProtect Discussions
- Global Protect Embargo Rules in GlobalProtect Discussions
- ZTP Update on 1st Connect Fails with no Threat Protection License in Panorama Discussions
- Global Protect Custom Setup in Next-Generation Firewall Discussions