- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Captive portal leak
- LIVEcommunity
- Discussions
- General Topics
- Captive portal leak
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-27-2014 02:59 AM
Hi everyone,
recently I configured CP but have problem with skype, which running without CP web authentication. I understand that sec policy take in place first and redirect session to CP for authentication (in my case have policy to permit any to any), but Skype running regardless of CP authentication and bypassing that flow. In CP policy I change for services to be any, instead http and https, but that was helpless....
any suggestions will be appreciated...:-)
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-30-2014 03:47 AM
Hi Tician
You missed some settings, ie. known-user
My settings looks like:
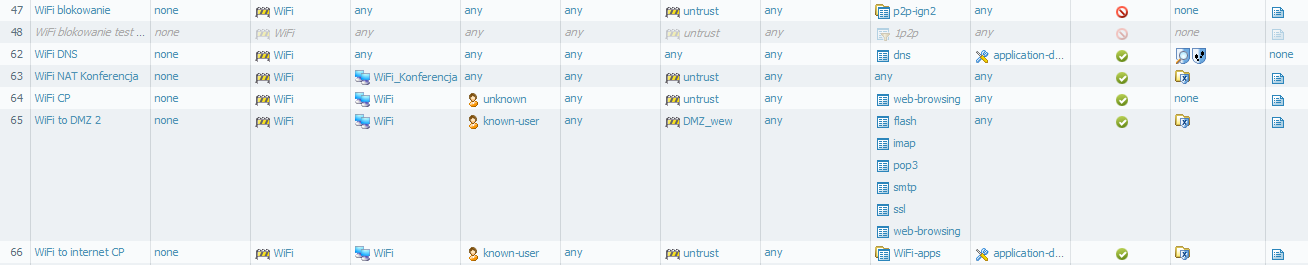
Please create rules 62 64 and 66 on Your device (of course with your network settings).
Rule 62 for DNS traffic, 64 is for browser redirection.
Regards
Slawek
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-28-2014 12:38 AM
Please whow us details of that session (from CLI show session id XXXX) and security policies from that zone to untrust.
Regards
Slawek
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-30-2014 02:15 AM
Hi,
this is the output of session's before making authentication on web captive portal:
show session id 52962 [K [K [K [K5838
[?1h = [44;1H [K
Session 55838
c2s flow:
source: 192.168.100.51 [Untrusted_WiFi]
dst: 92.51.156.98
proto: 6
sport: 60604 dport: 5938
state: ACTIVE type: FLOW
src user: unknown
dst user: unknown
pbf rule: Tunnel-cable_defaultroute 8
s2c flow:
source: 92.51.156.98 [UntrustGP_Cable]
dst: 192.168.100.51
proto: 6
sport: 5938 dport: 60604
state: ACTIVE type: FLOW
src user: unknown
dst user: unknown
start time : Fri May 30 10:41:00 2014
timeout : 3600 sec
time to live : 3560 sec
total byte count(c2s) : 4147
total byte count(s2c) : 4446
layer7 packet count(c2s) : 23
layer7 packet count(s2c) : 16
vsys : vsys1
application : teamviewer-base
rule : Untrusted_WiFi_Internet
session to be logged at end : True
session in session ager : True
session synced from HA peer : False
layer7 processing : enabled
URL filtering enabled : True
URL category : any
session via syn-cookies : False
session terminated on host : False
session traverses tunnel : False
captive portal session : False
ingress interface : vlan.1
[44;1H [K [7mlines 1-43 [27m [44;1H [44;1H [K egress interface : ethernet1/1.1
session QoS rule : N/A (class 4)
[44;1H [K [?1l >admin@PA-500> show session id 55838 [K [K [K [K [K1375
[?1h = [44;1H [K
Session 1375
c2s flow:
source: 192.168.100.51 [Untrusted_WiFi]
dst: 213.199.179.153
proto: 6
sport: 58809 dport: 40004
state: ACTIVE type: FLOW
src user: unknown
dst user: unknown
pbf rule: Tunnel-cable_defaultroute 8
s2c flow:
source: 213.199.179.153 [UntrustGP_Cable]
dst: 192.168.100.51
proto: 6
sport: 40004 dport: 58809
state: ACTIVE type: FLOW
src user: unknown
dst user: unknown
start time : Fri May 30 10:13:53 2014
timeout : 3600 sec
time to live : 1952 sec
total byte count(c2s) : 3928
total byte count(s2c) : 2186
layer7 packet count(c2s) : 23
layer7 packet count(s2c) : 29
vsys : vsys1
application : skype
rule : Untrusted_WiFi_Internet
session to be logged at end : True
session in session ager : True
session synced from HA peer : False
layer7 processing : completed
URL filtering enabled : False
session via syn-cookies : False
session terminated on host : False
session traverses tunnel : False
captive portal session : False
ingress interface : vlan.1
egress interface : ethernet1/1.1
[44;1H [K [7mlines 1-43 [27m [44;1H [44;1H [K session QoS rule : N/A (class 4)
session tracker stage l7proc : ctd err bypass
[44;1H [K [?1l >admin@PA-500> show session id 1375 [K [K [K [K8548
[?1h = [44;1H [K
Session 8548
c2s flow:
source: 192.168.100.51 [Untrusted_WiFi]
dst: 157.55.133.141
proto: 6
sport: 60580 dport: 12350
state: ACTIVE type: FLOW
src user: unknown
dst user: unknown
pbf rule: Tunnel-cable_defaultroute 8
s2c flow:
source: 157.55.133.141 [UntrustGP_Cable]
dst: 192.168.100.51
proto: 6
sport: 12350 dport: 60580
state: ACTIVE type: FLOW
src user: unknown
dst user: unknown
start time : Fri May 30 10:40:37 2014
timeout : 3600 sec
time to live : 3316 sec
total byte count(c2s) : 1383
total byte count(s2c) : 1214
layer7 packet count(c2s) : 10
layer7 packet count(s2c) : 11
vsys : vsys1
application : skype
rule : Untrusted_WiFi_Internet
session to be logged at end : True
session in session ager : True
session synced from HA peer : False
layer7 processing : completed
URL filtering enabled : False
session via syn-cookies : False
session terminated on host : False
session traverses tunnel : False
captive portal session : False
ingress interface : vlan.1
egress interface : ethernet1/1.1
[44;1H [K [7mlines 1-43 [27m [44;1H [44;1H [K session QoS rule : N/A (class 4)
session tracker stage l7proc : ctd err bypass
[44;1H [K [?1l >admin@PA-500> show session id 8548 [K [K [K [K65111
[?1h = [44;1H [K
Session 65111
c2s flow:
source: 192.168.100.51 [Untrusted_WiFi]
dst: 108.168.151.6
proto: 6
sport: 58818 dport: 80
state: ACTIVE type: FLOW
src user: unknown
dst user: unknown
pbf rule: Tunnel-cable_defaultroute 8
s2c flow:
source: 108.168.151.6 [UntrustGP_Cable]
dst: 192.168.100.51
proto: 6
sport: 80 dport: 58818
state: ACTIVE type: FLOW
src user: unknown
dst user: unknown
start time : Fri May 30 10:13:57 2014
timeout : 3600 sec
time to live : 2579 sec
total byte count(c2s) : 1078
total byte count(s2c) : 1501
layer7 packet count(c2s) : 5
layer7 packet count(s2c) : 20
vsys : vsys1
application : disqus
rule : Untrusted_WiFi_Internet
session to be logged at end : True
session in session ager : True
session synced from HA peer : False
layer7 processing : completed
URL filtering enabled : False
session via syn-cookies : False
session terminated on host : False
session traverses tunnel : False
captive portal session : False
ingress interface : vlan.1
egress interface : ethernet1/1.1
[44;1H [K [7mlines 1-43 [27m [44;1H [44;1H [K session QoS rule : N/A (class 4)
session tracker stage l7proc : ctd stop proc
[44;1H [K [?1l >admin@PA-500>
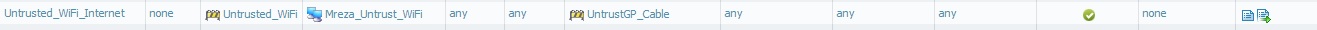
sec policy:
CP policy:
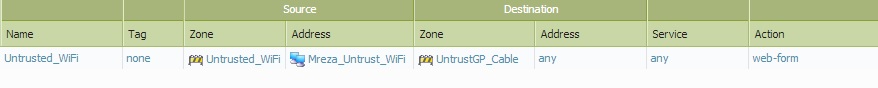
As you can see TeamViewer also working without authentication through CP...
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-30-2014 03:47 AM
Hi Tician
You missed some settings, ie. known-user
My settings looks like:

Please create rules 62 64 and 66 on Your device (of course with your network settings).
Rule 62 for DNS traffic, 64 is for browser redirection.
Regards
Slawek
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-30-2014 04:40 AM
Hi Slawek,
yes....![]() Great!, exactly that was missing in my configuration...now working as expected. Thank you very much!!!
Great!, exactly that was missing in my configuration...now working as expected. Thank you very much!!!
- 1 accepted solution
- 3732 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- GlobalProtect Always-On (6.3.3-c711) – Users Stuck in “Connecting” State but Still Have Internet Access in General Topics
- Windows Clients – Captive Portal Not Triggering with GlobalProtect Always-On Enabled in General Topics
- CIE for user/group mapping for firewall on-premise in General Topics
- High Data Plane Utilization During Business Hours in Next-Generation Firewall Discussions
- Android & iOS devices are bypassing the captive portal in Next-Generation Firewall Discussions



