- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Site to Site VPN config on Azure palo lato
- LIVEcommunity
- Discussions
- Network Security
- VM-Series in the Public Cloud
- Re: Site to Site VPN config on Azure palo lato
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Site to Site VPN config on Azure palo lato
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-11-2017 12:01 AM
Hi All,
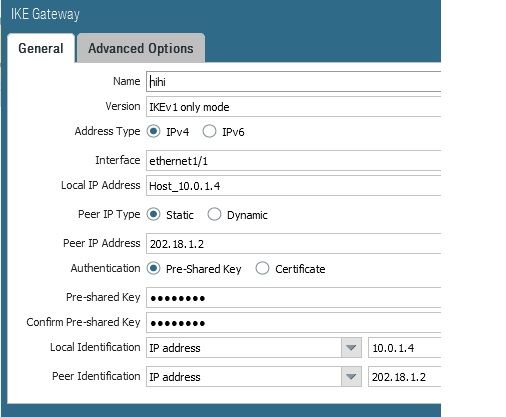
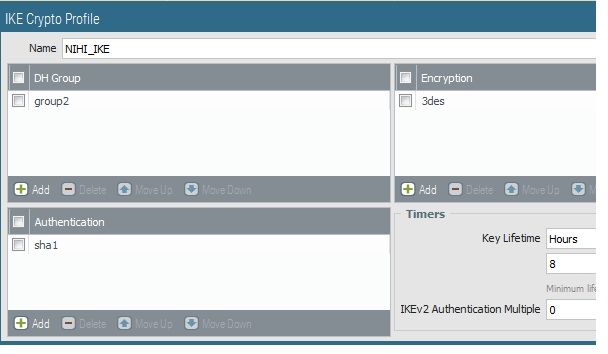
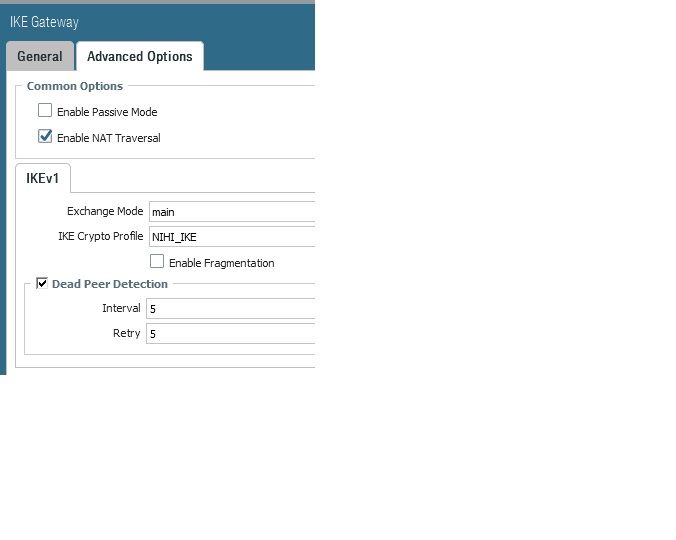
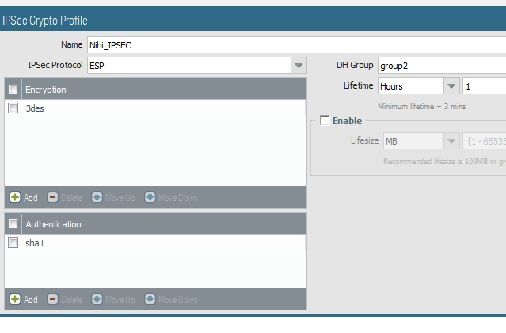
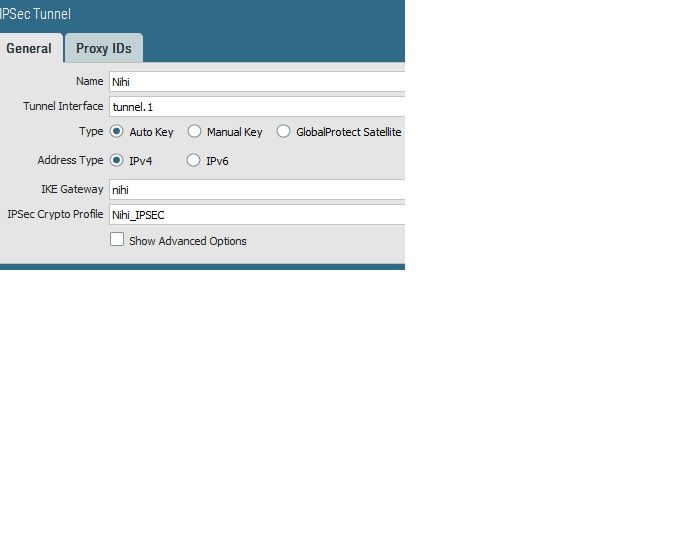
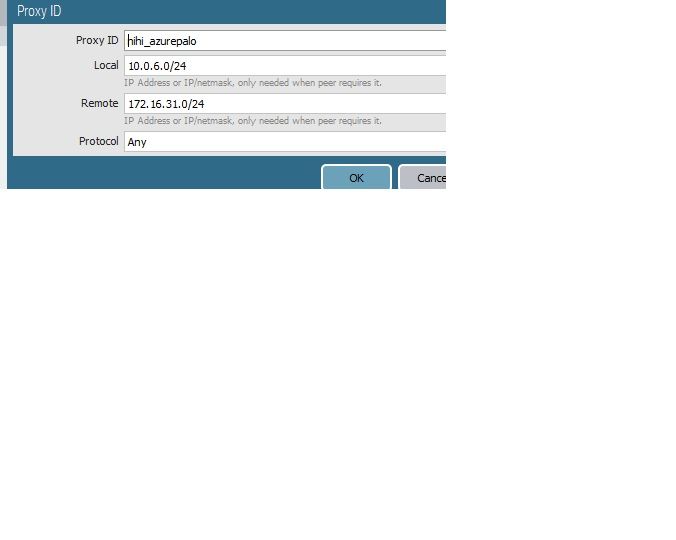
I have created site to site VPN between Palo alto in azure and checkpoint firewall.
Created VPN on untrust interface (Public IP is mapped on that interface ) . Even the Phase 1 is not up.
Can anyone help me with config on azure palo alto
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-26-2017 07:26 AM
Thanks for your reply.
Is it ok If i upload the screenshoot of the config
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-26-2017 08:36 AM
Amaresh,
Sure. I will take a look when I can.
Thank you,
Todd
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-29-2017 02:36 AM
Also configured routes and policies .
Note - The interface is mapped with Public IP on azure.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-29-2017 06:20 AM
What do your logs say? Have you run a debug on the ike yet? If you are trying the connection take a look at the mp-log ikemgr.log and look at the messages. Watching that will give you a good indication where the issue might be.
Are you able to ping the public IP peer on the remote side? I would also go over your ike/ipsec settings from the vendor and make sure you are matched up.
Todd
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-02-2017 04:55 AM
look at the system logs and filter with (subtype eq vpn) .If you seel messages saying failing due to negotiation timeout then take a packet capture on palo alto and checkpoint to check if you are sending/receiving isakmp packets
Run a test vpn ike-sa gateway <gateway> and have a look at mp-log ikemgr.log for more info
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-04-2017 01:31 AM
Is there any docs available for the config of site to site VPN/Remote access VPN in azure palo alto .
Note - I do have docs related to appliance box.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-04-2017 09:17 AM
Amaresh:
If you are using the Azure VPN gateway, try this KB article:
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-10-2017 02:34 AM
I am looking for the docs for vpn configure in Plao alto which is deployed in azure/amazon environment.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-10-2018 04:49 AM
have you managed to get this working ?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-27-2020 01:51 PM
Unfortunately, the article doesn’t offer any help on how to configure the Azure side, it only suggests to read a Microsoft article that is very generic.
Please, give us a howto document with examples for both sides; otherwise, it is worthless.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-27-2020 02:33 PM
In our reference architecture and companion deployment guide, we do not typically recommend terminating the VPNs on the Virtual Appliance running in Azure. This is b/c you will need to use SNAT to enforce return path routing through the proper firewall to prevent asymmetric routing as we cannot extend BGP from the firewalls to the Azure Route Table. Instead, you may consider terminating the VPN on the Azure VPN Gateway and use our backhaul routing design to force all traffic to and from the Gateway subnet through the firewall utilizing UDRs and the Load Balancer.
https://www.paloaltonetworks.com/resources/reference-architectures/azure
- 15949 Views
- 15 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Panorama managed - Global protect SAML cert renew - IDP xml import wrong expiry in GlobalProtect Discussions
- Azure Virtual Desktops integration with Global Protect nightmare in GlobalProtect Discussions
- How to Fully Back Up Panorama VM in Azure in Panorama Discussions
- Process to Rebuild Panorama with Prisma Access & Prisma SDWAN in Panorama Discussions
- PAN-OS Upgrade / Downgrade procedure in VM-Series in the Public Cloud