- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Credential Phishing Protection troubleshooting
- LIVEcommunity
- Discussions
- Cloud Delivered Security Services
- Threat & Vulnerability
- Re: Credential Phishing Protection troubleshooting
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Credential Phishing Protection troubleshooting
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-08-2018 08:45 AM
hey community -
tearing my hair out here...I've set up a RoDC in my environment and added a test group to the allowed password replication group. I've configured the user and credential agents on the RoDC and they say connected to my firewall, and also successfully connect to the other dcs. I can see my user to ip mapping for my test account. On the firewall I've created a User ID agent that shows connected as well.
however, show user credential-filter statistics shows zero entries, I'm also seeing this in the user id logs:
UIA CredentialChecking error: credential enabled but no digest.
What am I missing here? thanks for any advice!!
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-05-2019 07:42 AM
Hi Chacko42,
I should have replied here when I solved this particular issue. For the benefit of others (I don't think this is documented anywhere yet), the version of Credential & User-id agents have to be equal or less than the PAN-OS on the firewalls doing the checking.
thanks for pinging here and reminding me! 🙂
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-06-2019 01:34 AM
Hi, found your post and wondered if you could point me in the right direction.
Trying to implement this as well in our environment.
I have build a RODC and installed both programs
Running PAN-OS version 8.1.7
I am running into some problems though.
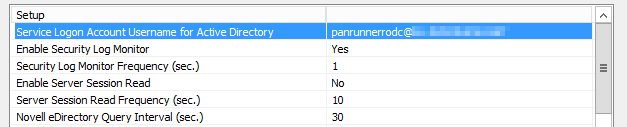
The User_ID agent runs as a service. At first via the Local System Account but if you configure it to run with a dedicated account it wants to run the service with this account
Although the account is configured to run-as-a-service in the default domain policy it throws in an error when you start the service.
I have used the following instructions to set this up
Are there any additional instructions that I need to follow to implement this correctly on a RODC (Server 2012R2)?
Remko
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-06-2019 01:38 PM
Hey Remko,
Have you tried walking down your version at all? I'm not running 8.1 at the edge just yet - and I'm wondering if there are bugs in the 8.1. versions? I'm running 8.0.10 right now for both agents - but I'm interested to know if its versioning since I'm headed to 8.1 on the border firewalls really soon.
let me know what you think?
Laura
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2019 12:25 AM
Hi Laura, thanks for your reply.
I have downgraded the client further to version 8.1.5-6.
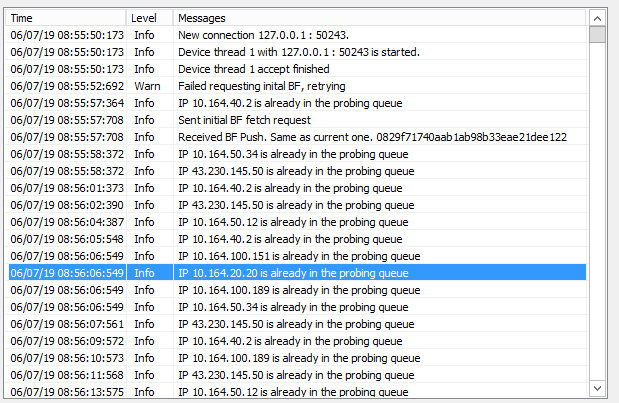
It appears to be working correctly as long as it runs with the local system account
In the log I see a whole bunch of entries appearing
When I edit the UserIdentification setup and save it, the service starts to run with the RODC_Service account.
This account has the correct priviledges according to this article
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClEuCAK
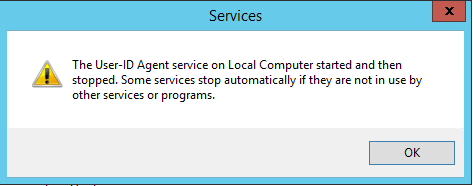
But but the service fails to start when started with this new account
06/04/19 11:19:03:448[Error 2382]: Start error -1!! 06/04/19 11:19:03:448[Error 764]: Device listening thread stops timeout! 06/04/19 11:19:45:694[ Info 2357]: ------------Service is being started------------ 06/04/19 11:19:45:694[ Info 2364]: Os version is 6.2.0. 06/04/19 11:19:45:694[Error 675]: Cannot open config reg log key with error 5(Access is denied.
As said, as long as it runs with the system account there are green lights though in the Palo Alto User_ID Agent screen so I will try if I can get a block page when entering corporate credentials.
Still a bit confused how all this works but let's give it a try 🙂
Remko
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2019 12:41 AM
Hmmm,
Can't seem to get this to work. Whatever I try, the Palo Alto does not detect any user credential submission. Tried various websites and categories to put the URL credential submission to block.
But unfortunately, no luck whatsoever.
I think I am going to put this aside for a while and try some other time.
This is causing to much frustration 🙂
Remko
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2019 12:43 AM
@Indorama_Ventures Can you see any blob filters if you have a look on the statistics of the User ID agent on firewall CLI?
Chacko
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2019 12:49 AM
@Chacko42 : Thanks for your reply. How would you check this via the commandline? I did a quick Google Search but was not able to find this. Can you advise?
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2019 12:53 AM
show user user-id-agent state <your RODC agent>
There you shood see hits at
num of bloomfilter requests sent :
num of bloomfilter response received :
In best case, the errors are low or non-existing
Chacko
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2019 01:51 AM
Thanks, I do see a couple of bloomfilter entries appear
num of bloomfilter requests sent : 13
num of bloomfilter response received : 12
num of bloomfilter response failed to proc : 0
num of bloomfilter resize requests sent : 0
Last heard(seconds ago) : 4So I guess we are on the right track ?
I put "domain users" in the "Allowed RODC Password Replication Group"
But also my personal testing account in the case there might be a problem with nested groups.
Then I tried two different URL categories for the password credential submission
One for my personal NAS device (computers-and-internet-info) at home and one for NetFlix (streaming-media)
But if I enter any domain credentials, they are not detected.
Both websites simply say the credentials are not valid.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2019 01:56 AM - edited 06-07-2019 01:57 AM
Okay, you're on the right track.
You also got a "Denied RODC Password Replication Group" which will exclude users - so maybe that is the reason, why there are so less entries (1 bloom filter equals 1 credential) - I guess you can trigger the RODC credential sync with windows tools - you need to google that.
Regarding the "any credentials" - if you use the credential agent, the credentials are only detected, if you're web session is related to the according user.
If bob is mapped to ip 1.1.1.1 and bob logs in with alice credentials, nothing will happen.
If bob is mapped to ip 1.1.1.1 and bob logs in with his own credentials (doesn't matter which user name) - the credentials will be detected.
edit: and of course you need ssl decryption - otherwise you are unable to see the credential transmissions
Chacko
- 16446 Views
- 11 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!