- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
PenTest GlobalProtect Subnet
- LIVEcommunity
- Discussions
- Network Security
- GlobalProtect Discussions
- Re: PenTest GlobalProtect Subnet
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
PenTest GlobalProtect Subnet
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-26-2023 06:26 AM
Hello,
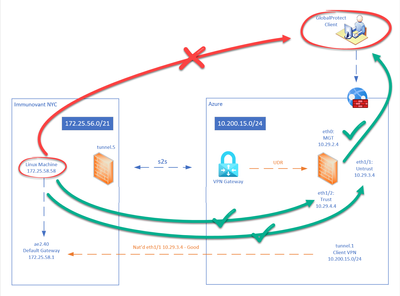
Our Palo GP is setup inside Azure - and it is working and serving its purpose. GP can reach everything, but not the other way around.
We can't ping GP Clients, we can't RDP to them, any traffic destined to GP Subnet has literally no logs at all.
Looking for some expert advice. Thanks in advance.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-26-2023 07:00 AM
Traffic log in 10.29.2.4 firewall shows pen tester traffic going to tunnel.1 towards GlobalProtect client?
If yes and you don't get any replies it means Windows firewall is dropping incoming traffic.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-26-2023 07:04 AM
Traffic log in 10.29.2.4 firewall shows pen tester traffic going to tunnel.1 towards GlobalProtect client?
If yes and you don't get any replies it means Windows firewall of the GlobalProtect client is dropping incoming traffic.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-27-2023 10:47 AM
Hello @popoymaster ,
Do you have a security rule allowing traffic to your GP zone?
If you do not see logs, it may be because you have not enabled logging on your interzone-default rule which drops all traffic not matched by any rules. Click on the interzone-default rule; click Override; select Log at Session End; and click Ok. Commit.
Thanks,
Tom
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-27-2023 10:09 PM - edited 05-27-2023 10:18 PM
This actually works! Traffic is dropped by the interzone-default rule.
Ok, so we have 2 palo alto firewalls;
1. On-prem with site-to-site tunnel to azure native vpn gateway
2. The other one is dedicated for GP.
Now, GP palo can reach the GP clients, thanks to you i allow interzone comms.
Problem now is, our on prem palo can reach all the interfaces Eth1 Untrust, Eth2 Trust of the GP FW but not the GP subnets. And this time, no logs at all.
Additionally, GP clients can reach the on-prem palo and subnets inside it.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-28-2023 06:38 AM
Hi @popoymaster ,
- Do you have a route on the on-prem NGFW to the GP subnet that points to the tunnel?
- Do you have a rule on the on-prem NGFW that allows traffic to the GP subnet?
- Do you have a rule on the Azure NGFW that allows traffic to GP for S2S VPN?
- What do the traffic logs show on the on-prem and Azure NGFWs for the pings that fail?
Thanks,
Tom
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-30-2023 08:34 AM
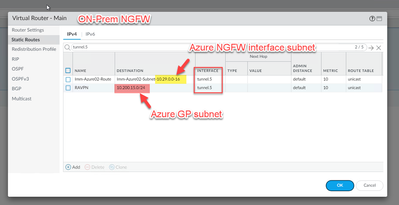
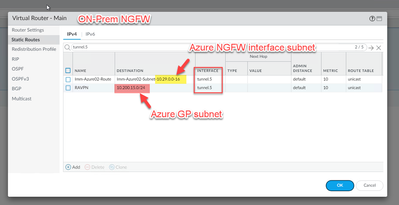
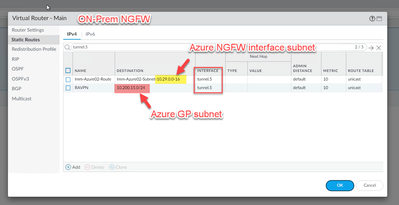
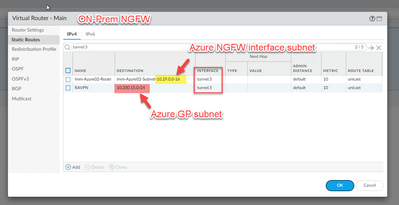
- YES! Azure NGFW's management and GP subnets are pointing to tunnel.
[cid:image001.png@01D992EA.9FD5C5D0]
Do you have a rule on the on-prem NGFW that allows traffic to the GP subnet?
- YES! Bi-directional.
Do you have a rule on the Azure NGFW that allows traffic to GP for S2S VPN?
- On-prem NGFW tunnels with Azure Native VPN Gateway. I enabled the intra and interzone loggs - this should capture anything not matched right?
What do the traffic logs show on the on-prem and Azure NGFWs for the pings that fail?
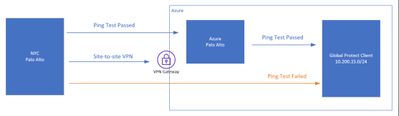
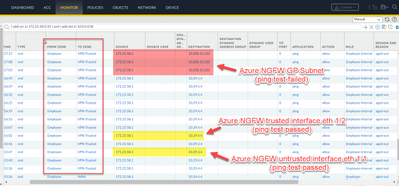
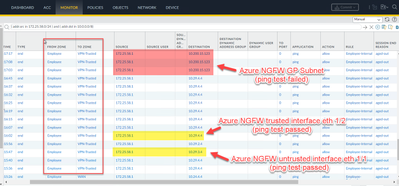
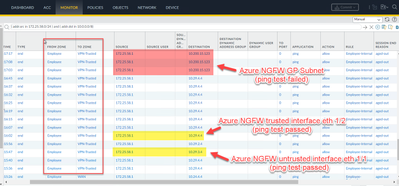
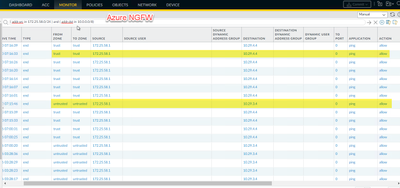
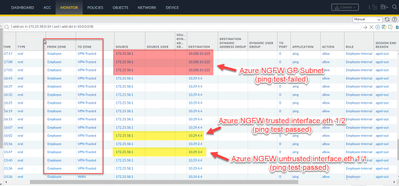
- I can see the traffic going out of On-prem NGFW but not arriving at Azure NGFW. Ping test to interfaces logged and worked but not to the GP Subnet.
[cid:image002.png@01D992EA.9FD5C5D0]
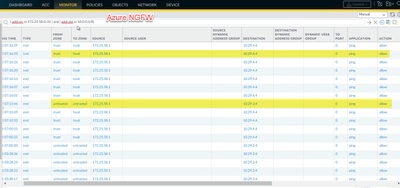
Azure NGFW only sees traffic going to the interfaces, but not destined to GP subnet.
[cid:image003.png@01D992EA.9FD5C5D0]
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-30-2023 08:37 AM
Do you have a route on the on-prem NGFW to the GP subnet that points to the tunnel?
- YES! Azure NGFW’s management and GP subnets are pointing to tunnel.
Do you have a rule on the on-prem NGFW that allows traffic to the GP subnet?
- YES! Bi-directional.
Do you have a rule on the Azure NGFW that allows traffic to GP for S2S VPN?
- On-prem NGFW tunnels with Azure Native VPN Gateway. I enabled the intra and interzone loggs – this should capture anything not matched right?
What do the traffic logs show on the on-prem and Azure NGFWs for the pings that fail?
- I can see the traffic going out of On-prem NGFW but not arriving at Azure NGFW. Ping test to interfaces logged and worked but not to the GP Subnet.
Azure NGFW only sees traffic going to the interfaces, but not destined to GP subnet.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-30-2023 08:48 AM
PING from Azure NGFW works but not from the Onprem NGFW.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-30-2023 08:50 AM
Hi Tom,
Do you have a route on the on-prem NGFW to the GP subnet that points to the tunnel?
- YES! Azure NGFW’s management and GP subnets are pointing to tunnel.
Do you have a rule on the on-prem NGFW that allows traffic to the GP subnet?
- YES! Bi-directional.
Do you have a rule on the Azure NGFW that allows traffic to GP for S2S VPN?
- On-prem NGFW tunnels with Azure Native VPN Gateway. I enabled the intra and interzone loggs – this should capture anything not matched right?
What do the traffic logs show on the on-prem and Azure NGFWs for the pings that fail?
- I can see the traffic going out of On-prem NGFW but not arriving at Azure NGFW. Ping test to interfaces logged and worked but not to the GP Subnet.
Azure NGFW only sees traffic going to the interfaces, but not destined to GP subnet.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-30-2023 08:51 AM
Hi Tom,
Do you have a route on the on-prem NGFW to the GP subnet that points to the tunnel?
- YES! Azure NGFW’s management and GP subnets are pointing to tunnel.
Do you have a rule on the on-prem NGFW that allows traffic to the GP subnet?
- YES! Bi-directional.
Do you have a rule on the Azure NGFW that allows traffic to GP for S2S VPN?
- On-prem NGFW tunnels with Azure Native VPN Gateway. I enabled the intra and interzone loggs – this should capture anything not matched right?
What do the traffic logs show on the on-prem and Azure NGFWs for the pings that fail?
- I can see the traffic going out of On-prem NGFW but not arriving at Azure NGFW. Ping test to interfaces logged and worked but not to the GP Subnet.
Azure NGFW only sees traffic going to the interfaces, but not destined to GP subnet.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-30-2023 08:54 AM
Do you have a route on the on-prem NGFW to the GP subnet that points to the tunnel?
- YES! Azure NGFW’s management and GP subnets are pointing to tunnel.
Do you have a rule on the on-prem NGFW that allows traffic to the GP subnet?
- YES! Bi-directional.
Do you have a rule on the Azure NGFW that allows traffic to GP for S2S VPN?
- On-prem NGFW tunnels with Azure Native VPN Gateway. I enabled the intra and interzone loggs – this should capture anything not matched right?
What do the traffic logs show on the on-prem and Azure NGFWs for the pings that fail?
- I can see the traffic going out of On-prem NGFW but not arriving at Azure NGFW. Ping test to interfaces logged and worked but not to the GP Subnet.
Azure NGFW only sees traffic going to the interfaces, but not destined to GP subnet.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-30-2023 08:55 AM
Do you have a route on the on-prem NGFW to the GP subnet that points to the tunnel?
- YES! Azure NGFW’s management and GP subnets are pointing to tunnel.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-30-2023 08:55 AM
Do you have a rule on the on-prem NGFW that allows traffic to the GP subnet?
- YES! Bi-directional.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-30-2023 08:55 AM
Do you have a rule on the Azure NGFW that allows traffic to GP for S2S VPN?
- On-prem NGFW tunnels with Azure Native VPN Gateway. I enabled the intra and interzone loggs – this should capture anything not matched right?
- 7727 Views
- 15 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- PA Global Protect in GlobalProtect Discussions
- Globalprotect VPN assign a public IP to an internal server in GlobalProtect Discussions
- SPlit tunneling issue on GlobalProtect in GlobalProtect Discussions
- GlobalProtect Prelogon in GlobalProtect Discussions
- Get a defined target IP Adress and Subnet via GlobalProtect (PA-460) in GlobalProtect Discussions