- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Is it possible to Query Prisma Cloud Compute for Alerts? I am not interested in Prisma Cloud Alerts.
- LIVEcommunity
- Discussions
- Cloud Native Application Protection
- Prisma Cloud Discussions
- Re: Is it possible to Query Prisma Cloud Compute for Alerts? I am not interested in Prisma Cloud Alerts.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-06-2022 02:14 PM
Is it possible to Query Prisma Cloud Compute for Alerts? I am not interested in Prisma Cloud Alerts.
If yes then, which API call?
I can't find it here... https://prisma.pan.dev/api/cloud/cwpp/
thunt@citrusoft.org
https://www.citrusoft.org
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-10-2022 06:09 AM
Hello, Compute doesn't have an API endpoint for alerts.
Compute is Stateless, so it does not have a list of active alerts that can be pulled down. In compute, alerts get pushed to integrations that are set up. We have alert profiles inside which we have alert providers, and we can configure the profiles to send a bunch of alert information related to compliance, vulnerabilities, WAAS, etc., to these alert providers.
We have separate API endpoints for vulnerabilities, compliance, WAAS, runtime, images, etc., that you can query.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-01-2022 12:34 PM
@CloudEngineer dude, you were correct the whole time. The Prisma Cloud Compute SecurityHub Alert Provider works perfectly fine.
I got misinformation from support case 02326773. Here is how I determined that the Registry Scanned CVEs and Compliance vulnerabilities were generating Alerts and propogating them to AWS SecurityHub/Findings Console. I entered this Filter criteria and then I could see the CVE-Alerts.
I still have NO explanation for those errors that I cited at the beginning of this
thunt@citrusoft.org
https://www.citrusoft.org
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-10-2022 06:09 AM
Hello, Compute doesn't have an API endpoint for alerts.
Compute is Stateless, so it does not have a list of active alerts that can be pulled down. In compute, alerts get pushed to integrations that are set up. We have alert profiles inside which we have alert providers, and we can configure the profiles to send a bunch of alert information related to compliance, vulnerabilities, WAAS, etc., to these alert providers.
We have separate API endpoints for vulnerabilities, compliance, WAAS, runtime, images, etc., that you can query.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-11-2022 06:46 AM
Thanks for your confirmation; ya know what is sad is that there does exist an Alert Provider for AWS SecurityHub but it does not forward/publish Alerts of CVEs as reported by scanners. Webhook Alert Provider is not an option since we want to minimize attack surface from the public internet. So, I can query the registries API for the vulnerabilities.
thunt@citrusoft.org
https://www.citrusoft.org
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-11-2022 11:02 AM
Hi Tommy,
I'd like to know what alerts you are looking for? While its true that there isn't a single consolidated alerts API endpoint for Compute, you can still use the relevant individual APIs to gather what you want which would ultimately match your configured rules and ultimately trigger an alert to be sent to a desired integration.
As for the AWS SecurityHub integration, could you please clarify what you mean "does not publish Alerts of CVEs as reported by scanners?" It will should forward your requested information as I understand it. I have seen the findings sent to SecurityHub so I'd be very interested in understanding more.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-12-2022 11:46 AM
Hi Brandon,
In support CASE 02326773, I asked...
"However, I cannot find the Alerts that should have been generated by Prisma CloudCompute Console/Defend/Vulnerabilities/Images/CI/Rules...
...
It appears that the CVEs did trigger Alert creation because now the Alert provider, AWSSecurityHub, is reporting this error...
failed to add findings: [{ ErrorCode: "InvalidInput", ErrorMessage: "Finding does not adhere to Amazon Finding Format. data.Resources[0].Id should NOT be shorter than 1 characters, data.Resources[0].Id should NOT be shorter than 12 characters, data.Resources[0].Id should match pattern \"^arn:(aws|aws-cn|aws-us-gov):[A-Za-z0-9\\-]{1,63}:[a-z0-9\\-]*:([0-9]{12})?:.+$\", data.Resources[0].Id should match some schema in anyOf.", Id: "us-west-2/twistlock/vulnerabilities/" }]...
2. What the heck is wrong with the integration to Alert provider, AWSSecurityHub? remember that Test Alerts and runtime Alerts are sent successfully."
Support's response is this...
"Hello Tommy,
Thank you for allowing me time to review the case.
Based on our documentation, we have an existing issue, PCSUP 9241, and it is expected to be fixed in Lagrange release.
Here is the link to the documentation for known issue in Prisma Cloud Compute:
https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-release-notes/prisma-cloud-comput...
Please let me know if you have any further questions."
If you saw Alerts from twistlock scans of registries or images in the pipeline then can you show that to Umer Sheikh cause he thinks that its a known issue and although AlertProvider, AWSSecurityHub, is working, we see no Alerts in SecurityHub related to registry scans with reported CVEs.
thunt@citrusoft.org
https://www.citrusoft.org
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-12-2022 01:17 PM
Hi Tommy,
I've read through the PCSUP and I can summarize that if you are trying to send Compute's findings to an AWS Gov account then we are expecting a fix in the next major release (Lagrange) which may resolve the errors observed from AWS.
If you are working on integrating with Security Hub in a typical commercial account then we can probably get this going with some additional configuration checks and testing since I have seen this integration work successfully.
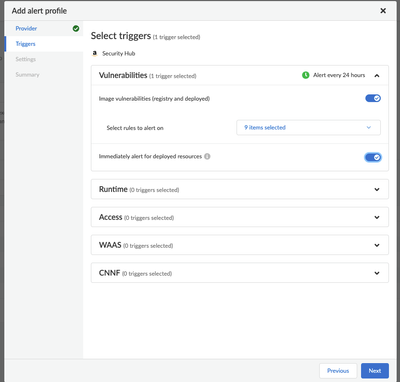
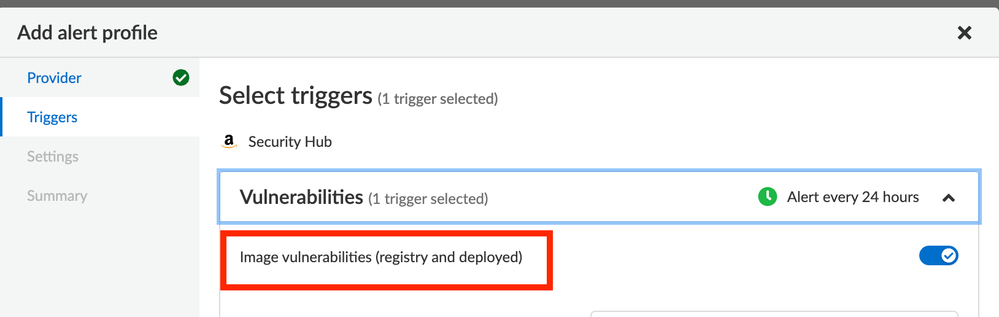
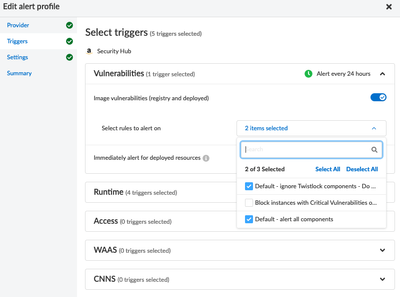
However, I noticed that your request mentioned alerts generated by CI rules. At this time, the Security Hub integration doesn't have an option to send CI alerts to Security Hub. Please have a look at this screenshot where I've shown that only Deployed and Registry scan results are available for Vulnerability Management:
You'll see within "select rules to alert on" that only your Deployed / Registry rules are available to select.
We also support sending findings for Runtime, Access, WAAS and CNNF.
Lastly, can you please confirm if you are using the self-hosted Compute console or Prisma Cloud Enterprise Edition (SaaS) ? I know you mentioned "Prisma Cloud Compute" which is generally our identification of the self-hosted product but I always like to be sure especially since that will change some of the authentication options.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-13-2022 07:18 AM
Brandon, I am grateful for your help with this matter.
We are a commercial enterprise; we have nothing to do with AWS Gov and we have no AWS Gov accounts. I suspect that is the Prisma SaaS default behavior when the integration is only partially or mis configured. This gov issue isn't my request for help, however, it's an issue but would take me some time to recreate the configuration to trigger that behavior in the SaaS product. So much to do, I prefer not to spend any time on this.
My issue is very detailed...
No one is saying that the integration doesn't work, I assert that THE INTEGRATION WORKS but only partially. You are saying that you've seen these VERY specific kinds of alerts that I report create errors; just seeing some/any Alerts being transferred to SecurityHub is insufficient evidence that my issue is to be dismissed.
Let me describe it again because the support comments are scrambled eggs...
PCC SaaS Alerts triggered by scans of ECS & Artifactory registries appear to NOT be Accepted by AWS due to this error being reported by Prisma's SecurityHub Alert provider...
failed to add findings: [{ ErrorCode: "InvalidInput", ErrorMessage: "Finding does not adhere to Amazon Finding Format. data.Resources[0].Id should NOT be shorter than 1 characters, data.Resources[0].Id should NOT be shorter than 12 characters, data.Resources[0].Id should match pattern \"^arn:(aws|aws-cn|aws-us-gov):[A-Za-z0-9\\-]{1,63}:[a-z0-9\\-]*:([0-9]{12})?:.+$\", data.Resources[0].Id should match some schema in anyOf.", Id: "us-west-2/twistlock/vulnerabilities/" }]
The support guy says that error is a known issue in the product but I'm hoping that you've seen registry scans CVE-Alerts propagated to SecurityHub. Webhooks are not an option, due to my firms' policies on exposing network endpoints to public ingress internet.
Our AlertProvider is configured to send registry vulnerabilities...
I incorrectly used the language "CI", because there are no equivalent "Fail/Report" rules for the Registry scans; whereas there are rules for "CI" and "Deployed" scans. Within the alert profile, I specified these "Deployed" rules be applied to Vulnerabilities; its not clear if these would have an effect on Registry Scans' CVE-Alerts.
Our intention is to use registries' scans to govern images on their path-to-production; we want to BLOCK images with CVEs of severity, CRITICAL and HIGH.
We use Prisma Cloud Enterprise Edition (SaaS). Because of the two kinds of Alerts in this product, I use PCC to distinguish the kind of Alert that I am speak of. Whew!
thunt@citrusoft.org
https://www.citrusoft.org
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-01-2022 12:34 PM
@CloudEngineer dude, you were correct the whole time. The Prisma Cloud Compute SecurityHub Alert Provider works perfectly fine.
I got misinformation from support case 02326773. Here is how I determined that the Registry Scanned CVEs and Compliance vulnerabilities were generating Alerts and propogating them to AWS SecurityHub/Findings Console. I entered this Filter criteria and then I could see the CVE-Alerts.
I still have NO explanation for those errors that I cited at the beginning of this
thunt@citrusoft.org
https://www.citrusoft.org
- 2 accepted solutions
- 5552 Views
- 7 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- PC Compute License information is missing in Prisma Cloud Discussions
- NuGet Serverless defender in Prisma Cloud Discussions
- Queries about serverless installation and registry scanning in Prisma Cloud Discussions
- Prisma Cloud Compute Container Defender- App Embedded Manually Installed Defenders not seeing in Prisma Cloud Discussions
- Prisma Cloud Compute Multi Tenancy and creating Project in Prisma Cloud Discussions