- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
threat generic:5llion.com generic:conti.news
- LIVEcommunity
- Discussions
- Cloud Delivered Security Services
- Threat & Vulnerability
- Re: threat generic:5llion.com generic:conti.news
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-07-2021 03:05 AM
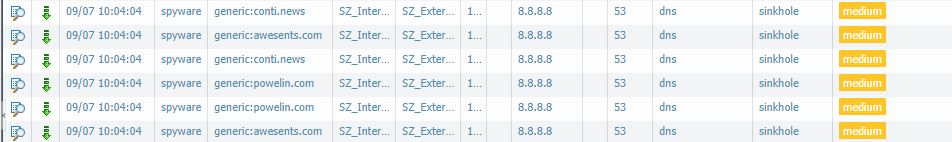
How to block this “unknown“ event to the customer that contains the threat generic:5llion.com (408607164). Because this threat is categorized as DNS Signature, the event had the destination port 53
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-07-2021 03:53 PM
Hi @NavidAlam thank you for posting question.
Do you need to change action specifically for DNS Threat ID: 408607164 to action block? When it comes to DNS signatures the action is set for all signatures under Anti-Spyware Profile > DNS Signatures > Policies & Settings. The option for Exceptions per signature bases is only for excluding signature from enforcement. There is no other configuration option to change action based on signature. Based on screen shot you have provided, the action is already: sinkhole. I think in this case there is no action needed as this has been forged with sinkhole IP address. Have you configured a rule to block: sinkhole.paloaltonetworks.com ?
Kind Regards
Pavel
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-07-2021 06:44 PM
Hello @NavidAlam
The final action for the DNS query is blocked as the action is a sinkhole. That means when a device will try to resolve the IP address for the known bad site, a sinkhole address ( dead end) is provided.
That way you can identify if which device is trying to reach a bad site, and the connection is never successful.
Sinkhole and block are parallel actions, not in sequence.
I hope this helps.
Himani
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-07-2021 03:53 PM
Hi @NavidAlam thank you for posting question.
Do you need to change action specifically for DNS Threat ID: 408607164 to action block? When it comes to DNS signatures the action is set for all signatures under Anti-Spyware Profile > DNS Signatures > Policies & Settings. The option for Exceptions per signature bases is only for excluding signature from enforcement. There is no other configuration option to change action based on signature. Based on screen shot you have provided, the action is already: sinkhole. I think in this case there is no action needed as this has been forged with sinkhole IP address. Have you configured a rule to block: sinkhole.paloaltonetworks.com ?
Kind Regards
Pavel
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-07-2021 06:44 PM
Hello @NavidAlam
The final action for the DNS query is blocked as the action is a sinkhole. That means when a device will try to resolve the IP address for the known bad site, a sinkhole address ( dead end) is provided.
That way you can identify if which device is trying to reach a bad site, and the connection is never successful.
Sinkhole and block are parallel actions, not in sequence.
I hope this helps.
Himani
- 2 accepted solutions
- 3315 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- TID 95187 is not on my signature list in Threat & Vulnerability Discussions
- False Positive: virus/win32.wGeneric.efbuyk in Threat & Vulnerability Discussions
- About Virus/Win32.WGeneric.eevxic in Threat & Vulnerability Discussions
- AGCInvokerUtility.exe - PA picking it up as Virus in Threat & Vulnerability Discussions
- Are there signature release for CVE-2023-6237 etc? in Threat & Vulnerability Discussions